Method and device for protecting a reading device for card-shaped data carriers from unauthorized evaluation or copying of magnetically encoded data of an inserted card-shaped data carrier
A technology of data carrier and readout device, applied in the direction of coinless or similar appliances, induction recording carrier, complete banking system, etc., can solve problems such as failure, achieve the effect of preventing illegal collection and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
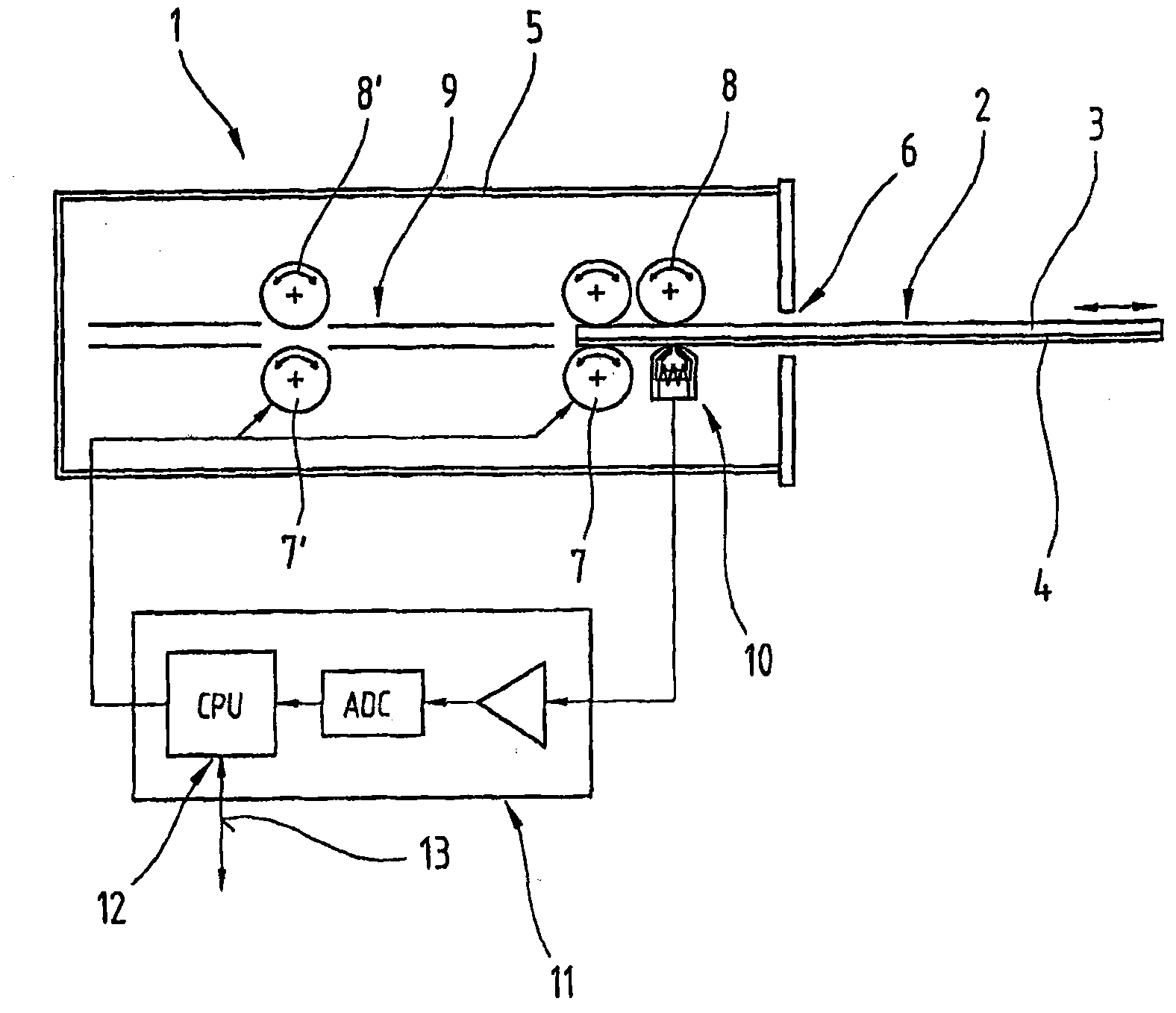
