Method for negotiating key share between user and peripheral apparatus
A peripheral device and shared key technology, applied in key distribution, can solve problems such as encrypted transmission, difficult information, impossible shared key of peripheral devices, etc., and achieve the effect of preventing tampering or stealing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
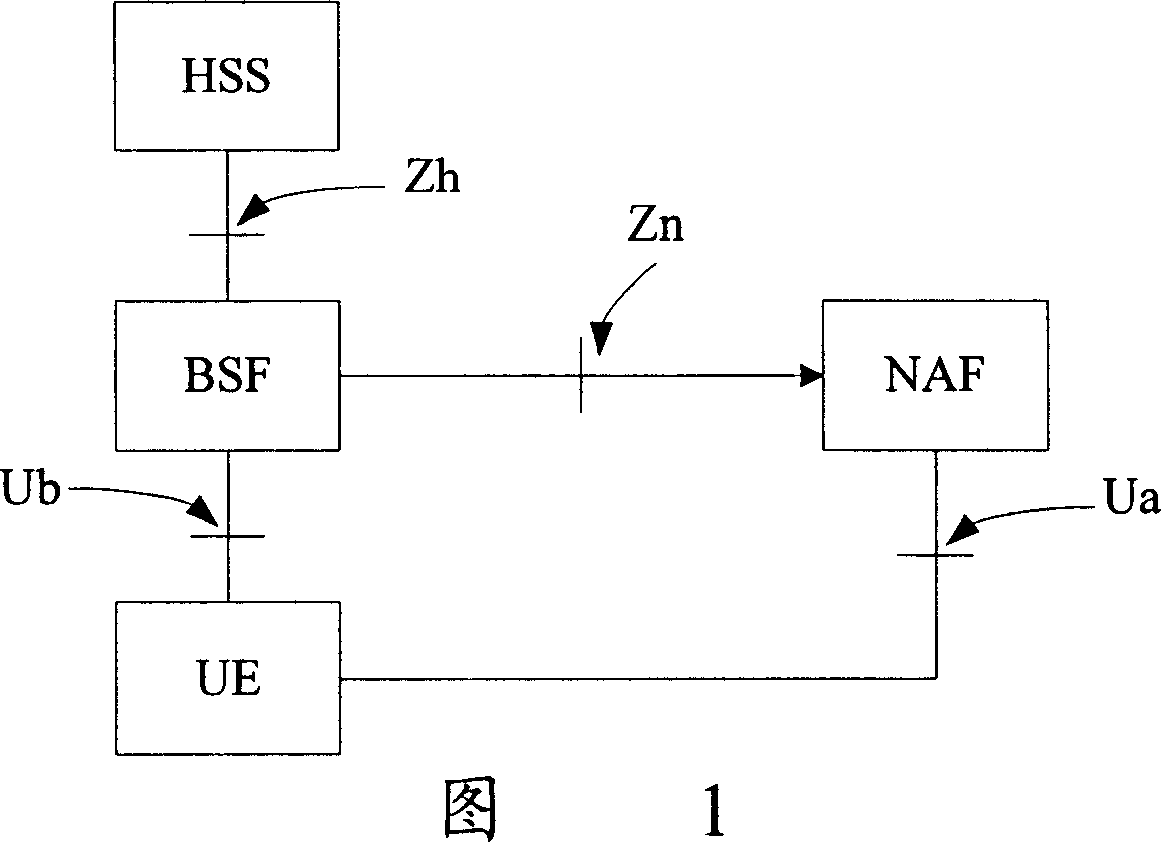
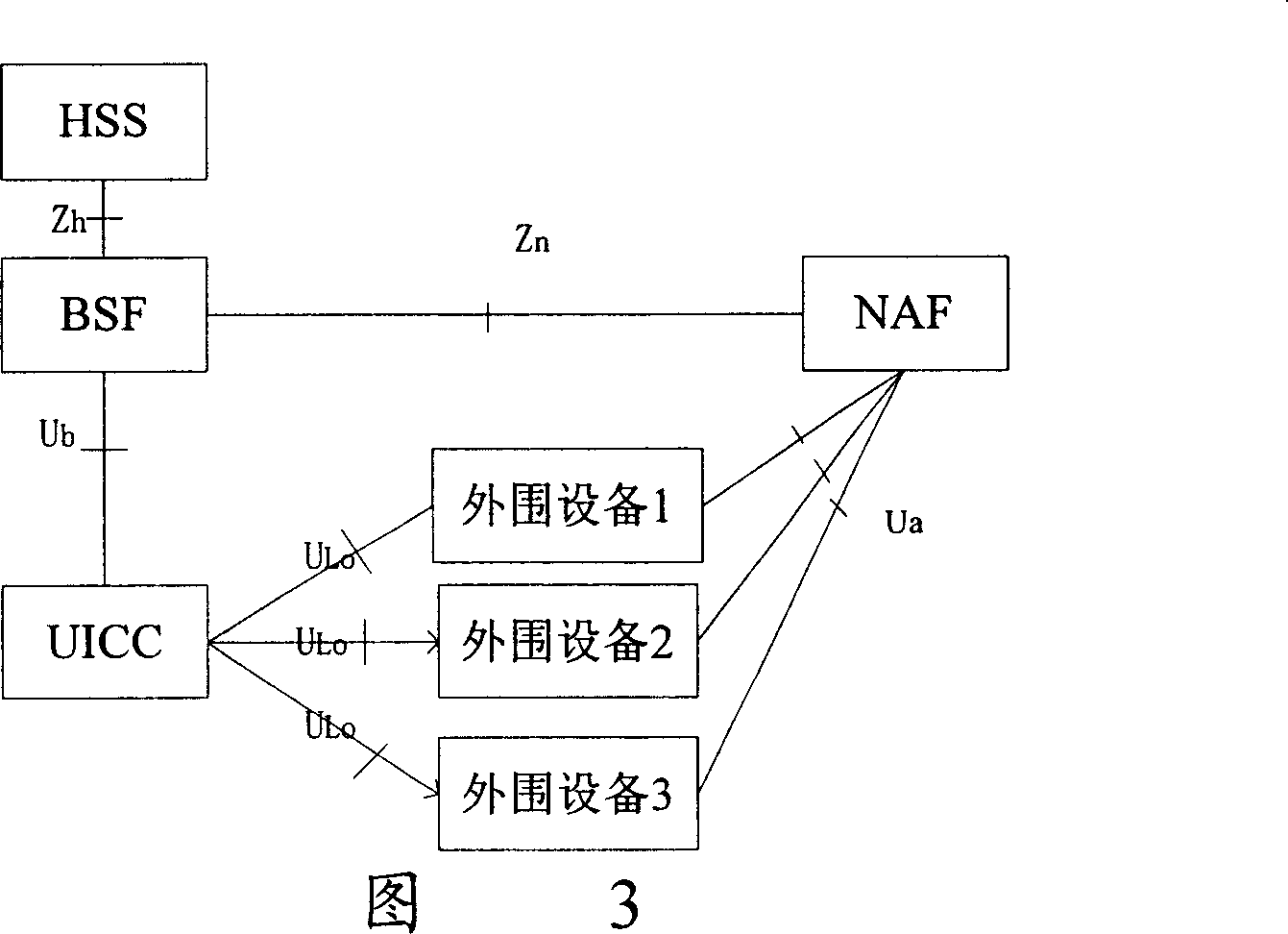
[0064] Referring to FIG. 4 below, the flow chart of the first embodiment of the present invention using GAA to realize the key negotiation between the UE and the peripheral device, wherein, the NAF is used as the key server to negotiate the local interface shared key Ks_Local between the UE and the peripheral device, And the local interface shared key Ks_Local is distributed to peripheral devices by NAF. Among them, when the NAF communicates with the peripheral device, the public key / symmetric key of the peripheral device can be used for integrity and digital signature protection, and the secret data sent by the NAF to the peripheral device can be protected by a random key generated by the NAF, while The transmission of the random key needs to be encrypted and protected with the public key / symmetric key of the peripheral device.
