User access method and system, user management method and system of closed user group
An access method and user technology, applied in the communication field, can solve problems such as exposing user privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
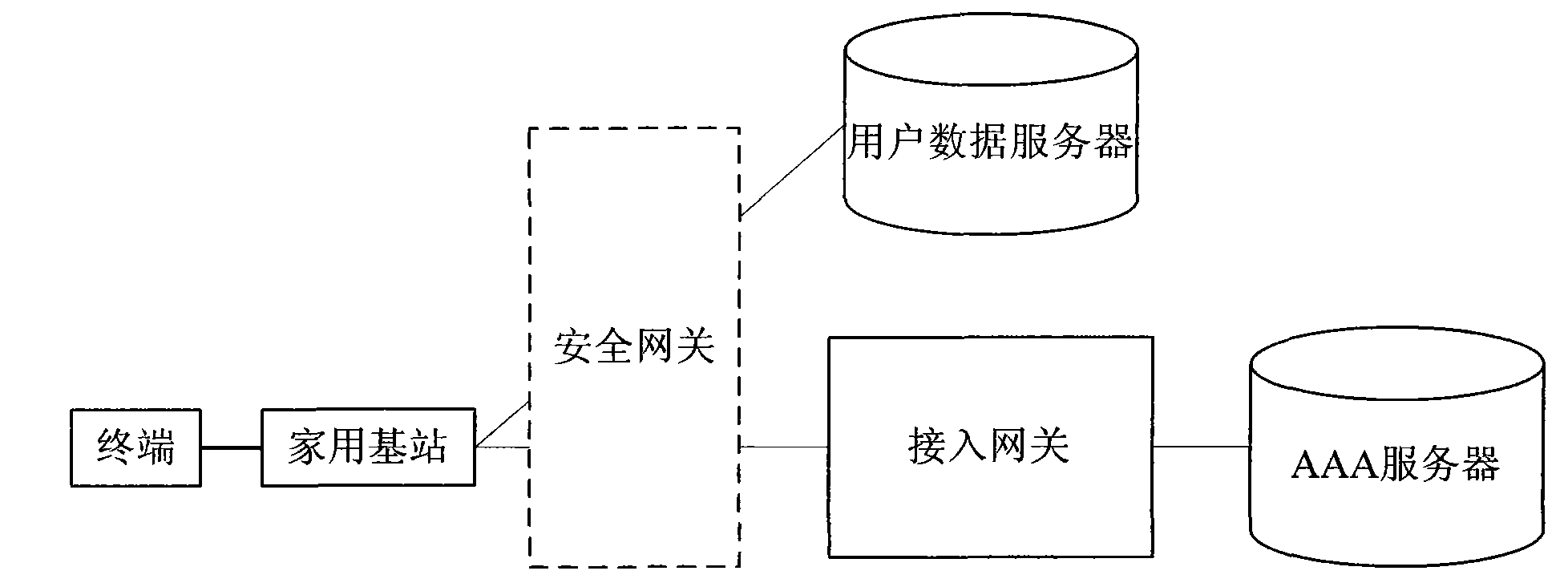
[0137] Figure 5 It is a flow chart of the first embodiment of the CSG member management method of the present invention; in this embodiment, the user (the owner of the home base station) manages the CSG members of the home base station by operating the home base station, and the user data server generates the SIS; like Figure 5 As shown, the method includes the following steps:
[0138] Step 501: The HNB accesses the mobile communication network, generally including the following sub-steps:
[0139] First, the femto base station discovers the security gateway it needs to connect to and establishes a security channel with the security gateway;
[0140] Secondly, with the participation of the AAA server of the home base station, mutual authentication is performed between the home base station and the mobile communication network connected to it;
[0141] Finally, the HNB interacts with the network to obtain a series of parameters required for the HNB initialization, and com...