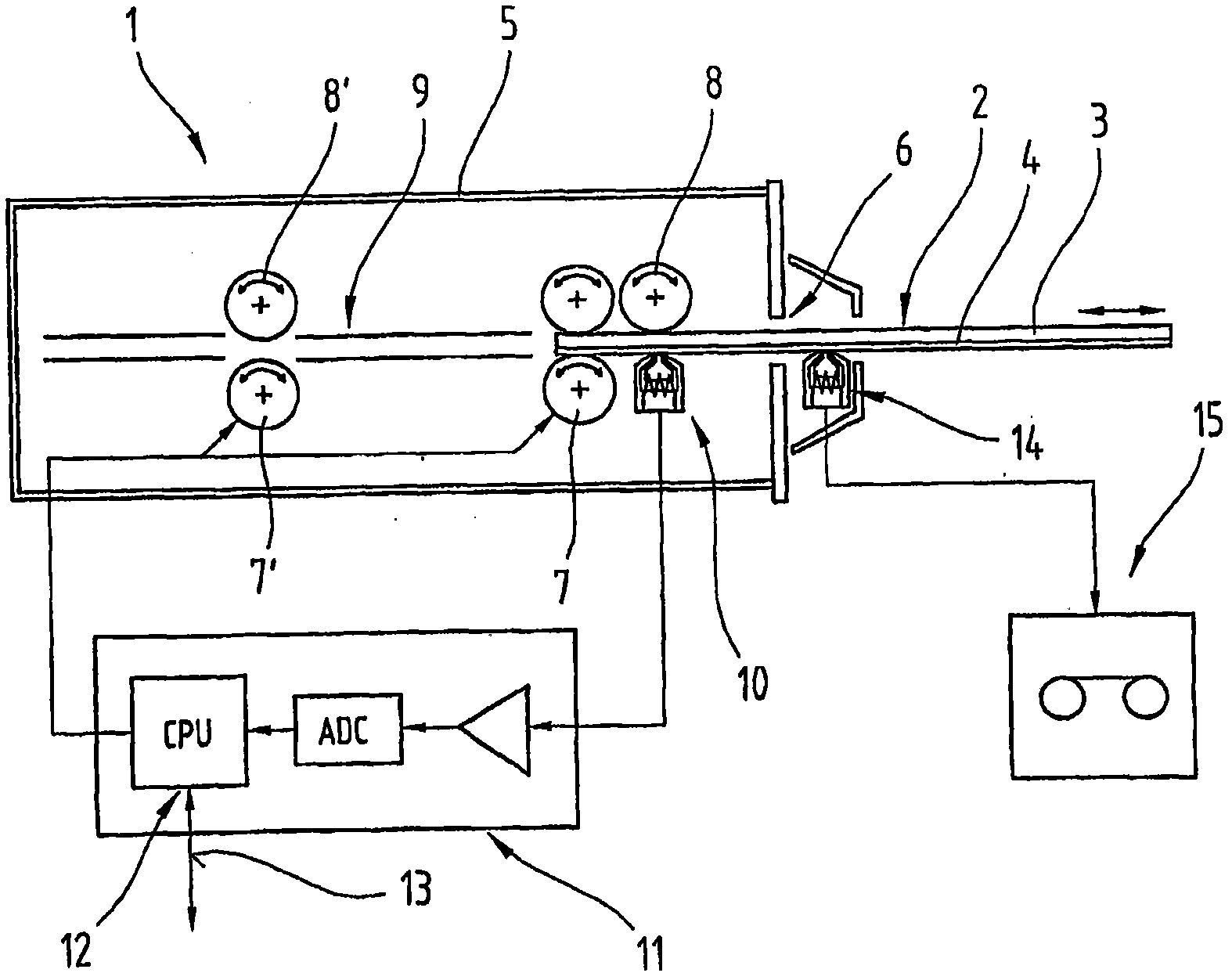
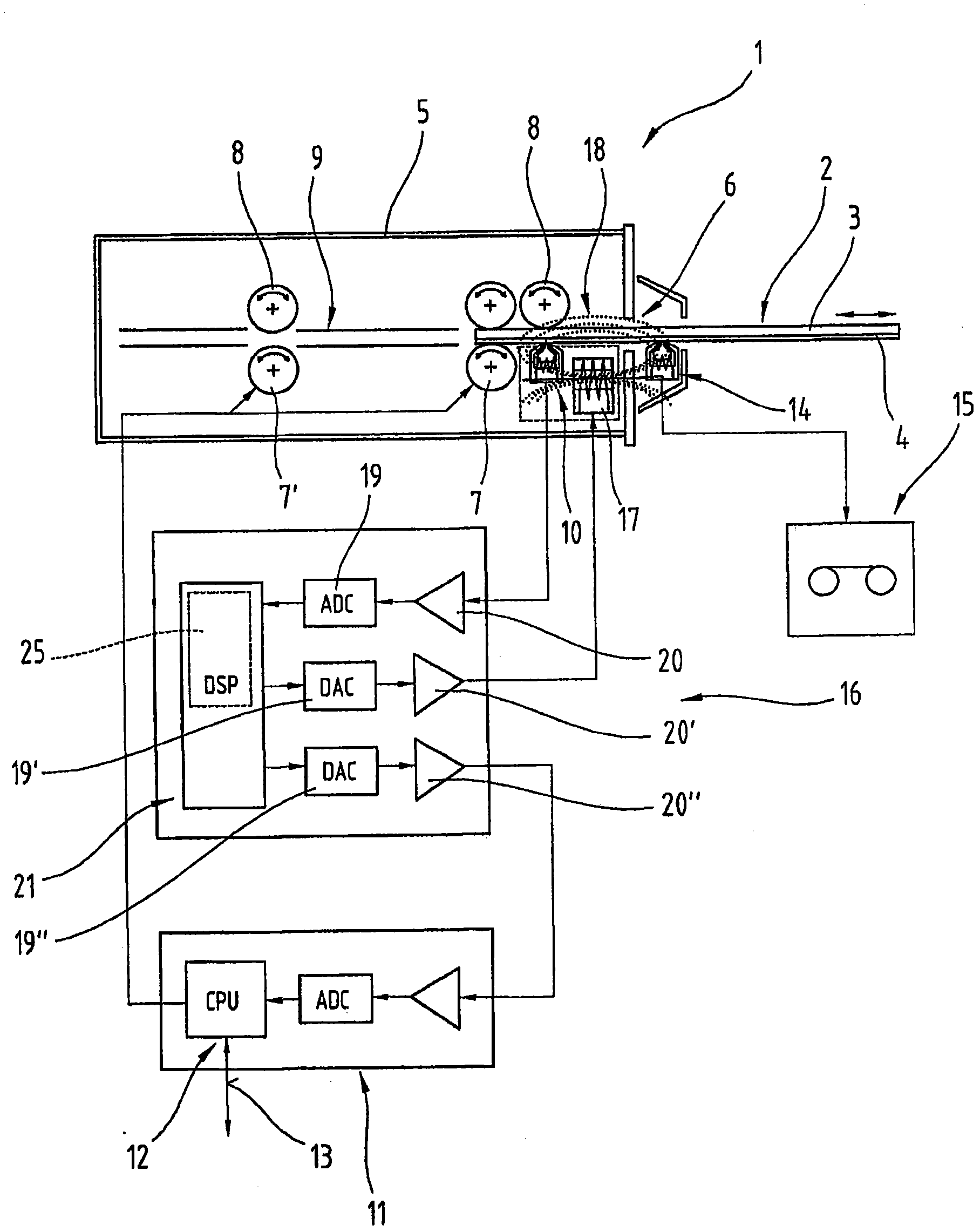
[0047] figure 1 A reading device 1 of a conventional card-shaped data carrier 2 is shown, on which information or data is stored at least magnetically. In particular, this reading device 1 is used to process magnetic cards 3 with at least one magnetic stripe 4 and / or chip cards with at least one magnetic stripe 4 . On these magnetic strips 4 , as is known, use-relevant or security-relevant data are stored, which data can be automatically read out from the reading device 1 and / or can be changed or updated. Such card-shaped magnetic data carriers 2 are in particular bank cards or debit cards and credit cards, which are used to authenticate the right to enter or use a specific device. That is, a given reading device 1 is often used in a bank or its automated machines or access control systems.
[0048] Such a reading device 1 usually has the following components: a housing 5; at least one insertion hole 6 or card reading slot for inserting and subsequently removing the data mag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com