A method for accessing shared resources in a distributed system and the distributed system
A technology of distributed systems and shared resources, applied in transmission systems, electrical components, etc., can solve the problem of high system risk and achieve the effect of reducing system security risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
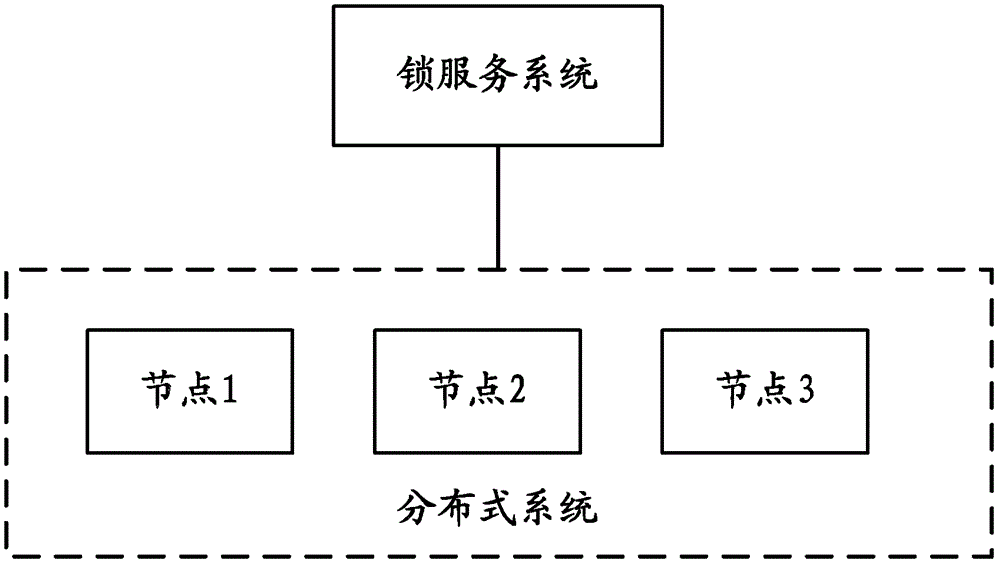
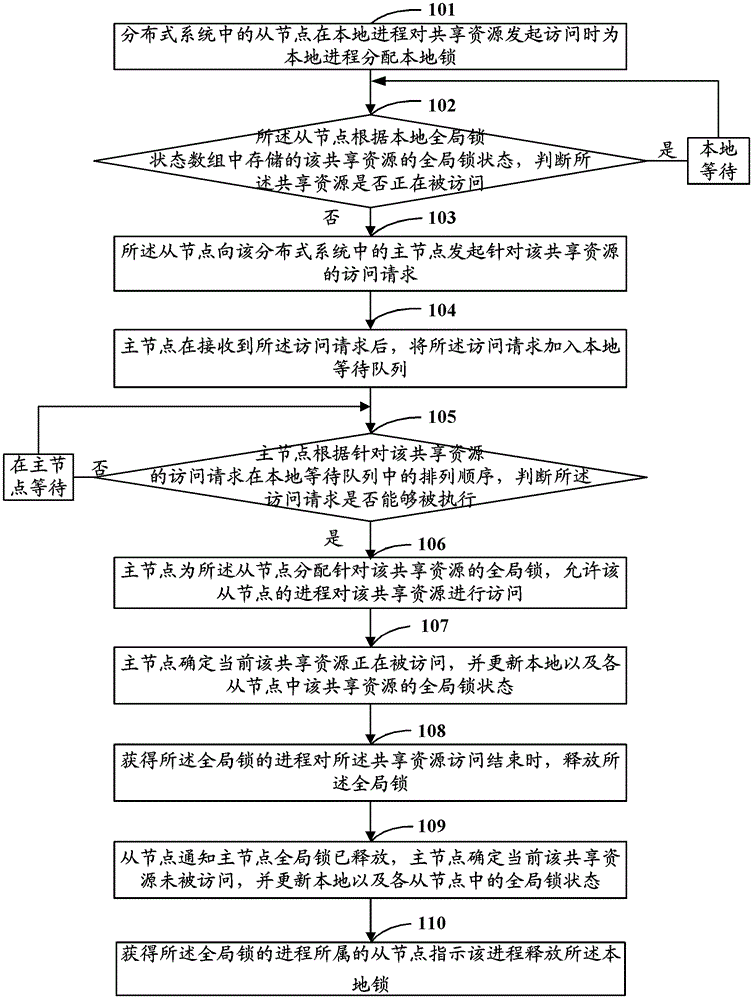
[0024] Embodiment 1 of the present application provides a method for accessing shared resources in a distributed system, and the method can be applied in a distributed system with multiple nodes. When the distributed system is running, a master node will be selected from each node, and other nodes will become slave nodes. The master node and the slave nodes can be connected through Transmission Control Protocol (Transmission Control Protocol, TCP) long connection or TCP short connection. way to keep in touch.
