Method of distributing piracy protected computer software
a technology of computer software and smart cards, applied in the direction of program/content distribution protection, digital data authentication, television systems, etc., can solve the problems of large loss of profits for companies developing and selling computer software, undesirable software piracy, and failure of “backup” copies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0055]With the advent of personal computers, software piracy—copying software in which copyright exists—proliferated. With the implementation of graphical user interfaces, copying software has become a matter of dragging files from an original diskette to a blank diskette. In fact, software piracy is so prolific that it is estimated that more than one half of software in use today is pirated. Obviously, it is in the best interests of software providers to reduce software piracy.
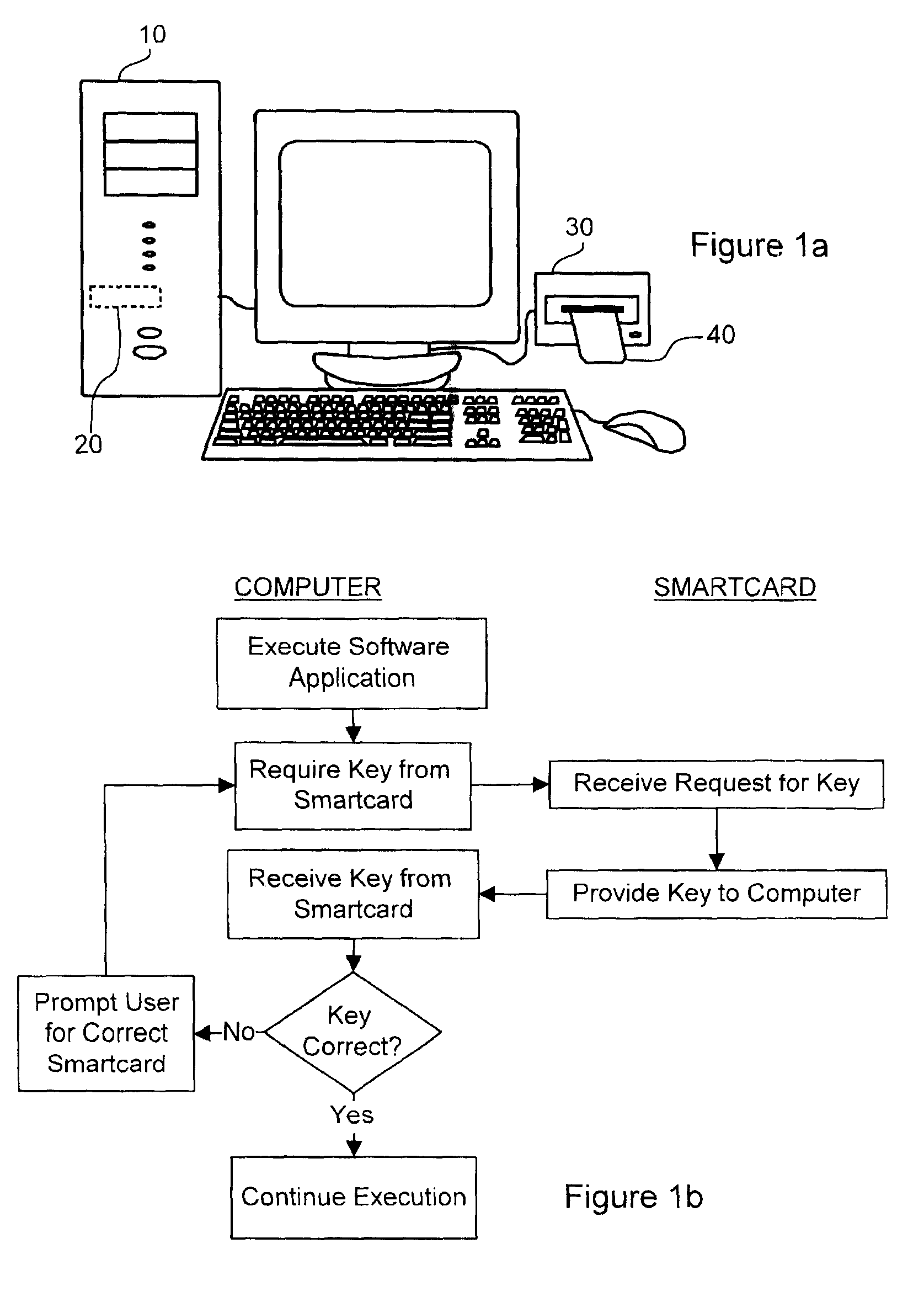
[0056]In the specification and claims that follow all items peripheral to computer functionality such as disk drives including hard disk drives, smart card readers, scanners, keyboards, printers, imaging devices, etc. are referred to as peripheral devices.
