System and method for secure network purchasing
a network purchasing and secure technology, applied in the field of secure network purchasing systems and methods, can solve the problems of credit account information being intercepted on-line, credit card misappropriation risk, and little psychological comfort given to potential users, and achieve the effect of reducing the exposure to the risk of credit card th
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
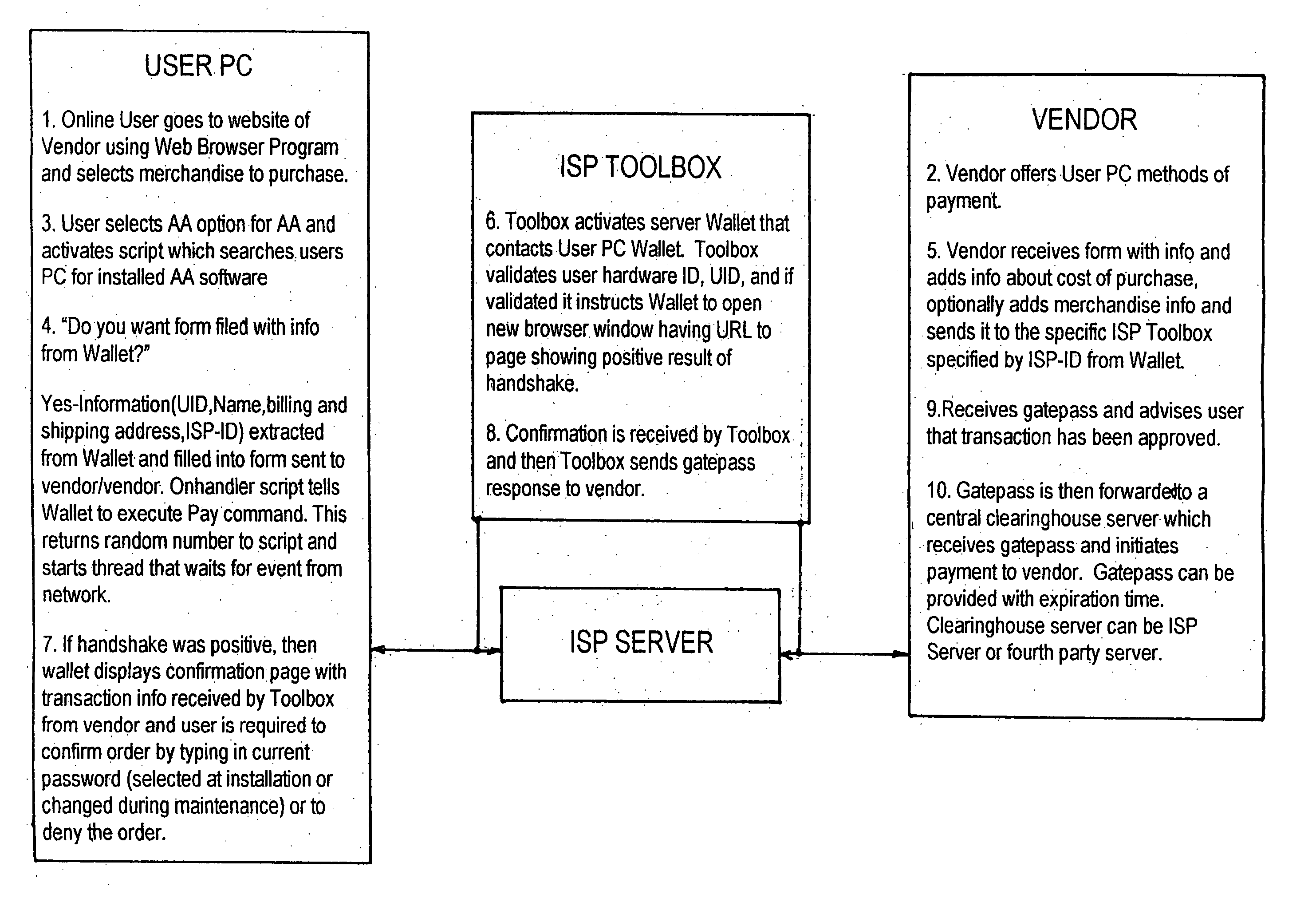
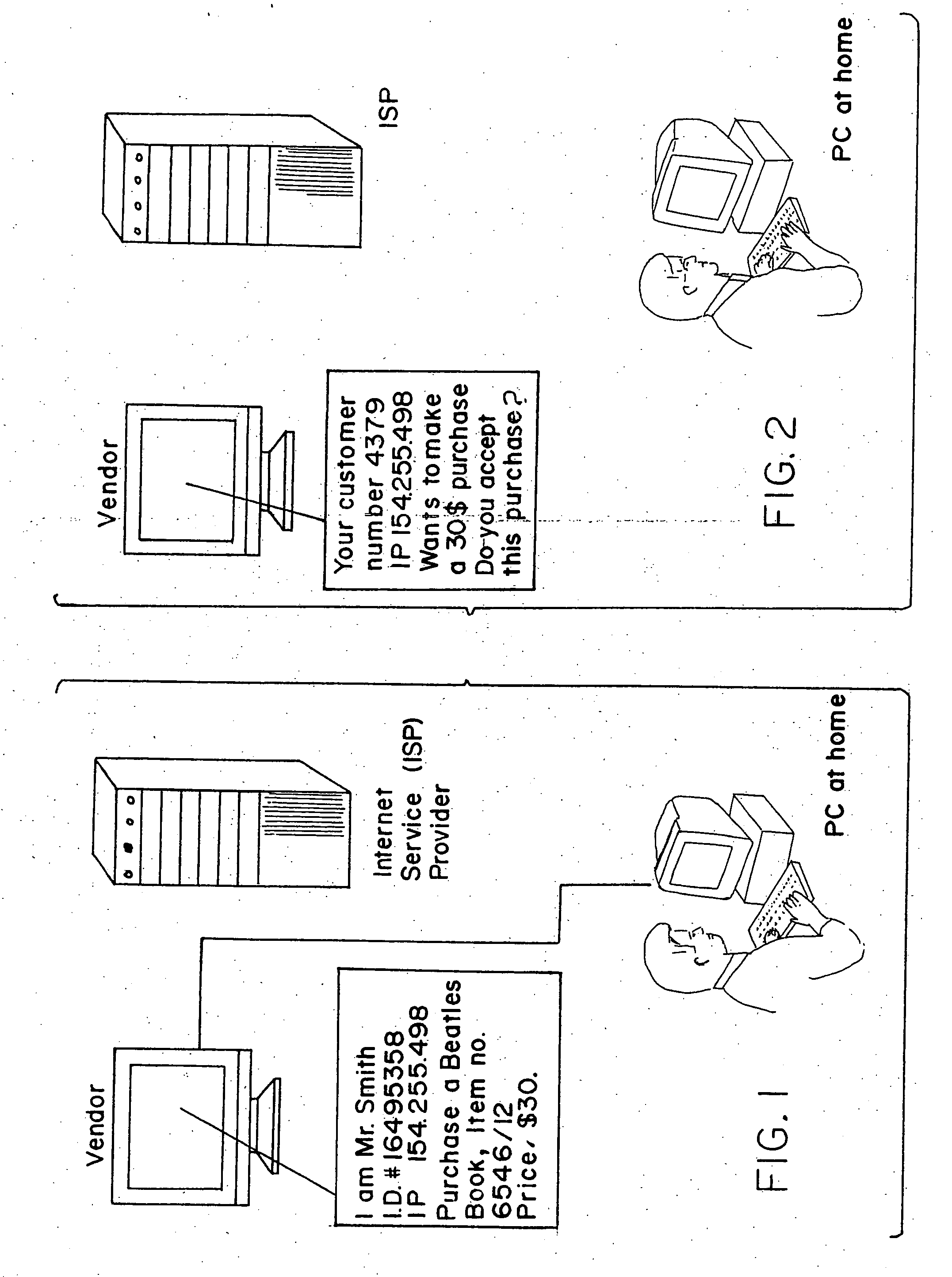