[0025] Specifically, the distributed system can implement the election of the master node and the consistency of data in the distributed system through algorithms such as Fast Paxos.
[0026] Preferably, each node in the distributed system has the same structure, including four structural components: a local lock, a global lock state array, a Log (log) record, and a waiting queue.
[0027] The local lock is the lock of the node itself, and each process in the node comp...
Embodiment 2
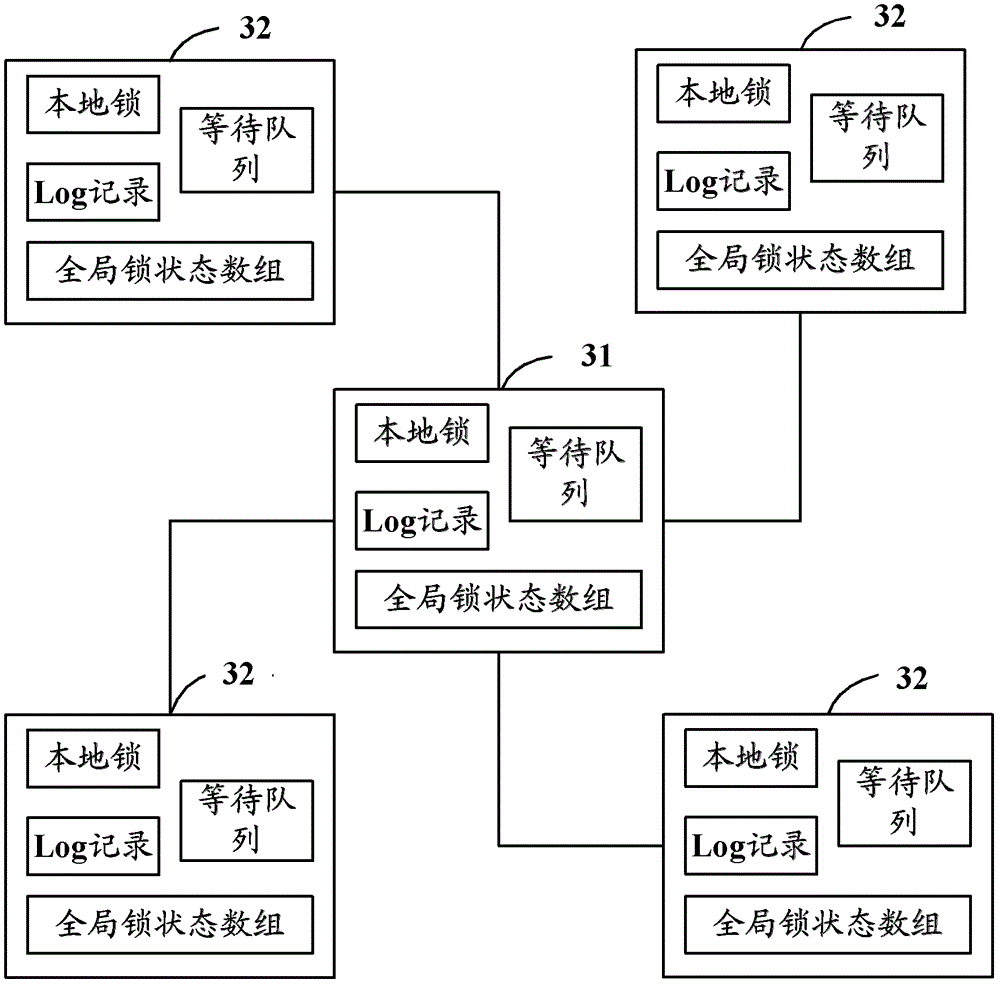
[0067] Such as image 3 As shown, it is a schematic structural diagram of a distributed system in Embodiment 2 of the present application. The distributed system includes a master node 31 and at least one slave node 32. Each node includes a local lock, a global lock state array, a Log record, and Waiting queues have four structural components.
[0068] Specifically, the distributed system can realize the election of the master node 31 and the consistency of data in the distributed system through algorithms such as Fast Paxos, and the mode of TCP long connection or TCP short connection between the master node 31 and the slave node 32 Keep in touch.
[0069] The slave node 32 is configured to judge whether the shared resource is being accessed according to the global lock state of the shared resource stored in the local global lock state array when the local process initiates access to the shared resource, and determine whether the shared resource is being accessed. When the sha...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com