Method for binding link layer information based on network access authentication information carrying protocol
A technology for network access and authentication information, applied in the field of link layer information binding based on PANA protocol, can solve the problems of unable to bind link layer information, unable to bind PANA client link layer information, etc. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0045] The preferred embodiments of the present invention will be described below in conjunction with the accompanying drawings. It should be understood that the preferred embodiments described here are only used to illustrate and explain the present invention, and are not intended to limit the present invention.
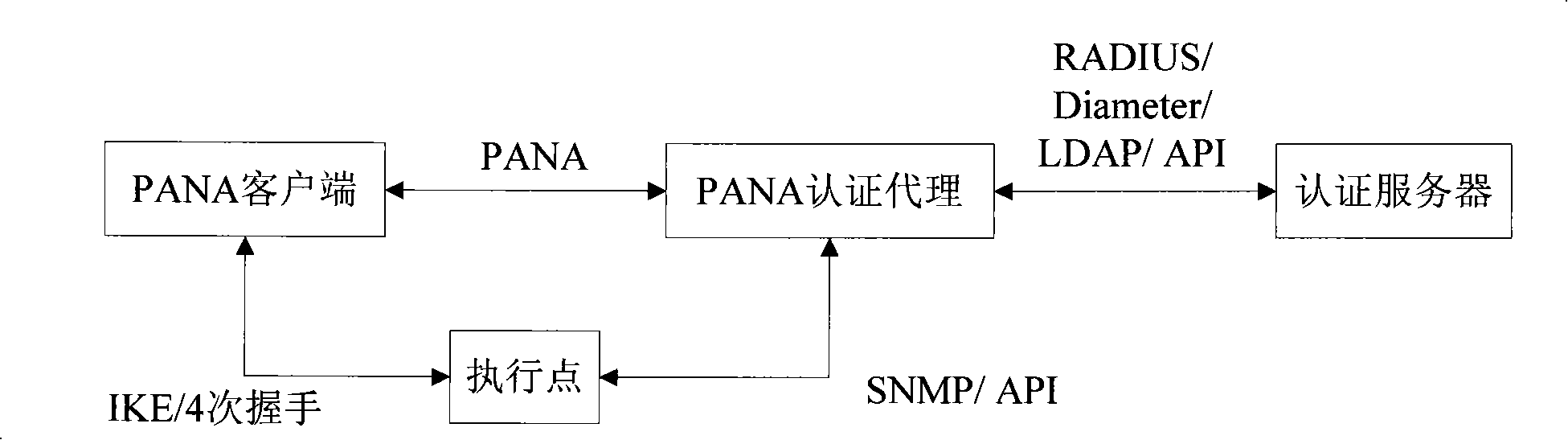
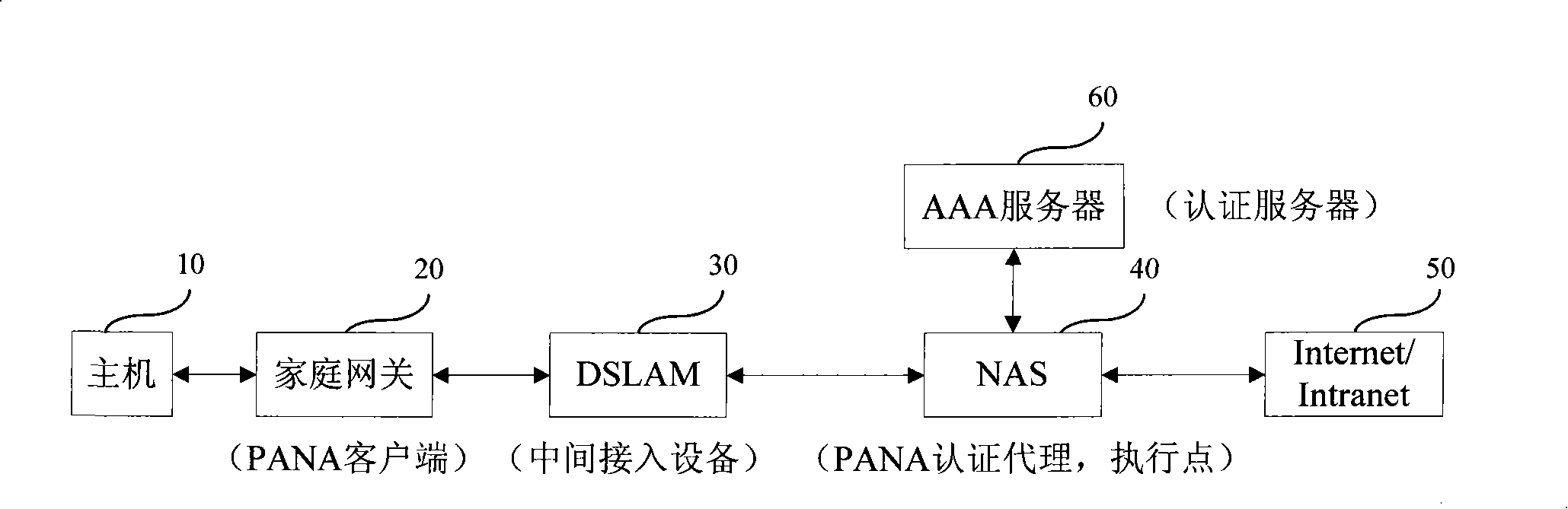
[0046] Such as image 3 As shown, the network structure of the embodiment of the present invention is composed of host 10, home gateway 20, DSLAM30 (Digital Subscriber Line Access Multiplexer, digital subscriber line access multiplexer), NAS 40, Internet / Intranet 50 and AAA server 60. Among them, the home gateway 20 has a PANA client function, the NAS 40 has a PANA authentication agent and an execution point function, the DSLAM 30 is an intermediate access device between the home gateway 20 and the NAS 40, and AAA (Authentication, Authorization, Accounting, authentication, authorization, billing) server 60 has an authentication server function.
