API misuse detection method and system based on attention mechanism
A misuse detection and attention technology, applied in neural learning methods, software testing/debugging, biological neural network models, etc., can solve problems such as different degrees of interdependence, inconsistent contributions, misuse of the first API, etc. To achieve the effect of fast training convergence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
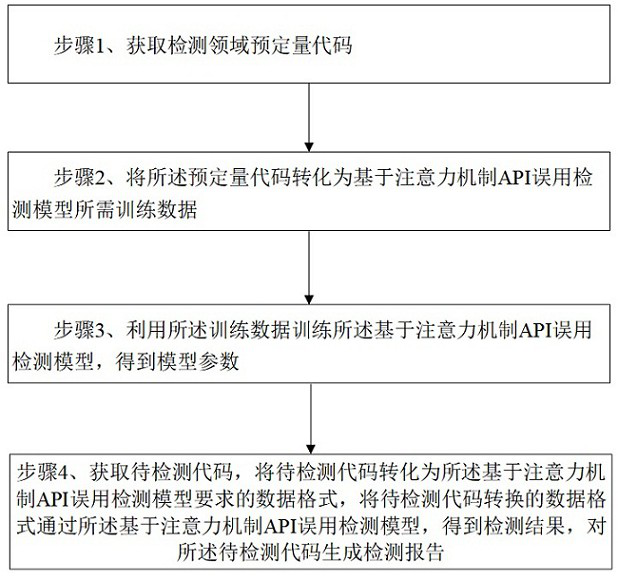
[0054] According to an embodiment of the present invention, as figure 1 As shown, an attention mechanism-based API misuse detection method is proposed, which includes the following steps:
[0055] Step 1. Obtain a predetermined amount of code in the detection field;
[0056] Step 2, converting the predetermined amount of code into training data required for the misuse detection model based on the attention mechanism API;
[0057] According to an embodiment of the present invention, the code contains the following key information: method name (such as a callable method or function in an open source framework), development language keywords (such as while, for, do, foreach, try, catch, etc.) , the variables in the method (such as integer variables, global variables, etc.), extract the key information in a piece of code in order, and organize them into a tuple, which contains all the key information of the piece of code.
[0058] For example the following code:
[0059] "whil...
Embodiment 2
[0086] According to an embodiment of the present invention, an attention mechanism-based API misuse detection system is proposed, including:
[0087] The code acquisition module is used to acquire the predetermined amount of codes in the detection field;
[0088] a conversion module, for converting the code into the training data required for the misuse detection model based on the attention mechanism API according to the obtained code;
[0089] a training module, configured to train the API misuse detection model based on the attention mechanism by using the training data to obtain the model parameters;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com