Fine-grained multi-user security searchable encryption method in cloud-edge collaborative environment
A technology of collaborative environment and encryption method, applied in the field of multi-user secure searchable encryption, to achieve the effect of reducing computing cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be further described below with reference to the accompanying drawings and embodiments.
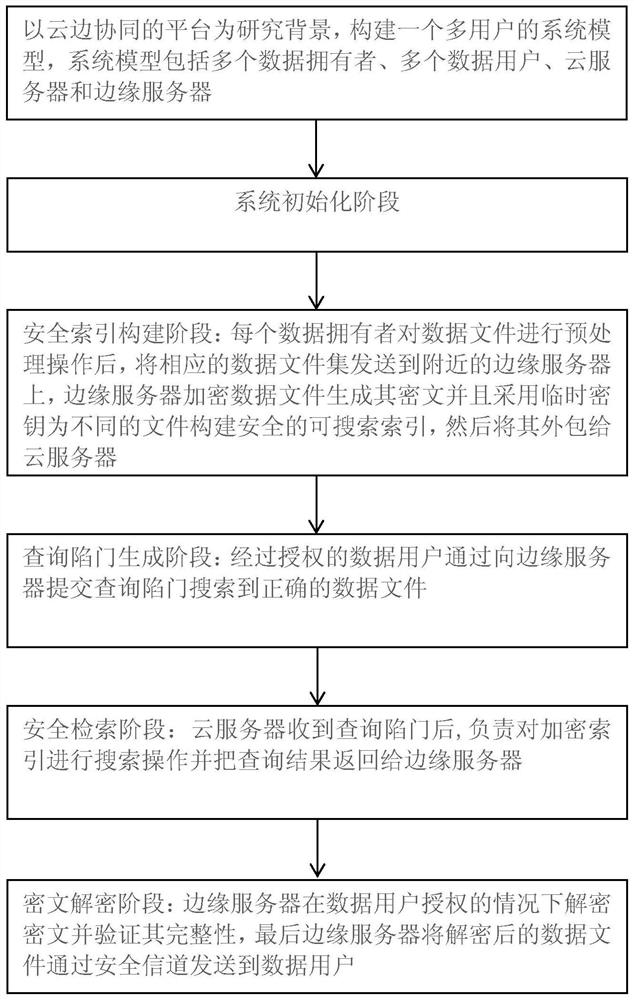
[0048] like figure 1 As shown, a fine-grained multi-user secure searchable encryption method in a cloud-edge collaborative environment, the steps are:
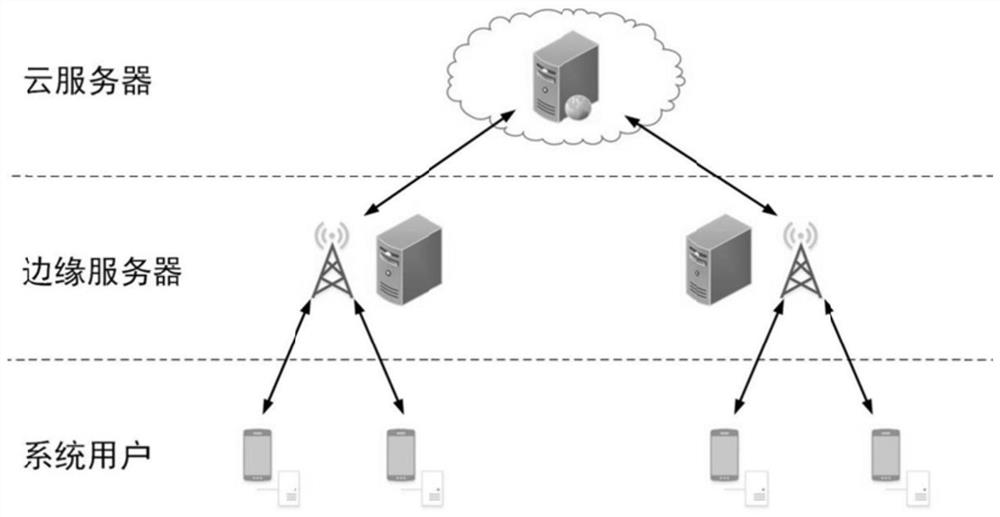
[0049] Step 1: The present invention takes the cloud-edge collaboration platform as the research background, and constructs a multi-user system model. The system model includes multiple data owners, multiple data users, cloud servers and edge servers. figure 2 As shown, the cloud server is defined as an “honest but curious” semi-trusted threat entity, and the edge server is defined as a trusted entity.
[0050] The second step is the system initialization phase.
[0051] The specific steps of the system initialization phase are:
[0052] Input a security parameter to the system model, output the public parameters of the system model, and construct the working environment: set G 1 , G 2 are two multi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com