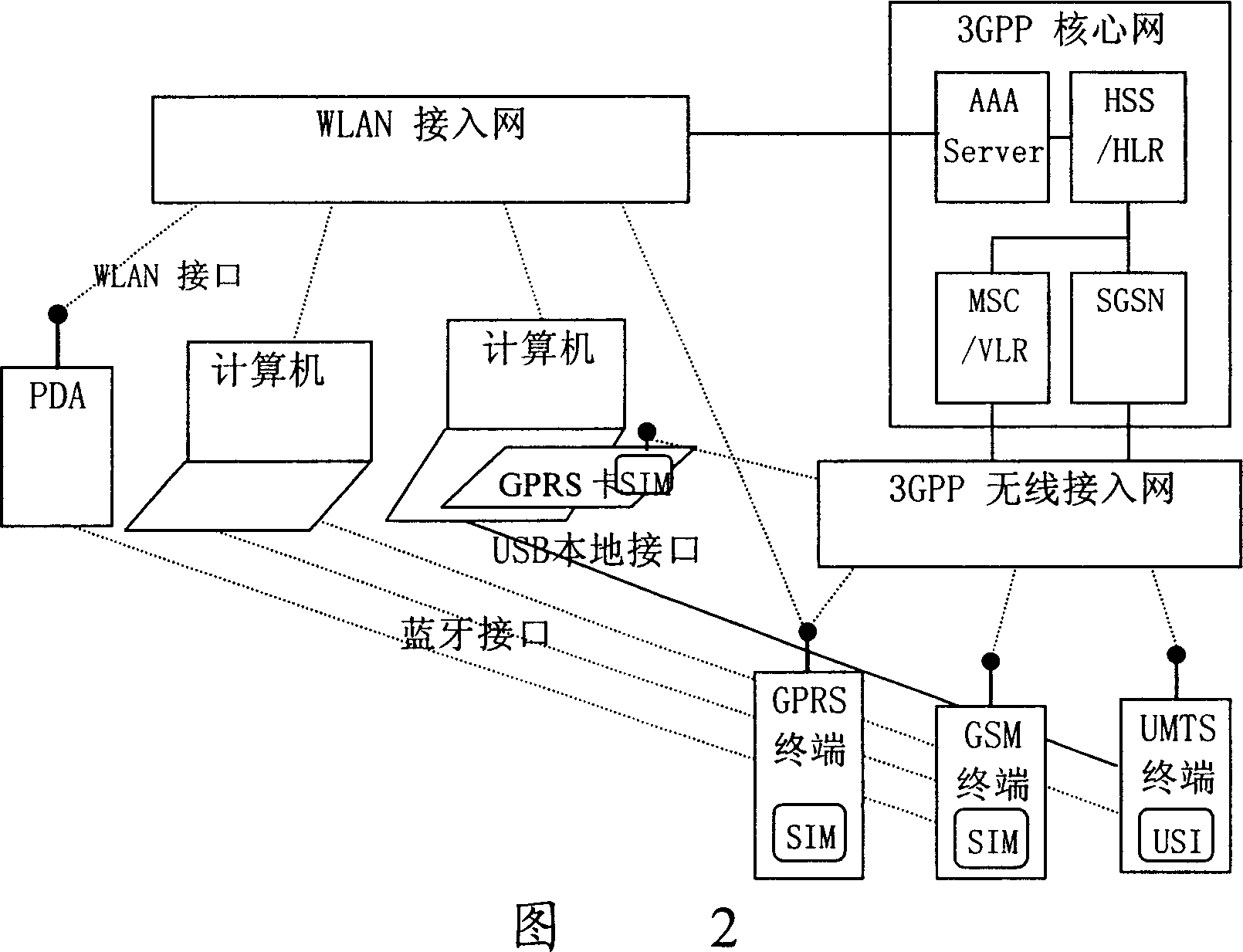
[0065] In this embodiment, the shown UE and the peripheral device belong to the same user. Taking the use of UICC on the UE as an example, the prese...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com