Embodiment 2
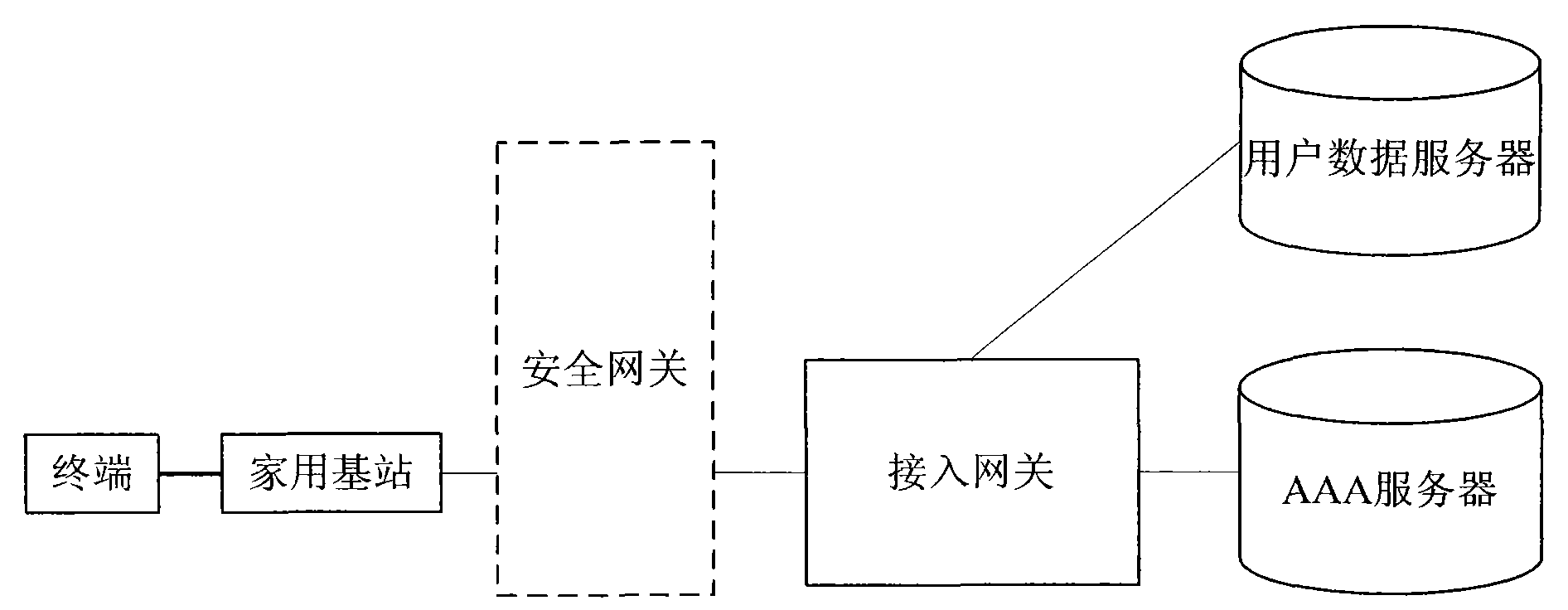
[0176] Figure 6 It is a flow chart of the second embodiment of the CSG member management method of the present invention; in this embodiment, the user (the owner of the home base station) manages the CSG members of the home base station by operating the home base station, and the home base station generates an SIS; as Figure 6 As shown, the method includes the following steps:
[0177] Step 601: Same as step 501.
[0178] Step 602: As described in step 502, the HNB receives a request to add the terminal user to its CSG member, for example, the owner of the HNB adds the terminal user to the CSG member of the HNB through the management interface on the HNB .
[0179] In this step, after receiving the above request, the HNB also needs to generate a parameter SIS for the terminal user.
[0180] The HNB may check the values of all SIS recorded locally, and then generate a new SIS different from these SIS as the parameter SIS.
[0181] In addition, the HNB may also directly ...