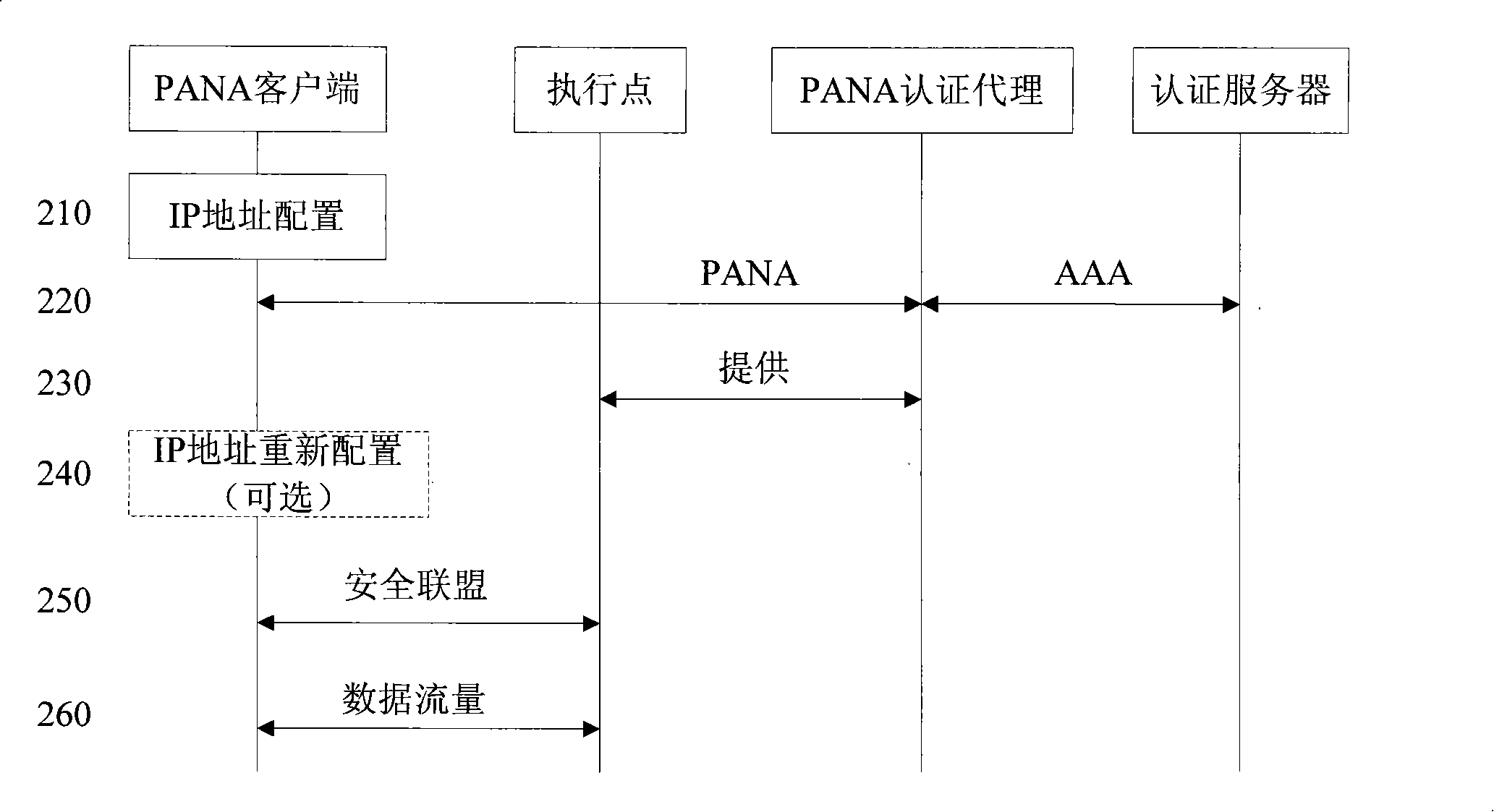
[0047] The followi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com