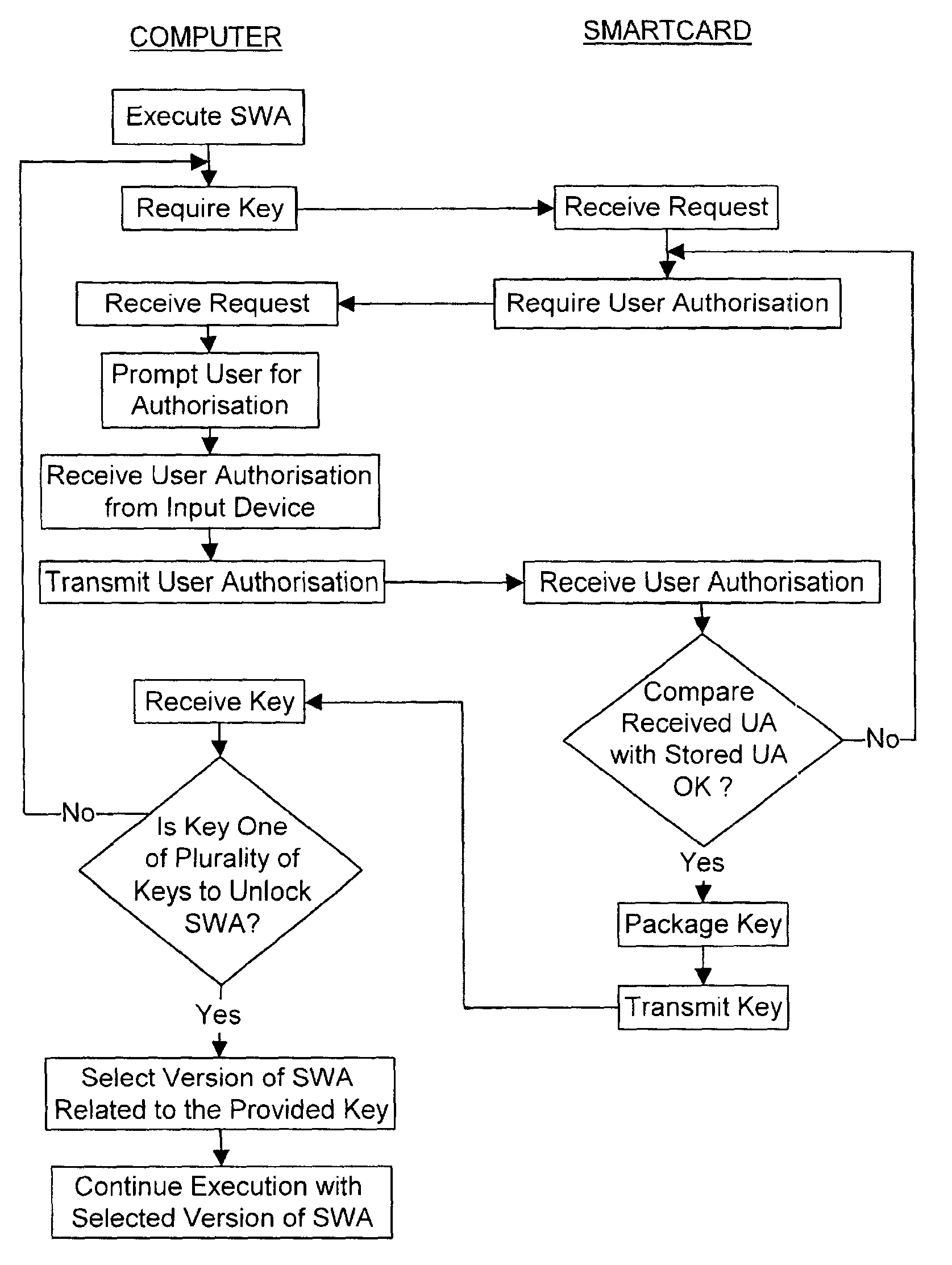
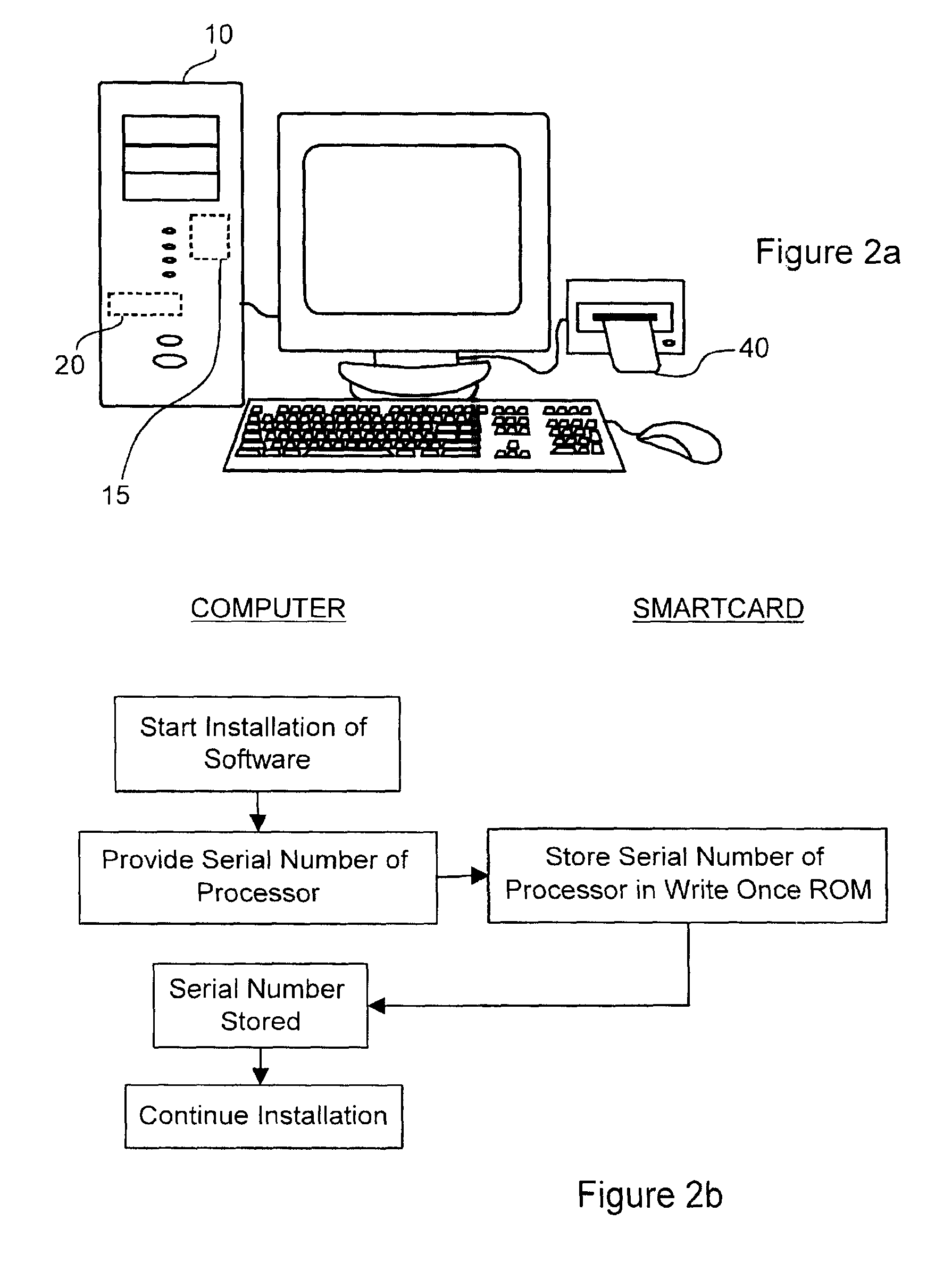
[0057]The invention provides a unique method for distribution of piracy-protected software. The method relies on a peripheral device such as a smart card to unlock software in order to permit execution thereof. The smart card is a credit card sized electroni...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com