SPI data transmission method
A data transmission method and data technology, applied in the field of communication, can solve problems such as data packet loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
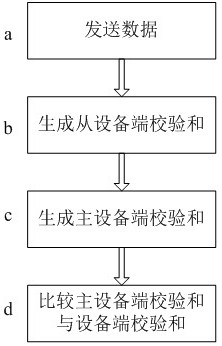
[0032] like figure 1 As shown, this embodiment discloses an SPI data transmission method, which is used for communication between a master device and a slave device through SPI, and includes the following steps:
[0033] a. The master device sends the first data to the slave device, and locally stores the first data in the master device;
[0034] b. After receiving the received value of the first data from the slave device, send the second data associated with the received value of the first data to the master device; The rule calculation generates the third data, and sends the third data to the master device;
[0035] c. After receiving the received value of the second data and the received value of the third data, the master device calculates the received value of the first data and the second data according to the predetermined arithmetic rule to generate the fourth data;
[0036] d. Comparing the received value of the third data with the fourth data, when the received va...
Embodiment 2
[0042] The difference between this embodiment and Embodiment 1 is that the predetermined operation rules adopted are as follows:
[0043] The result generated after the 8-bit data is XORed with the upper 8 bits and the lower 8 bits of the 16-bit data, respectively, is ANDed with 0x400.
Embodiment 3
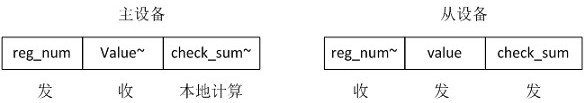
[0045] like figure 2 As shown, on the basis of Embodiment 2, this embodiment discloses an example of SPI data transmission, which is as follows:
[0046] Master A and slave B communicate through SPI, using the same clock, master A sends 8bit required register information reg_num to slave B, and master A saves the sent information locally, after slave B receives the 8bit information reg_num~, Send the register information required by host A to the host 16bit-value, and then calculate a checksum check_sum by itself and send it to host A. The specific calculation method is as follows:
[0047] The 8-bit information reg_num received by slave B~ XOR the upper 8 bits of the value, then XOR the lower 8 bits of the value, and finally add 0x400 as the label bit, as follows:
[0048] check_sum=(reg_num~⊕valueH8⊕valueL8)&0x400
[0049] In the above formula: valueH8 is the upper 8 bits of the value, and valueL8 is the lower 8 bits of the value.
[0050] After the host receives the 16b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com