Pseudo random number generation device
A pseudo-random number and generation device technology, applied in random number generators, secure communication devices, encoding/decoding devices, etc., can solve the problem of high processing speed, etc., and achieve the effect of high speed and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
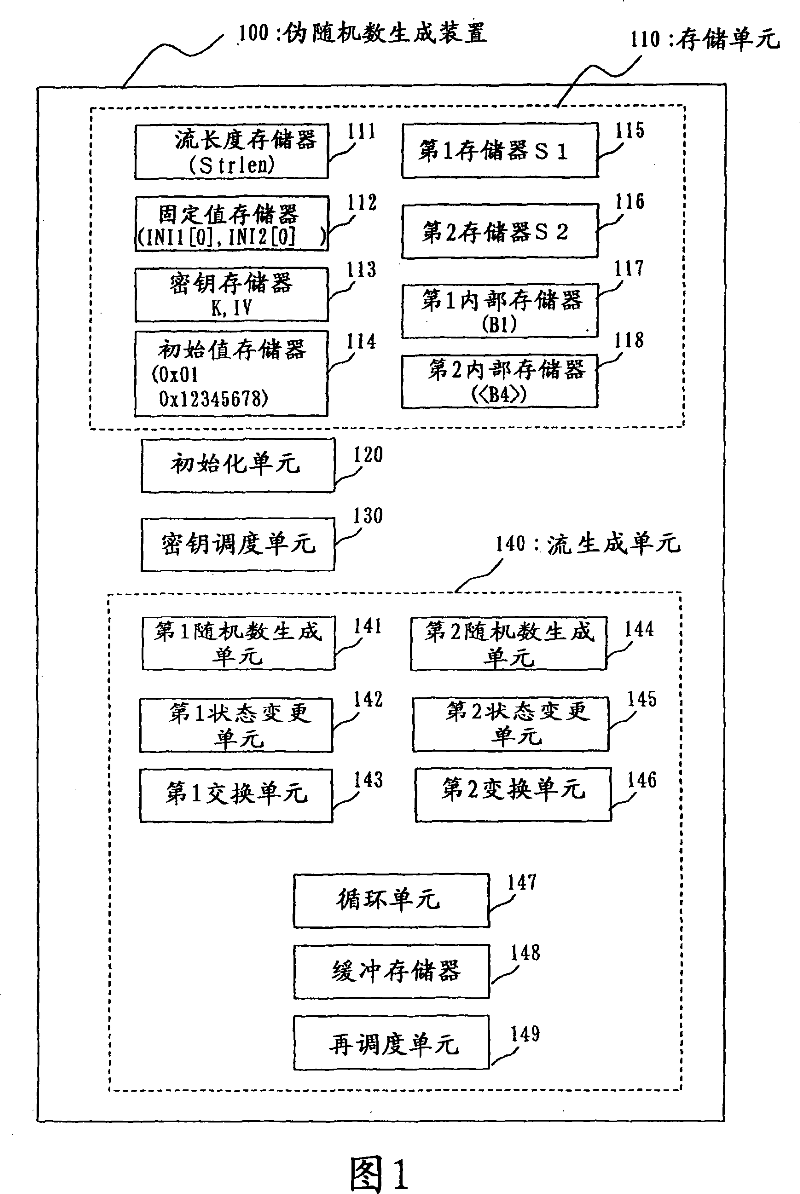
[0049] Embodiment 1 will be described using FIGS. 1 to 23 . Embodiment 1 relates to a pseudo-random number generating device, a pseudo-random number generating method, and a pseudo-random number generating program that generate pseudo-random numbers using two internal tables.
[0050] FIG. 1 is a block diagram of a pseudo-random number generator 100 in Embodiment 1. As shown in FIG. The pseudo-random number generation device 100 includes a storage unit 110 having various memories, an initialization unit 120 , a key scheduling unit 130 , and a stream generation unit 140 .
[0051] The storage unit 110 has:
[0052] (1) The stream length memory 111 storing the stream length L of the random number to be generated,
[0053] (2) The memory 112 for storing fixed values (INI1[0] described later, etc.),
[0054] (3) Key memory 113 for storing key information (K ([0], etc. described later),
[0055] (4) input and store the initial value memory of the initial value (0x01, 0x123456...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com