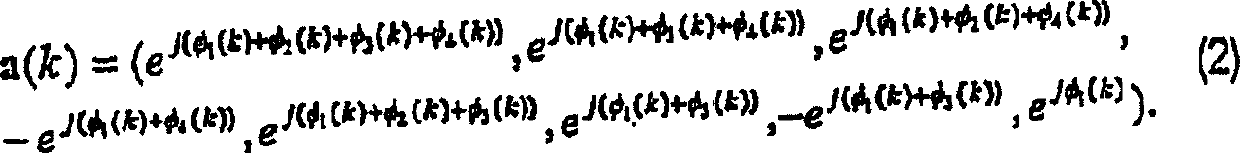Bidirectional turbo ISI canceller-based DSSS receiver for high-speed wireless LAN
A technology of receivers and cancellers, applied in the direction of transmission systems, electrical components, etc., can solve the problem of not being able to suppress the preceding ISI
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] 1(a) and 1(b) are block diagrams of, for example, a DSSS / CCK communication system that can be used for IEEE 802.11b wireless LAN. As shown in Figure 1(a), first, the scrambler 1 scrambles the source bit (source bit) in the data packet, then, at time k (k=0, 1, ..., k-1), Group them into the k-th octet block 2 (b(k)={b 0 (k), b 1 (k),...b 7 (k)}). Then, according to the DQPSK encoder 3 1 , the first pair (b 0 (k), b 1 (k)) are mapped to different encoded phase angles φ 1 (k), while according to encoder 3 2 、3 3 and 3 4 Natural QPSK encoding within, other bit pairs (b 2 (k), b 3 (k)), (b 4 (k), b 5 (k)), (b 6 (k), b 7 (k)) are mapped to φ 2 (k), φ 3 (k) and φ 4 . Note that these four corners can take values within the set {0, π / 2, π, 3π / 2} respectively. In selector 4, according to the following equation, among the four corners, the natural coded angle φ is used 2 (k), φ 3 and φ 4 Generate 64 base CCK code words c(k)=(c 0(k), c 1 (k),...,c 7 (k)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com