Trusted software base providing active security service
A technology of active security and security service modules, applied in the field of trusted software base, can solve the problems of not providing confidentiality services, and not giving the implementation method of the operating system layer, so as to prevent unauthorized operations and ensure confidentiality and integrity sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
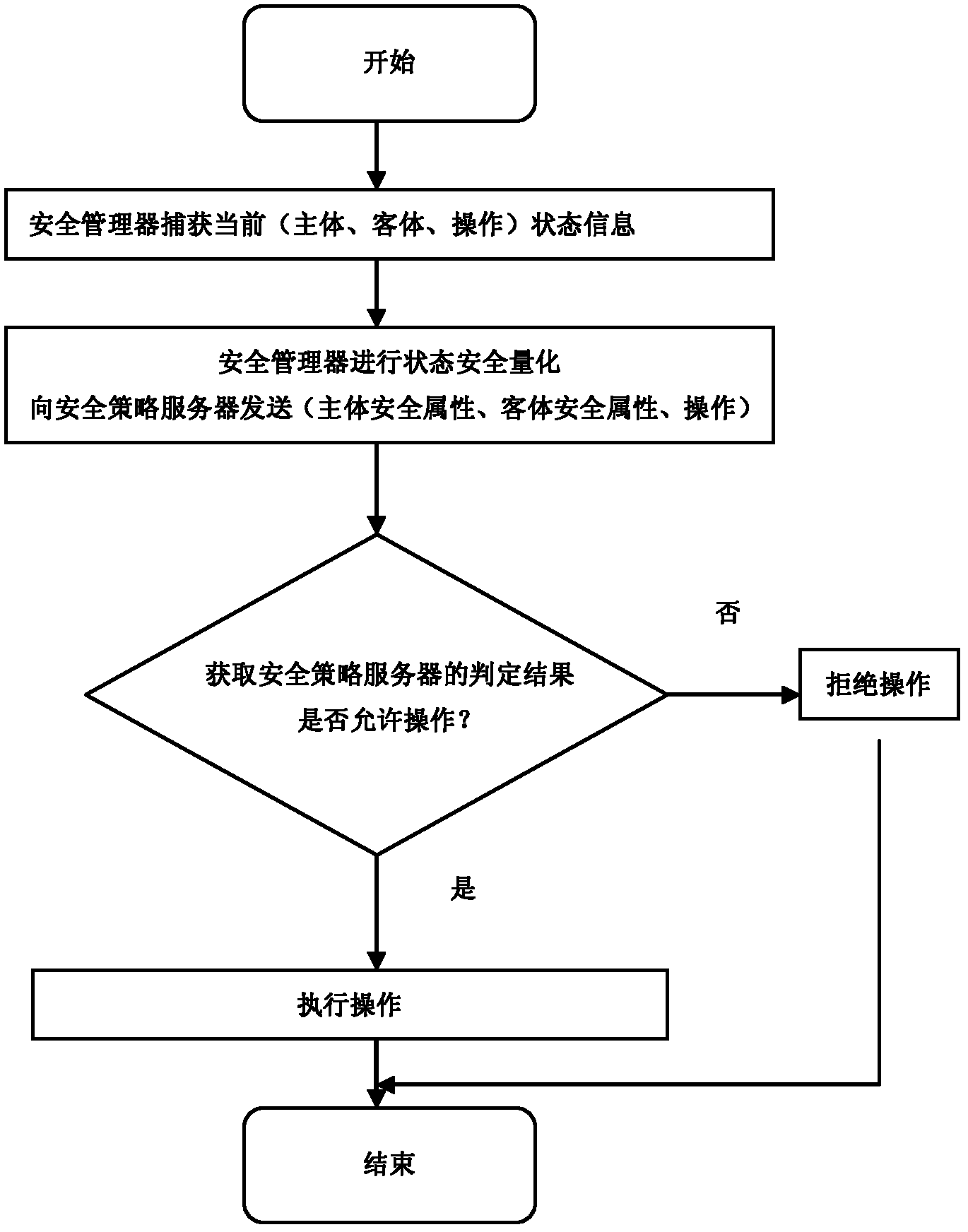
[0030] Below in conjunction with accompanying drawing of description, specific embodiment of the present invention is described:
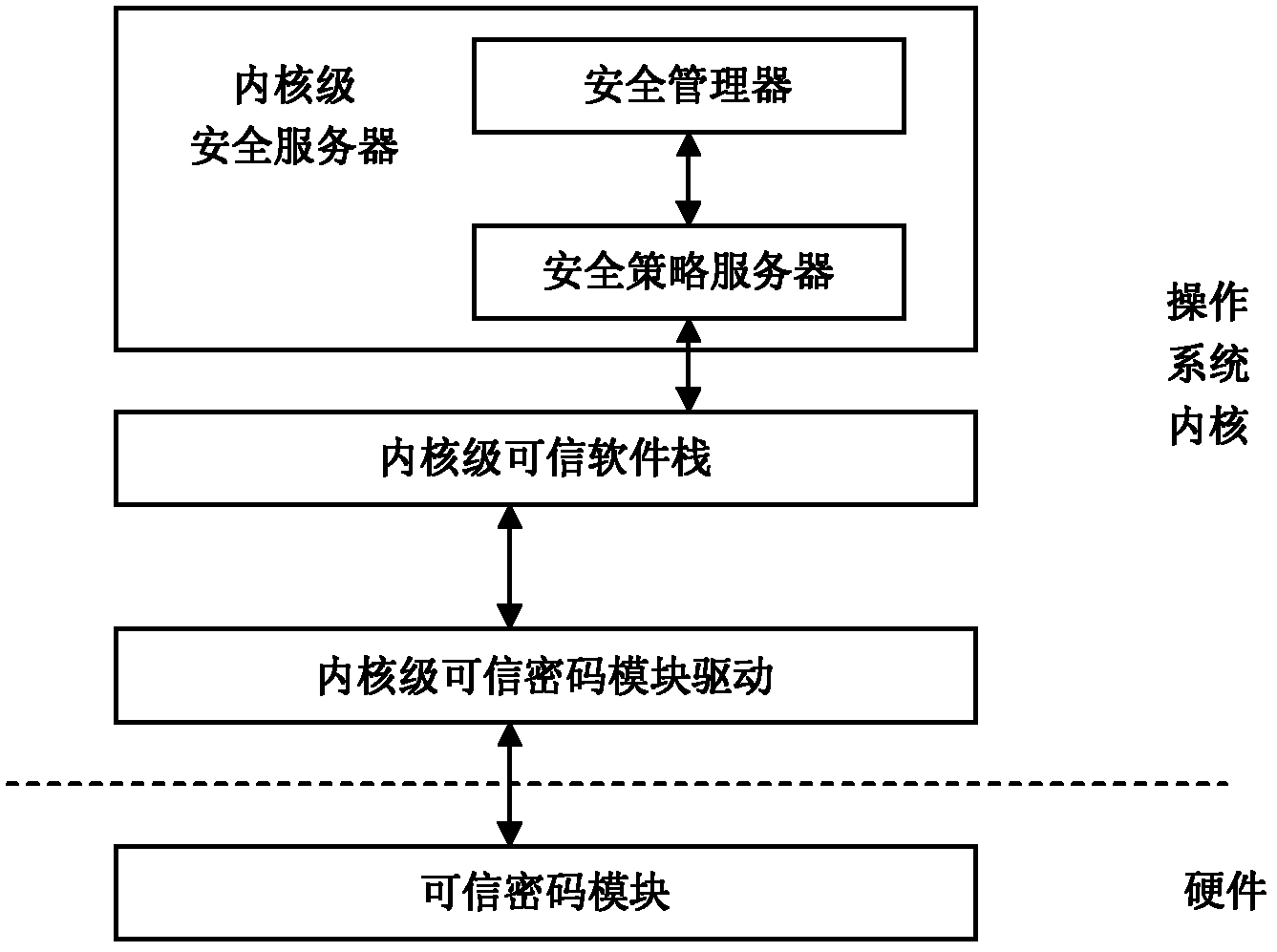
[0031] see figure 1 Shown is a schematic diagram of the trusted software base composition structure.
