Relocatable Storage Protect Keys for System Main Memory
a technology of system main memory and storage protection, applied in the direction of unauthorized memory use protection, redundant data error correction, instruments, etc., can solve the problem of not addressing the way the key and system data are in physical storage, and achieve the effect of improving ras and different and stronger ecc protection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
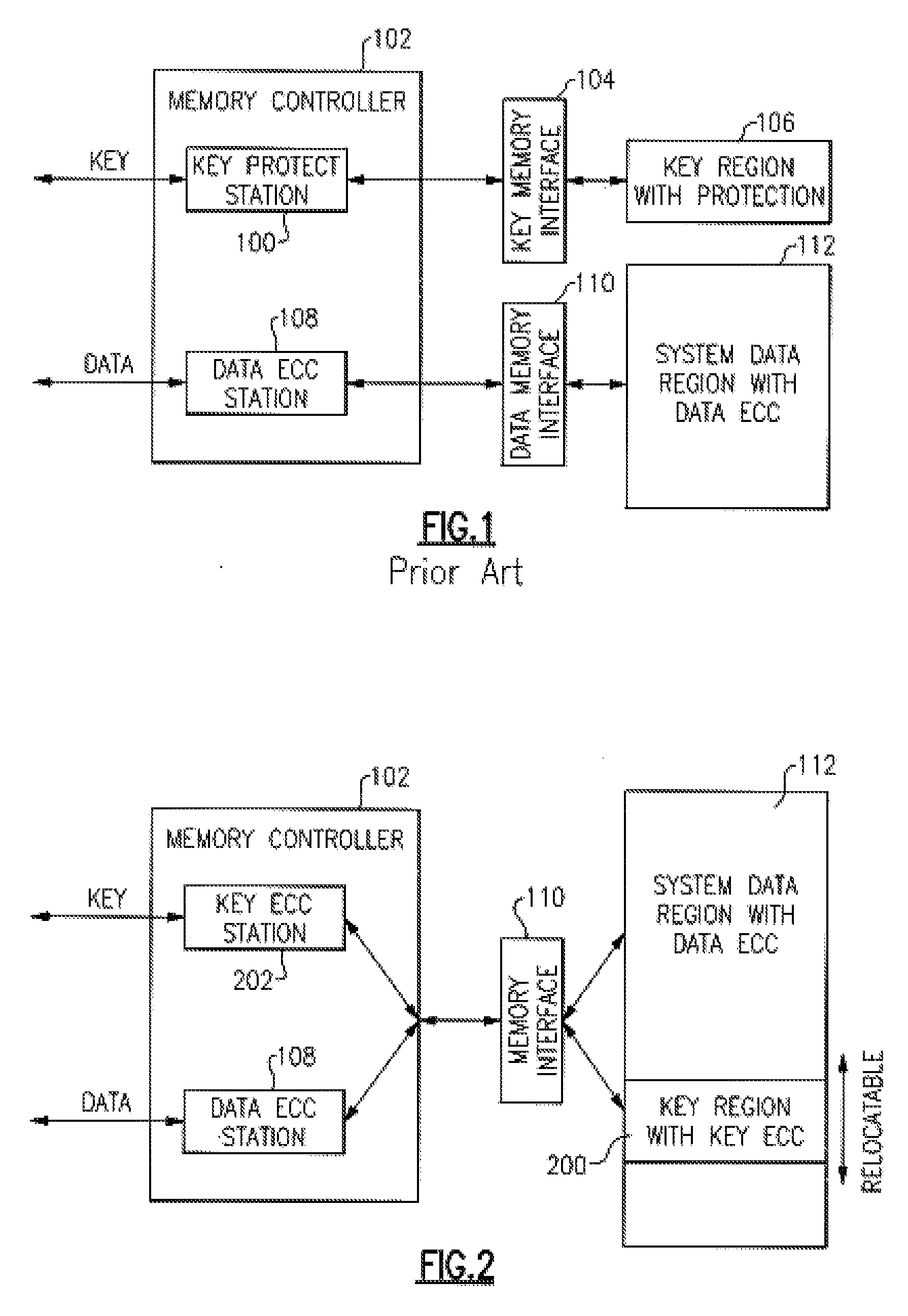
[0017]In the prior art arrangement of FIG. 1, SP data are entered from a key protect station i 00 in the memory controller 102 through a dedicated key memory interface 104 into a separate key storage region from the data protected by the SP data. The protected data are entered from a data ECC station 108 in the memory controller 102 through this data memory interface 110 into the system data region 112 containing data with Data ECC.
