Method, sending end, receiving end and system for protecting information transmission security
A technology for protecting information and sending ends, applied in the network field, can solve the problems of high transformation costs and high information security costs, and achieve the effects of reducing costs, ensuring security, and saving costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] An embodiment of the present invention provides a method for protecting information transmission security, such as figure 1 As shown, the method includes:
[0037] Step 101, generate a challenge code according to the current time information of the sender.
[0038] Specifically, in this embodiment, the sender can generate a challenge code according to the current time information of the sender, for example:
[0039] The format of the challenge code is: {ClientTime:salt}, where ClientTime is the time information corresponding to the current time of the sender. Optionally, the challenge code can also include salt, which is a sequence number, random number or random string. Adding salt can Increase the complexity of the challenge code, thereby increasing the encryption complexity of the authentication code generated according to the challenge code, and further improving the security of the encryption. Wherein, the sending end may be a sending end receiving end used for s...
Embodiment 2
[0058] An embodiment of the present invention provides a method for protecting information transmission security, such as Figure 2a As shown, the method includes:
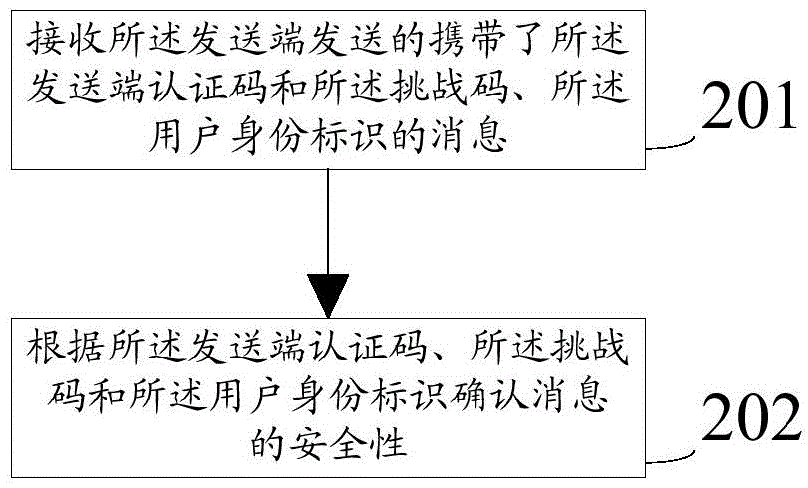
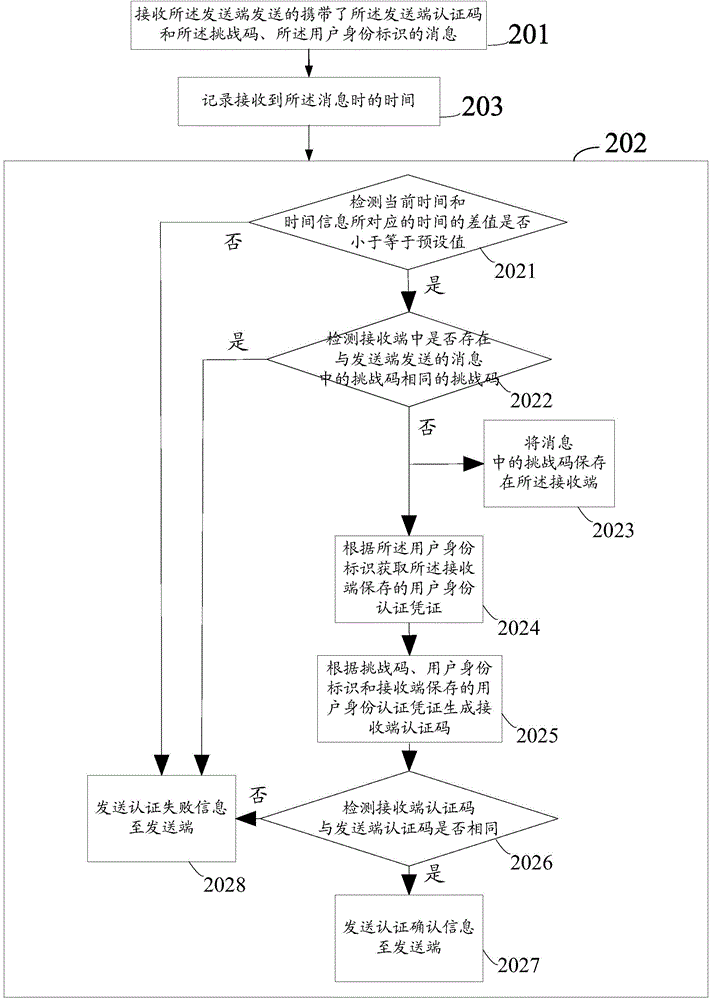
[0059] Step 201, receiving a message from the sender that carries the sender authentication code, the challenge code, and the user identity.
[0060] Among them, the challenge code is generated by the sender based on the current time information of the sender, and the authentication code of the sender is based on the challenge code, user ID and user identity authentication credentials saved by the sender, and the user ID is used to identify the currently used sender. For end users, user identity authentication credentials include passwords and digital certificates used to verify the legitimacy of user identity identification.
[0061] Specifically, in this embodiment, the receiving end as the execution subject may be a terminal, receiving end, switch, gateway device, router, etc., which have a data transmission r...
Embodiment 3
[0086] An embodiment of the present invention provides a sending end, such as image 3 shown, including:
[0087] The challenge code generating module 31 is configured to generate a challenge code according to the current time information of the sending end.
[0088] The sending-end authentication code generation module 32 is configured to generate a sending-end authentication code according to the challenge code, the user ID and the user identity authentication credential saved by the sending end.
[0089] Wherein, the user identity is used to identify the user who is currently using the sending end, and the user identity authentication credential includes a password and a digital certificate used to verify the legitimacy of the user identity.
[0090] Sending module 33, configured to send the message carrying the authentication code of the sending terminal, the challenge code and the user identity to the receiving end, so that the receiving end can code and the user identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com