Digital signing method based on mobile phone intelligent card
A digital signature and smart card technology, applied in the field of mobile smart cards, can solve the problems of mobile phone number forgery, security risks in business processing methods, cloning, etc., and achieve the effects of strong compatibility, great practical value, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
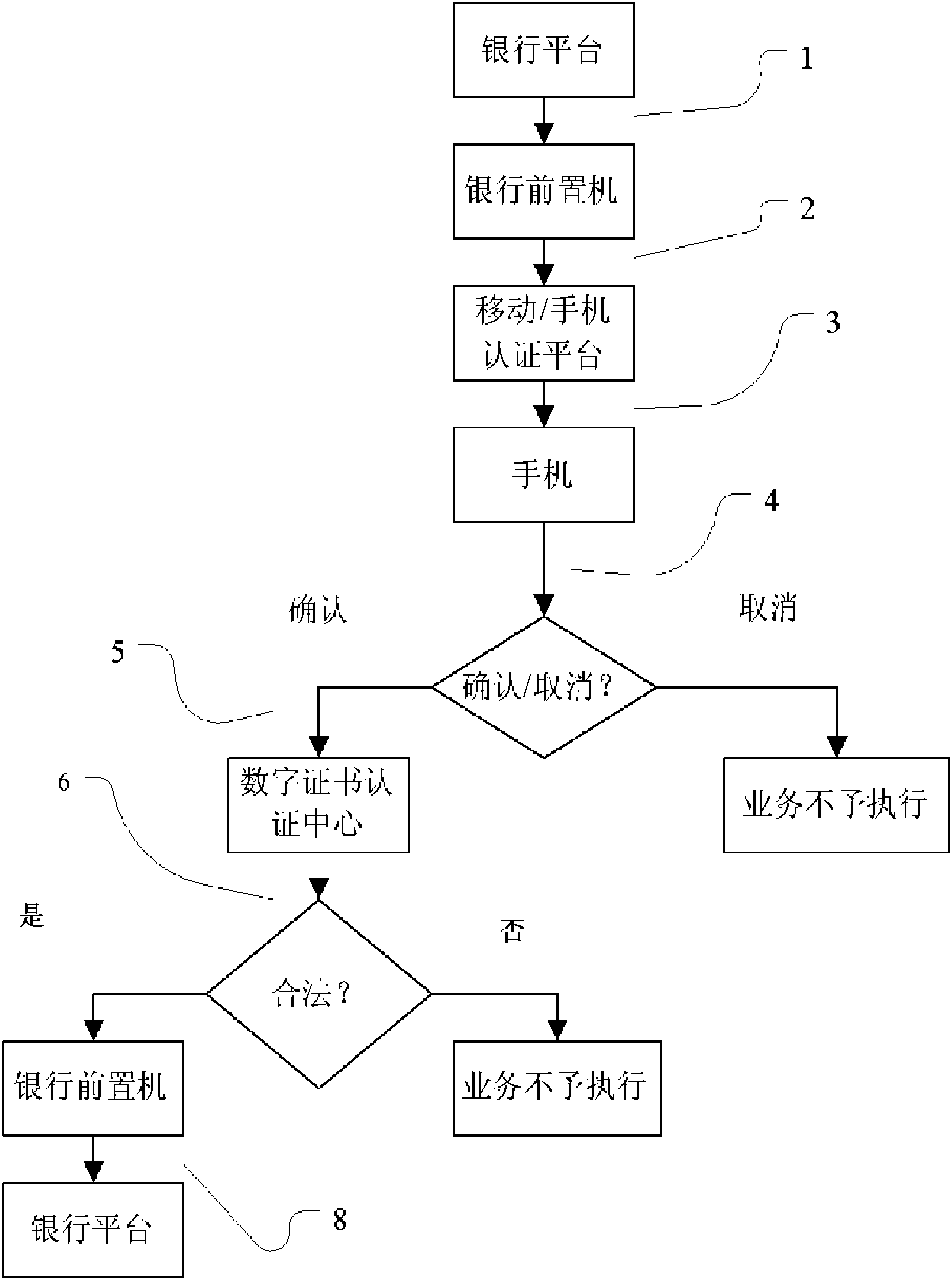
[0025] Combine below figure 2 Specifically describe the process of the user actively initiating banking business without being in any UnionPay business location. Such as figure 1 and Figure 4 As shown, this embodiment specifically includes the following steps:
[0026] Step 1: Various banking platforms send the data to be signed to the bank's front-end computer;
[0027] Step 2: The front-end computer of the bank forwards the data to be signed to the mobile authentication platform;
[0028] Step 3: The mobile authentication platform organizes the data to be signed, and forwards the organized data to be signed to the user's mobile phone in the form of a short message containing 3DES encryption and MAC verification mechanism;
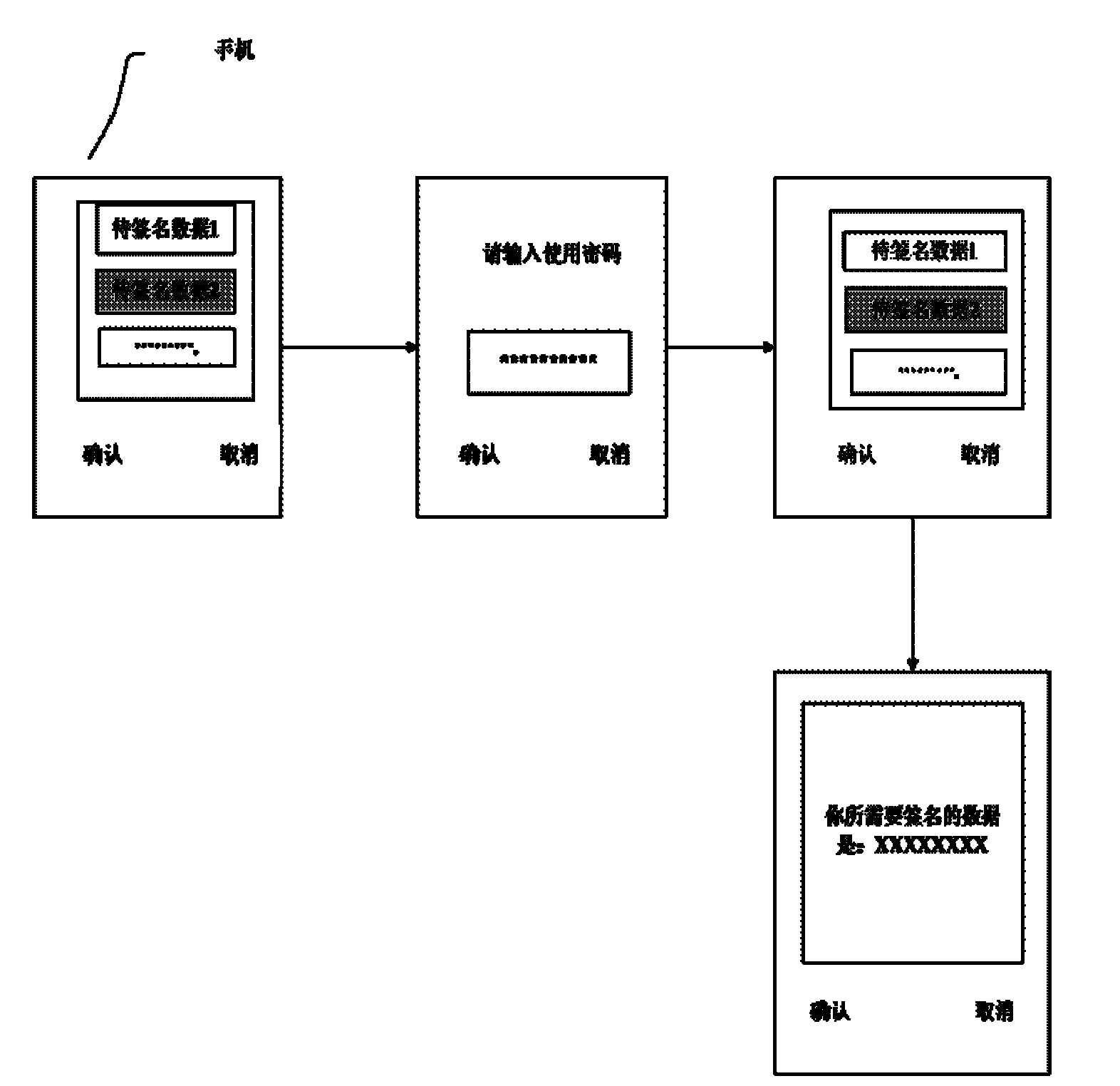
[0029] Step 4: The STK menu in the smart card with RSA encryption module and storage computing communication function displays text content, reminding the user to confirm the specific data in the banking business submitted by the user. If the user c...
Embodiment 2
[0046] Combine below image 3 It specifically describes how the user receives and executes the received banking business processing request when the user is not in each business point of the bank. Such as figure 2 and Figure 4 As shown, this embodiment specifically includes:
[0047]Step 1: The user's smart card receives the data to be signed sent by various banking platforms;
[0048] Step 2: The user clicks to view the data to be signed. The data to be signed is the key element of the specified transaction (such as the target account number, amount)
[0049] Step 3: The user confirms the data to be signed. If the user does not confirm, the banking business will not be executed, otherwise enter step 4;
[0050] Step 4: The smart card calculates the data to be signed
[0051] Step 5: The user signs the data and sends the result to the mobile authentication platform. If the user refuses to sign, the banking business will not be executed;
[0052] Step 6: The mobile auth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com