Ciphering and deciphering method and device for printed written files
A written document and print version technology, applied in the direction of public key for secure communication, user identity/authority verification, etc., to achieve the effect of strong security, convenient operation and low cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
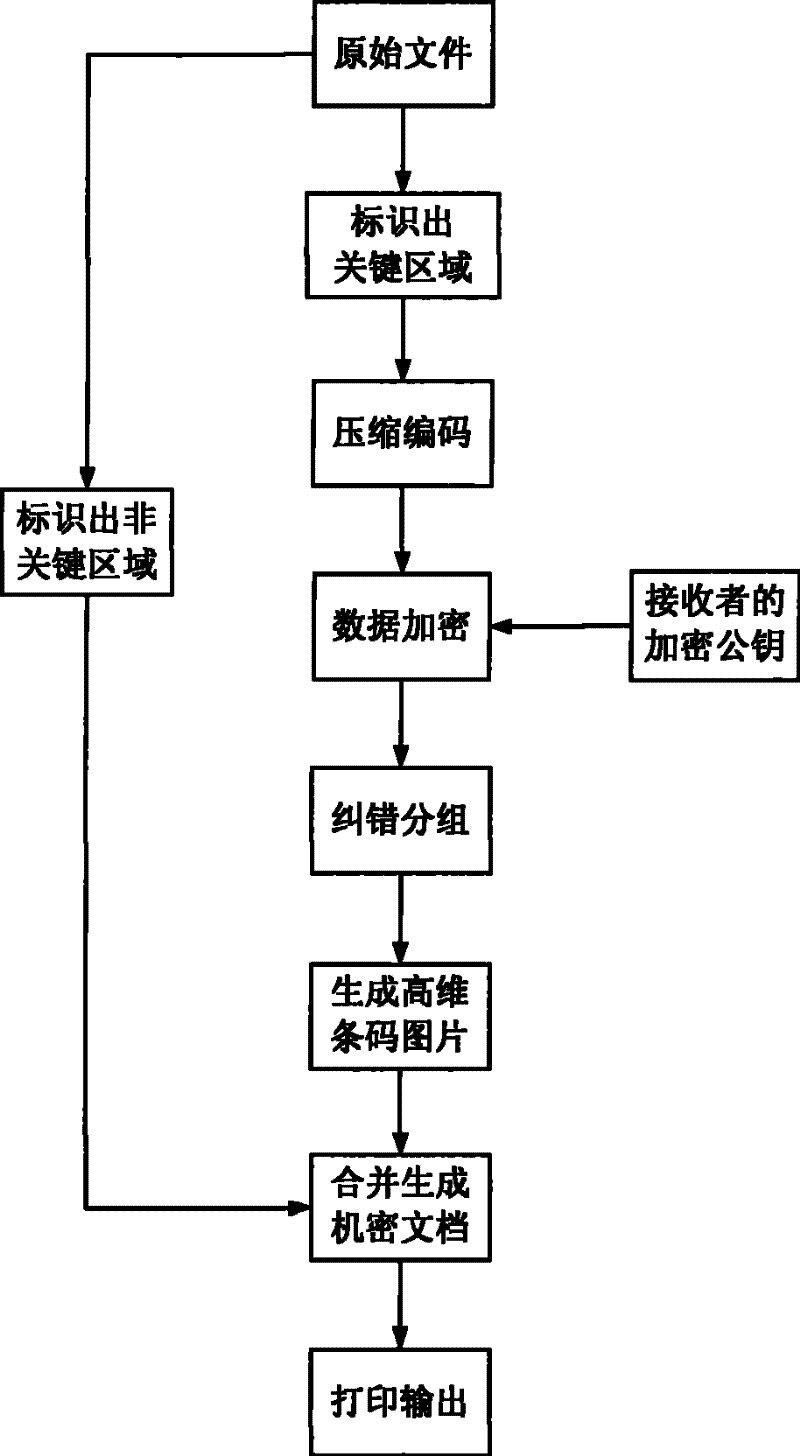
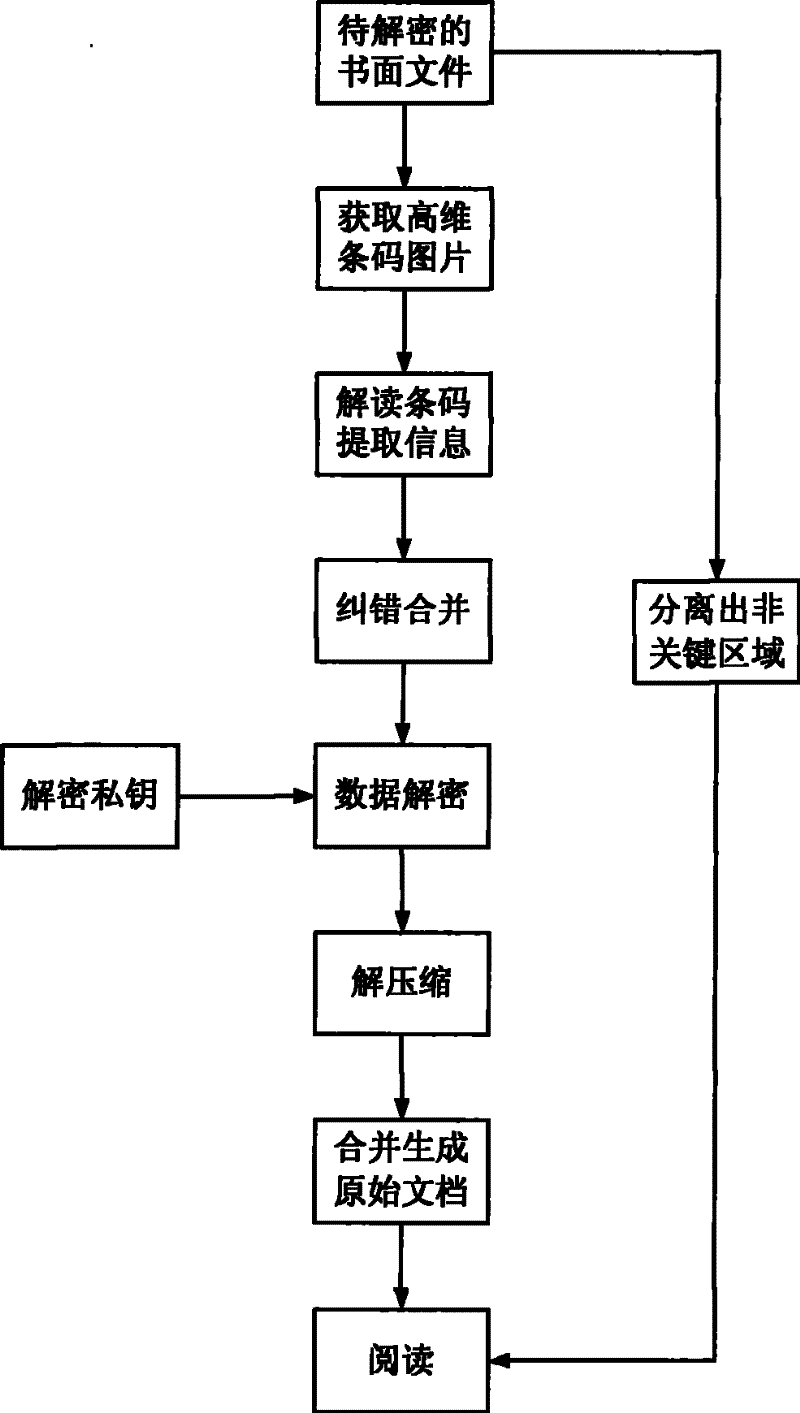
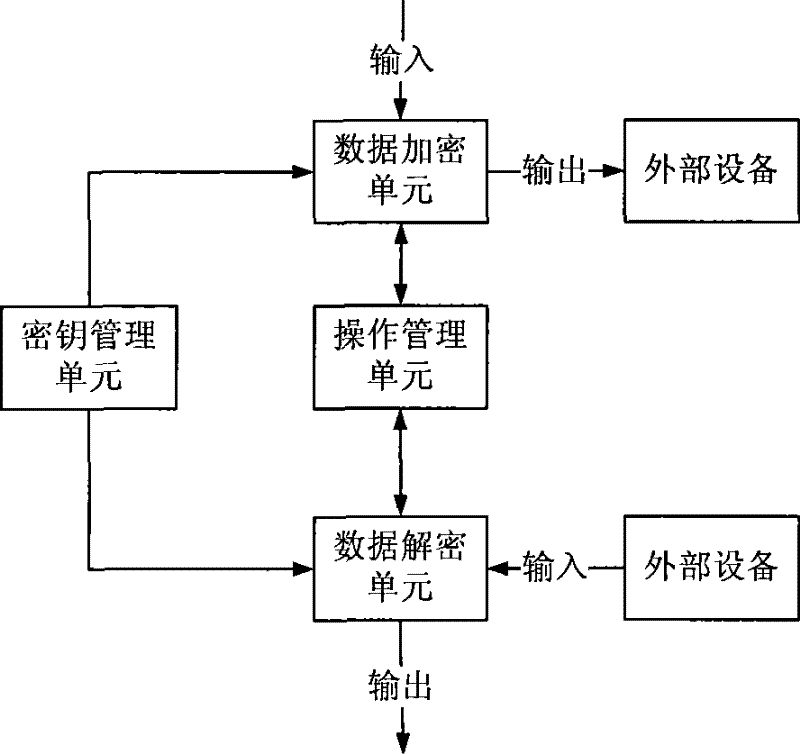
[0049] The background of this embodiment is assuming that user A needs to encrypt and protect key clauses in a printed commercial procurement contract, so that these key clauses can only be viewed by the other party B of the contract, so as to achieve the purpose of protecting commercial secrets. It can be seen from the description of the content of the present invention that this embodiment consists of three stages: key generation, encryption protection and decryption reading.
[0050] In the present embodiment, the selected one is the elliptic curve cryptosystem, and its cryptosystem parameters are as follows:
[0051] Randomly select a 192-bit large prime number p, the elliptic curve E(GF(p)):y 2 =x 3 +ax+b(mod p) is a secure elliptic curve defined on the finite field GF(p), on which the base point randomly selected is G=(x, y), and the order of the elliptic curve E is n=#E( GF(p)), r is a large prime factor of n.
[0052] in,
[0053] p=62771017353866807638357894232076...
Embodiment 2
[0088] The background of this embodiment is assuming that user A needs to make a copy as attached Figure 5 The structure, size, processing method and technical requirements of the key components in the mechanical drawings shown are encrypted and protected, so that these key information can only be viewed by legitimate users B, so as to achieve the purpose of protecting technical secrets and intellectual property rights. Similarly, this embodiment consists of three stages: key generation, encryption protection and decryption reading, and the parameters of the selected elliptic curve cryptosystem are the same as those in Embodiment 1.
[0089] Key generation stage: the purpose is to cooperate with the key issuing agency and the user to generate a decryption private key SK that only the user knows, and an encryption public key PK that can be made public, consisting of identity information SI and public key parameters PI. To complete the registration process, proceed as follows: ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com