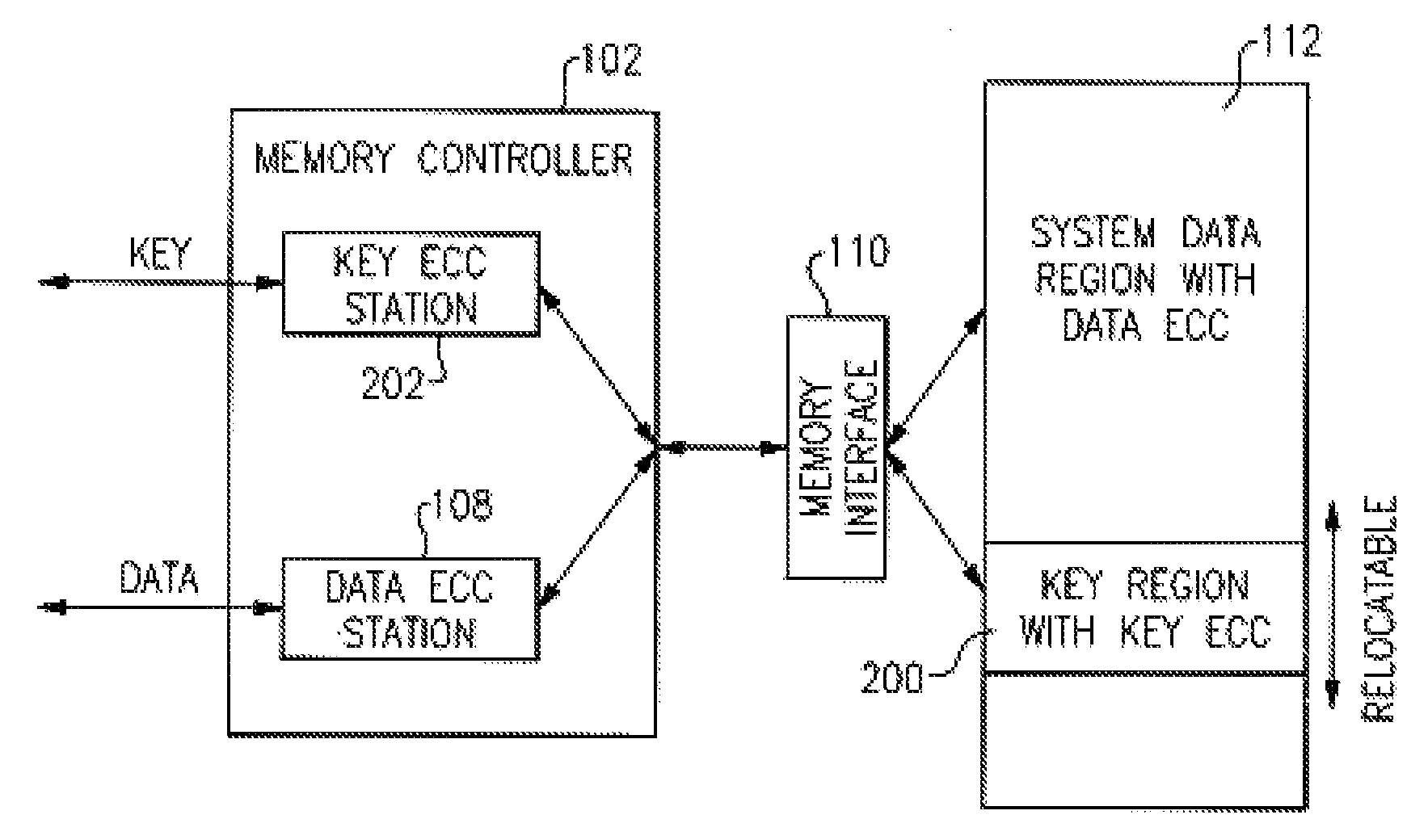
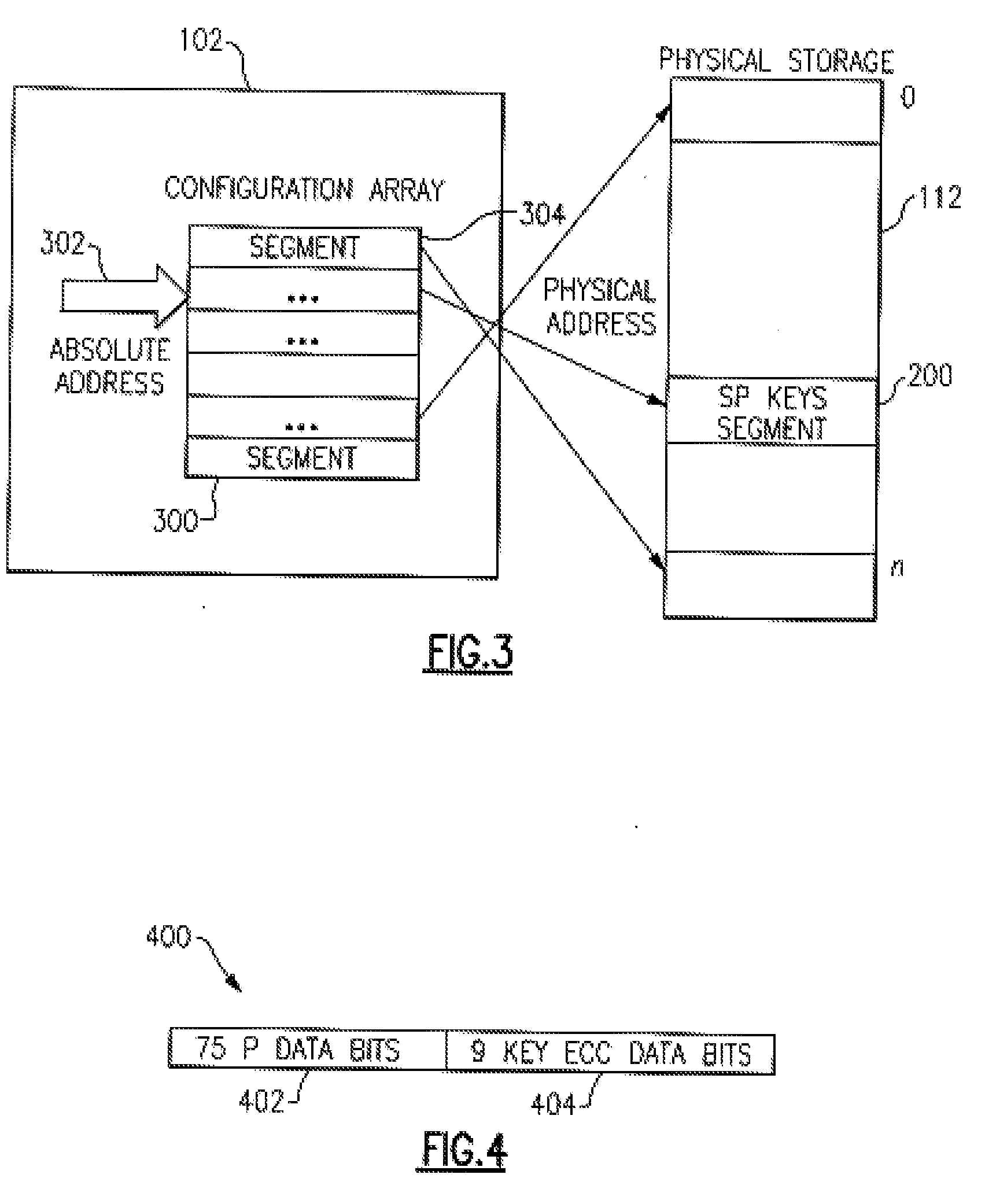
[0018]As opposed to the above described separated fixed / non-moveable memory physical location, to SP data in accordance with the present invention firmware can allocate any region within the physical storage to Storage Protection keys by using a configuration array which maps absolute addresses into physical addresses. This special SP key region is fully configurable, that can be allocated in any area within physical storage and can vary in size depending on the size of system main memory.
[0019]As shown in FIG. 2 a movable Key Region 200 with SP Key data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com