Portable trustworthy private information processing system
An information processing system and portable technology, applied in the field of private information processing systems, can solve problems such as security efficiency discount
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] The present invention will be further described below in conjunction with accompanying drawing and embodiment:
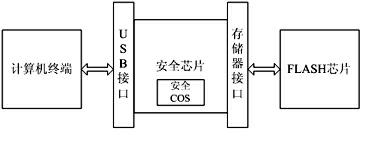
[0037] Such as figure 1 As shown, the physical composition of the portable reliable private information processing system includes a security chip, a Flash memory chip and a security COS. The security chip is connected with the USB port of the computer through the USB interface to complete the high-speed communication with the computer. At the same time, the security chip is connected with the Flash storage chip through the memory interface to realize the security storage function. The security chip can physically resist physical attacks, and logically the security function of the portable and reliable private information processing system is realized by the security COS.
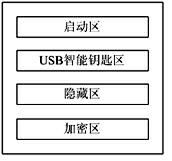
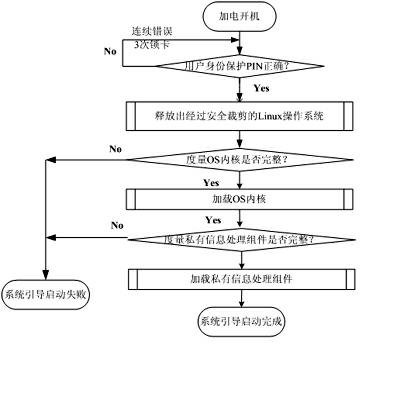
[0038] Such as figure 2 As shown, the logical composition of the portable trusted private information processing system includes four partitions, a boot area, a USB smart key area, a h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com