Embodiment 3
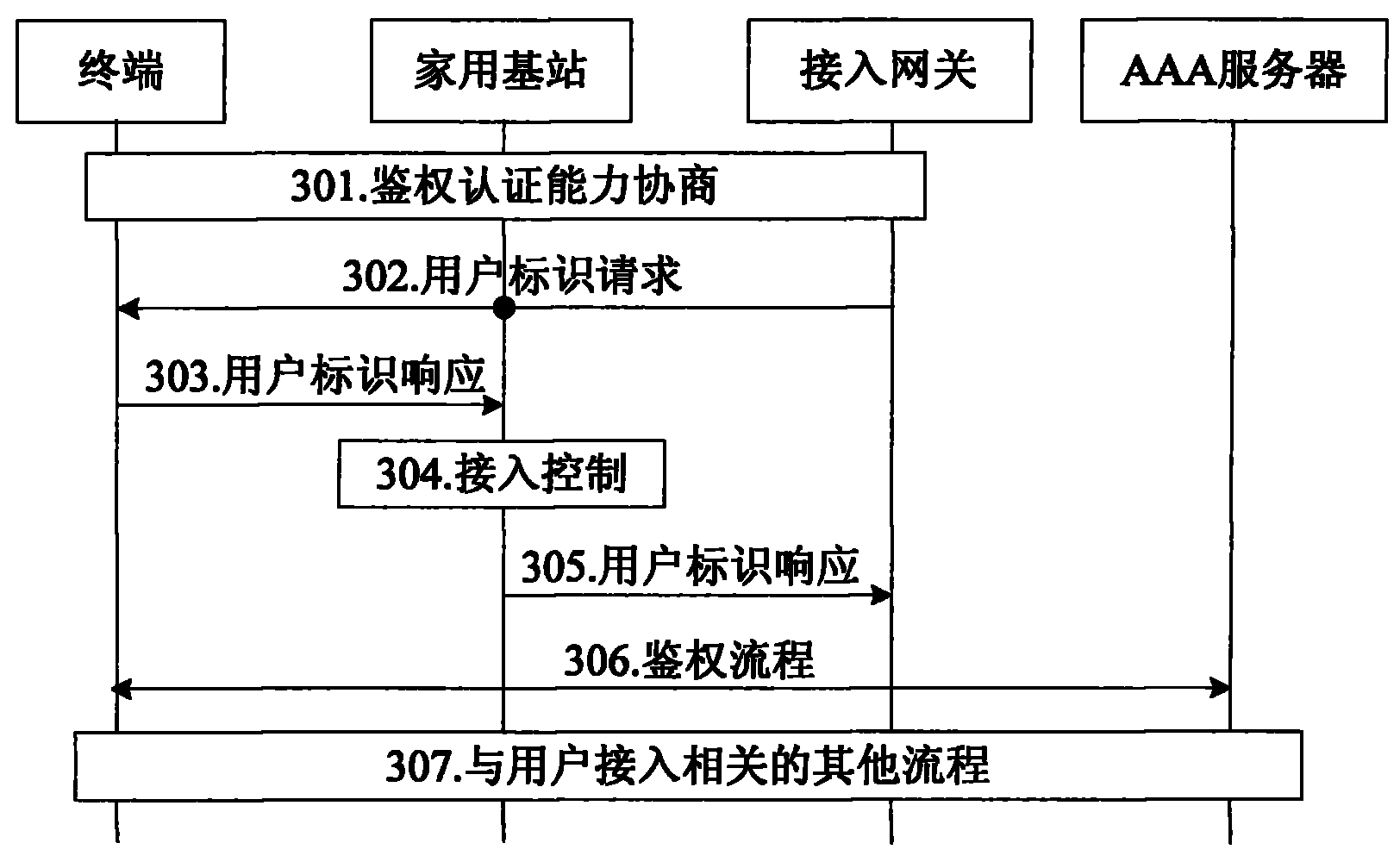
[0193] Figure 7 It is a flowchart of the third embodiment of the CSG member management method of the present invention; in this embodiment, the user (the owner of the home base station) manages the CSG members of the home base station through the user data server (for example, the owner of the home base station through Call the operator to request to add the end user to the CSG member of the femtocell it owns), and the SIS is generated by the user data server; as Figure 7 As shown, the method includes the following steps:
[0194] Step 701: same as step 501.
[0195] Step 702: The user data server receives a request to add the terminal user as a CSG member of the HNB.
[0196] The above request includes at least the HNB ID and the real user ID of the terminal user.
[0197] In addition, the above request may also include attribute parameters of the terminal used by the terminal user, such as the MAC address of the terminal, the MSID of the terminal, and the like.
[0198...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com