[0032] The trusted software base consists of a trusted cryptographic module, a kernel-level trusted cryptographic module driver, a kernel-level trusted software stack, and a kernel-level security service module. The kernel-level security service module is composed of a security policy server and a security manager.
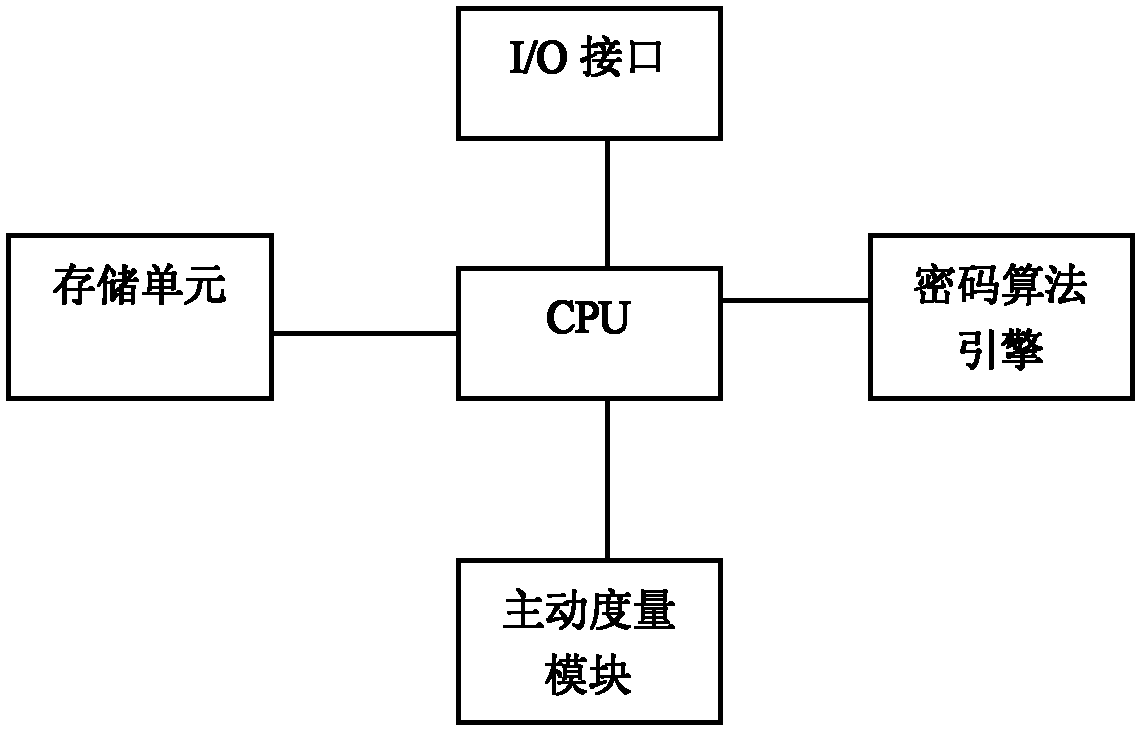
[0033] see figure 2 As shown in , it is a schematic diagram of the hardware composition of the trusted cryptographic module.
[0034] The trusted cryptographic module is embedded in the PC motherboard. It is an independent hardware entity, mainly composed of CPU, single storage unit, cryptographic algorithm engine, active measurement module and so on. It receives the command data stream delivered by the kernel-level trusted cryp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com