System for protecting information security of computer software or network
A network information and software technology, applied in the field of computer and communication, can solve the problems of third-party eavesdropping, tampering or counterfeiting, insecure transmission of computer software or network information, etc., and achieve the effect of protecting transmission security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0007] Embodiment 1. The system of the present invention involves identity verification agencies, information publishers and information users. The identity verification agencies have agreed with multiple information publishers or information users on an identity key based on a certain encryption method and based on this identity An official or unofficial (such as an enterprise) organization that verifies the identity of the information issuer or information user with the key. An information publisher or information user may have an information storage and processing device set on a ring for keeping the identity key. The ring includes but is not limited to watches, bracelets, bracelets, bracelets and the like. At the request of the information publisher or information user, the identity verification agency can use a certain identity key agreed with the information publisher or information user to transmit to the information publisher and information user respectively. The same...
Embodiment 2
[0009] Embodiment 2, the ring and its information storage and processing device in this example have a device based on wrist biometric recognition, such as wrist pulse biometric recognition or near-infrared sensing of veins, and recognition based on the criss-crossing characteristics of the vein network legitimate users. Or a device based on wrist biometric identification and other detection methods, such as simultaneous detection of alcohol concentration to determine whether the owner is conscious, to control the working status of the information storage and processing device. For example, if there is no pulse or abnormality outside the body, it can be closed. system. Control the working status of its information storage and processing device to be on or off. The information storage and processing device of the ring can directly exchange identity key information with the external information identification system through contact or non-contact, or indirectly exchange identit...
