Chaos based robustness invisible implanting and extracting method
A technology of watermark embedding and extraction method, applied in color TV parts, TV system parts, TV and other directions, can solve the problems of easy removal or forgery of watermarks, unsafe watermarks, etc., and achieve easy real-time operation, copyright Protection, security and invisibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
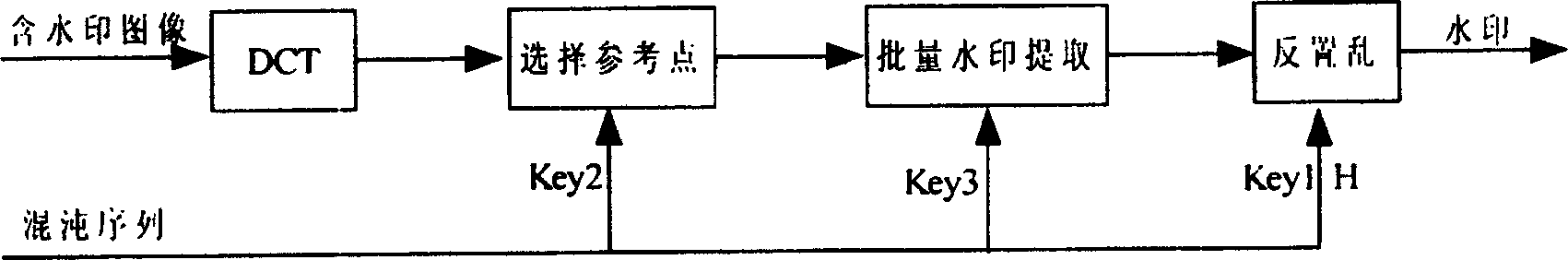
[0025] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0026] 1. Watermark scrambling:
[0027] The binary watermark W with a size of M×N is first reduced to a one-dimensional vector V by row scanning o Given the chaotic initial parameter (Key1), use a one-dimensional discrete chaotic map (such as Logistic-map) to generate a chaotic pseudo-random sequence of length M×N from 1 to M×N, process it with a static Hash table, and get The sequence is a 1~M×N random full permutation {q k}. use {q k}Scramble the watermark to get the out-of-order watermark bit stream
[0028] V p ={v p (k)=v(q k ), k=1, 2,..., M×N}
[0029] Since the chaotic sequence is processed by a static Hash table, the scrambling mapping is a one-to-one mapping.
[0030] 2. Watermark embedding:
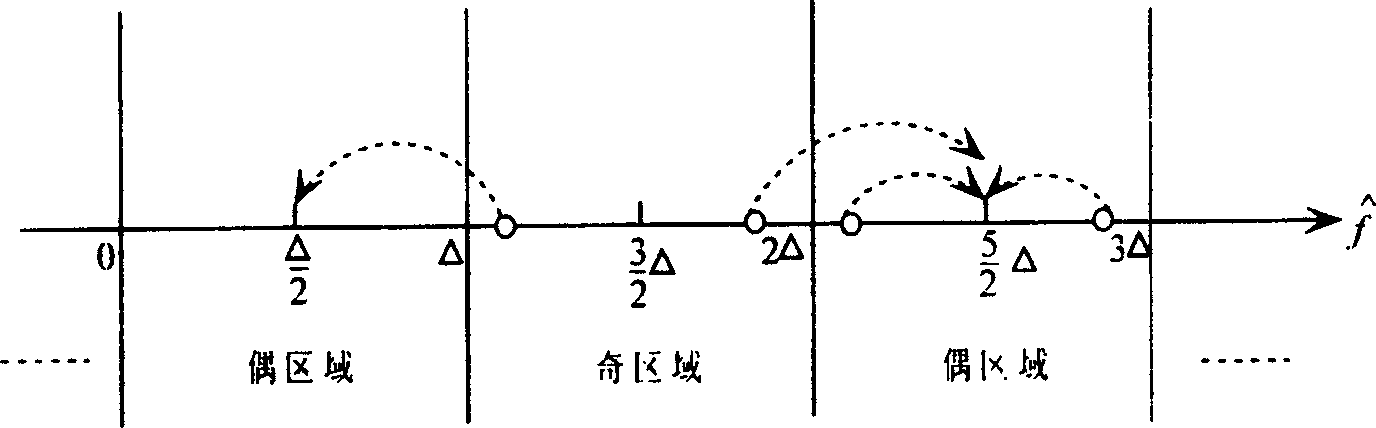
[0031] The original image is first transformed by DCT to obtain the DCT coefficient matrix of the image. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com