Method and system for improving safety of voice communication of mobile terminal system based on safety micro secure digital (TF) card
A voice communication and mobile terminal technology, applied in wireless communication, transmission systems, security devices, etc., can solve the problems of illegal interception and eavesdropping of wireless channels, and achieve the effect of ensuring confidentiality and enhancing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] Embodiment 1, a method for enhancing the voice communication security of a mobile terminal system based on a secure TF card, characterized by:
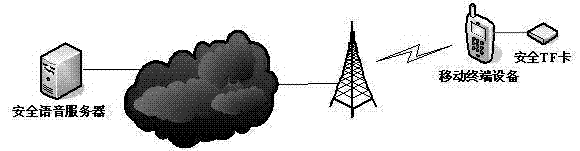
[0026] Step 1: Determine the session key used for voice data encryption and decryption through out-of-band methods, and directly generate the session key when issuing a secure TF card to the user and store it in the secure TF card;
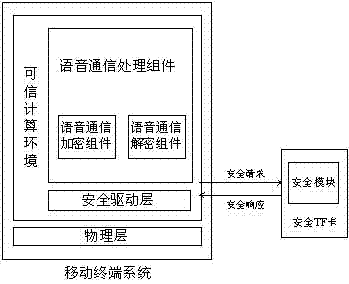
[0027] Step 2: When the voice communication is initiated, the voice communication content is sent to the voice communication server after the voice data stream is encrypted by the voice communication processing component of the mobile terminal using the session key to call the encryption component;
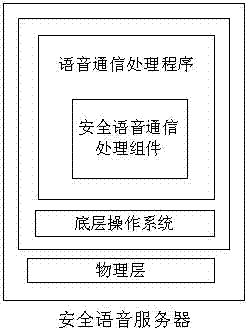
[0028] Step 3: After receiving the voice data stream sent by the mobile terminal, the voice communication server performs different processing according to the destination call address in the voice data stream.
Embodiment 2
[0029] Embodiment 2, a method for enhancing the voice communication security of a mobile terminal system based on a secure TF card, characterized by:
[0030] Step 1: Determine the session key used for voice data encryption and decryption through out-of-band means, and directly generate the session key when issuing a secure TF card to the user and store it in the secure TF card;
[0031] Step 2: When the voice communication is initiated, the voice communication content is sent to the voice communication server after the voice data stream is encrypted by the voice communication processing component of the mobile terminal using the session key to call the encryption component;
[0032] Step 3: After receiving the voice data stream sent by the mobile terminal, the voice communication server performs different processing according to the destination call address in the voice data stream.
[0033] Out of the need for effective management of keys, each mobile terminal system only retains the...
Embodiment 3
[0036] Embodiment 3, a method for enhancing the voice communication security of a mobile terminal system based on a secure TF card, characterized by:
[0037] Step 1: Determine the session key used for voice data encryption and decryption through out-of-band methods, and directly generate the session key when issuing a secure TF card to the user and store it in the secure TF card;
[0038] Step 2: When the voice communication is initiated, the voice communication content is sent to the voice communication server after the voice data stream is encrypted by the voice communication processing component of the mobile terminal using the session key to call the encryption component;
[0039] Step 3: After receiving the voice data stream sent by the mobile terminal, the voice communication server performs different processing according to the destination call address in the voice data stream.
[0040] Out of the need for effective management of keys, each mobile terminal system only retains t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com