Embodiment 3
[0010] Embodiment 3, the ring and its information storage and processing device in this example have a device based on biometric identification or non-biological identification including but not limited to password identification, and control its information storage and processing device to be on or off working status. The information storage and processing device of the ring can directly exchange identity key information with the external information identification system through contact or non-contact, or indirectly exchange identity key information with the external information identification system through a supporting mobile phone.
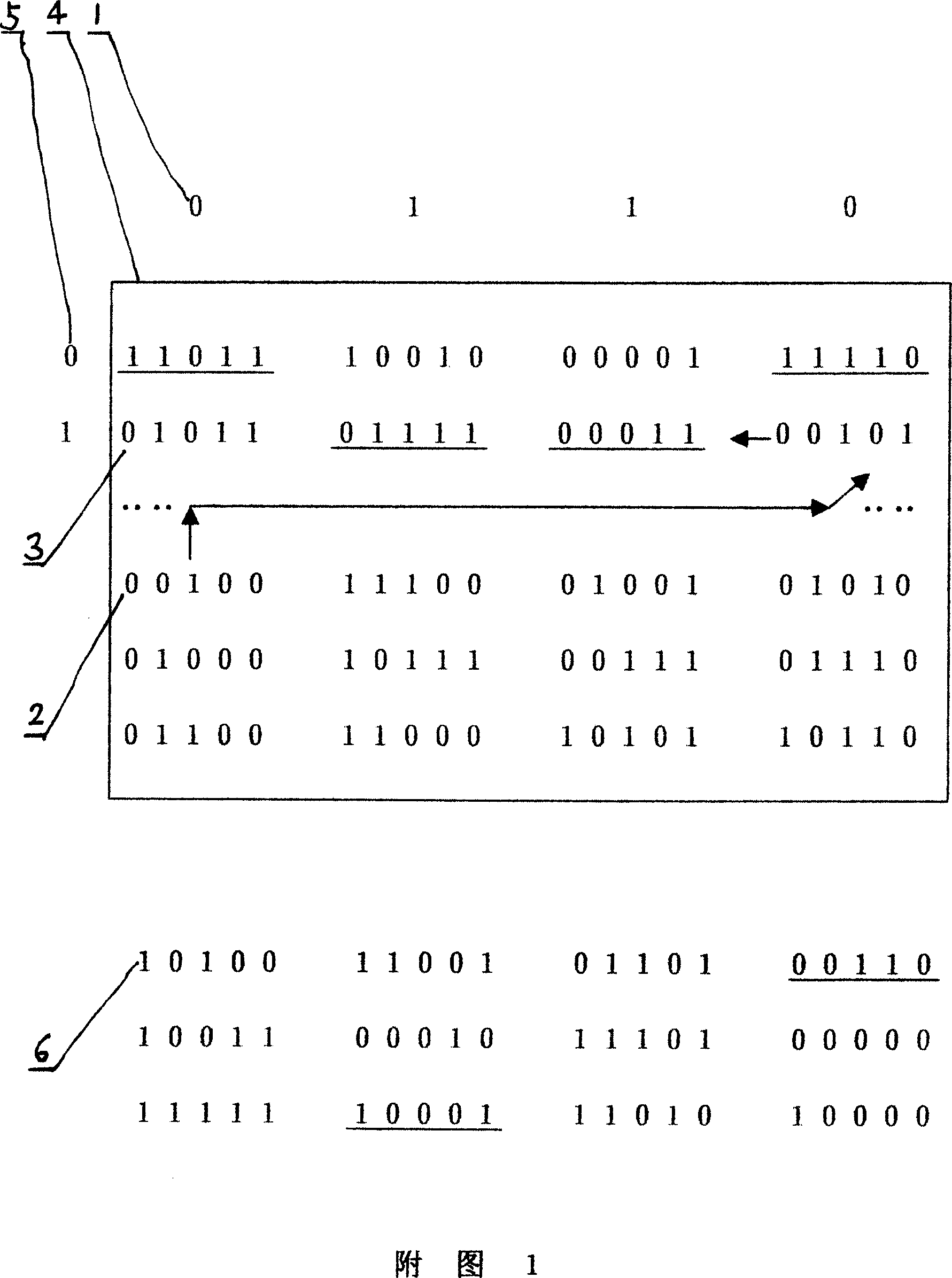
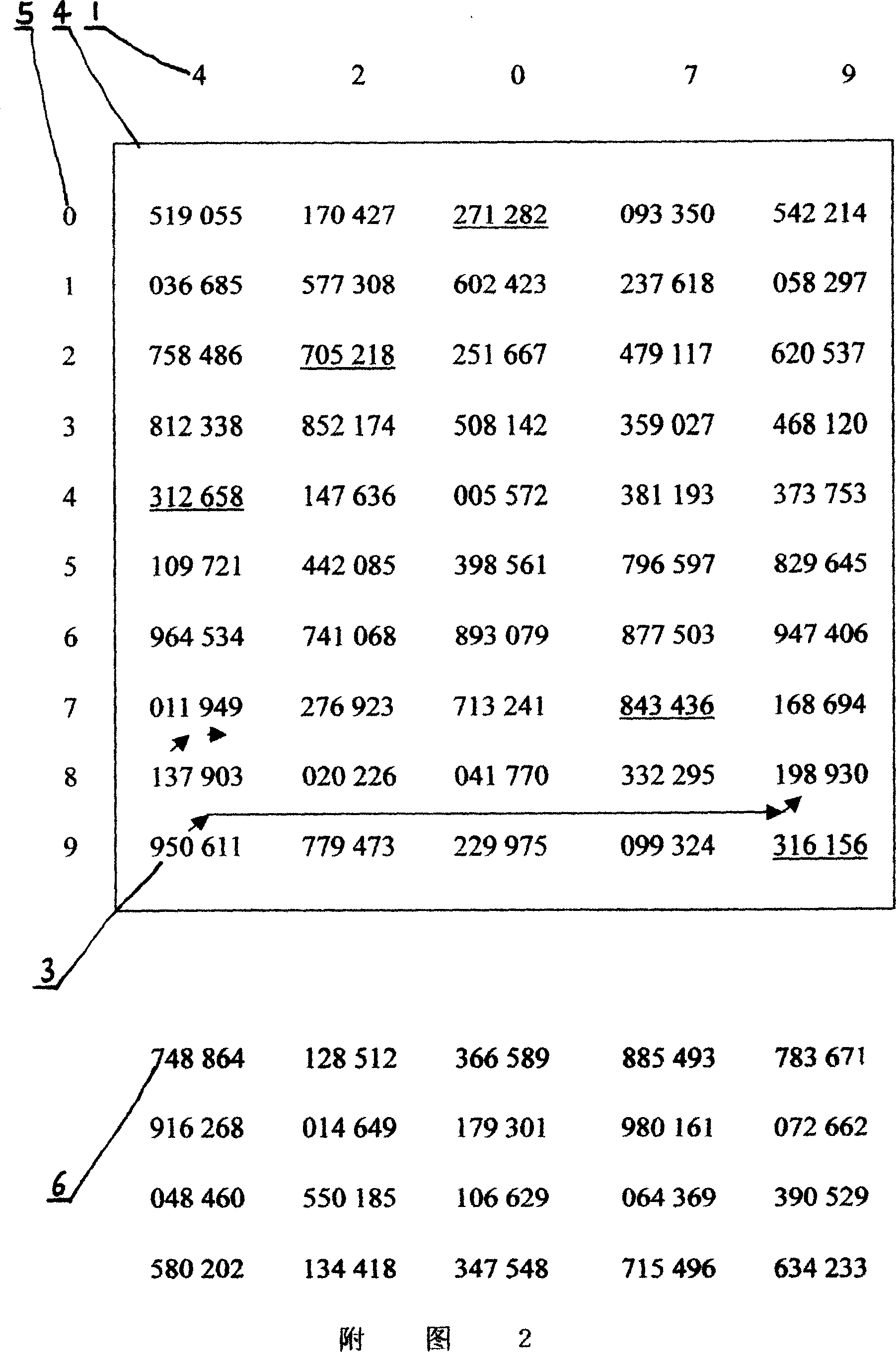
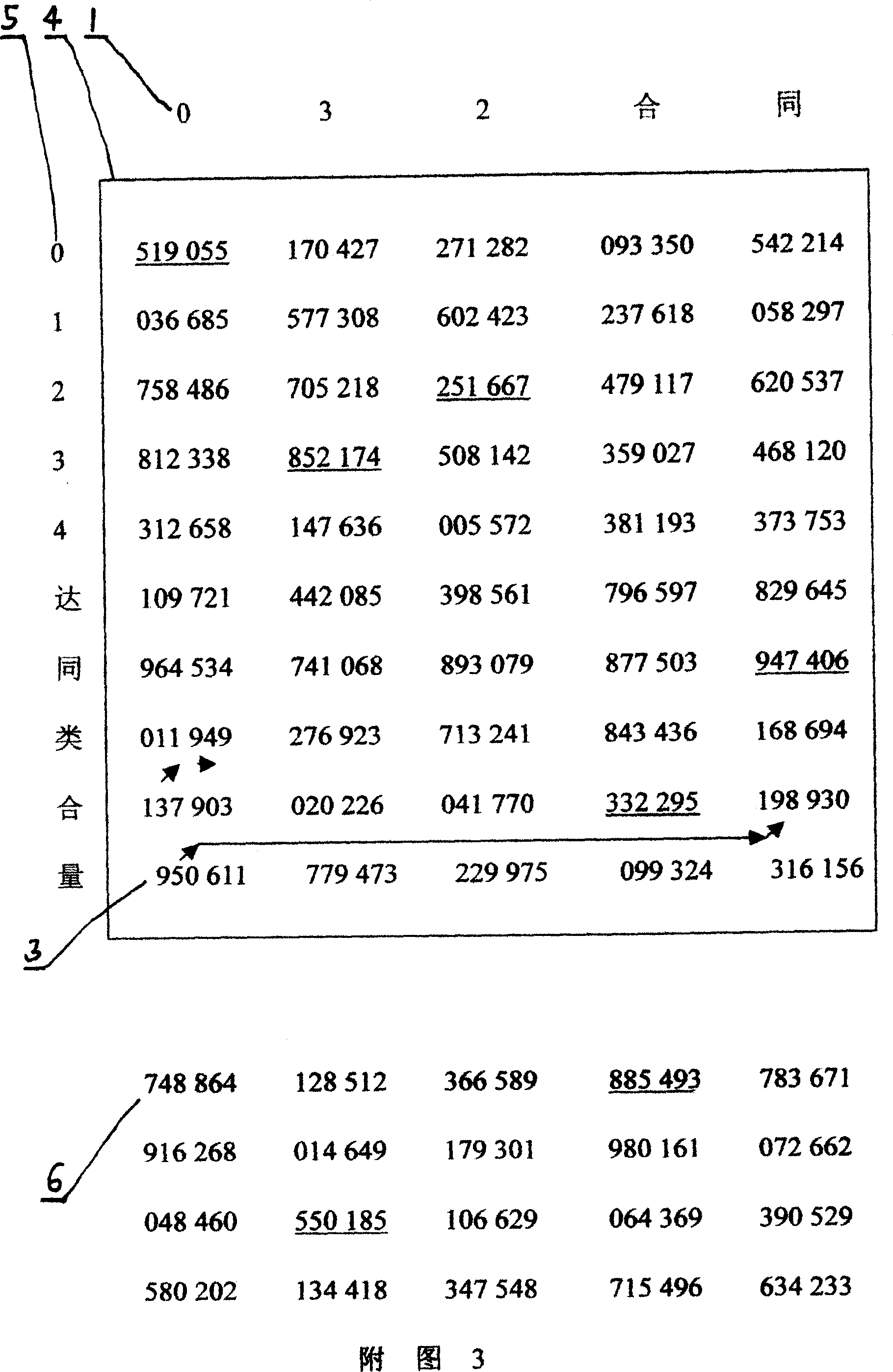
[0011] The identity key or exchange key kept by the information storage and processing device in the above three embodiments is a digital library [4] in a digital library encryption method. Please refer to Figure 1 for the principle. The encryption method of the digital database is to pre-agree on one or more digital databases [4] between th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com