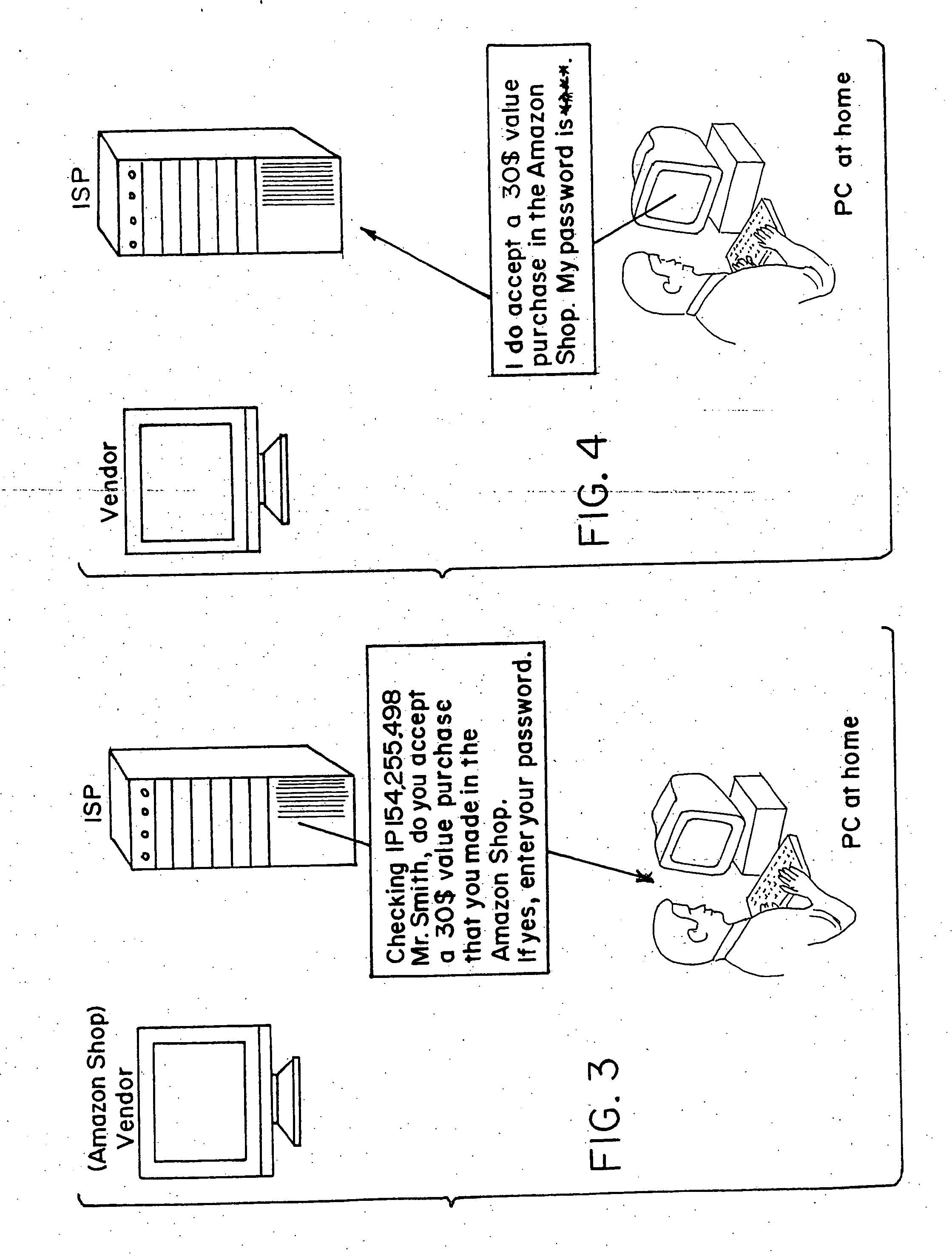
[0025] As was mentioned hereinabove, in one exemplary embodiment of the invention, the credit account for the subscriber (also referred to as an end user or Buyer) is established in the normal manner usually by providing credit card information to the ISP by conventional means, such as by voice telephony, fax transmission or check. In most ISP-end user relationships, the ISP has been given credit card information and this information is on file with the ISP, and avilable to the ISP's computers. In return for receiving payment, the ISP provides a gateway to the. Internet for the end-user's use. The end-user (or subscriber) is provided with software means and identification codes for dialling directly into the ISP's computers. The ISP's computers assign an Internet Protocol (hereinafter “IP”) address to the subscriber for use during the particular on-line session in progress. The subscriber's computer transmits messages which are received by the ISP computer and relayed through the IP...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com