Botnet risk assessment method and device
A risk assessment and botnet technology, applied in secure communication devices, digital transmission systems, instruments, etc., can solve problems such as single means, difficulty in encrypting traffic, and lack of botnet risk assessment methods and devices, etc., to improve comprehensive benefits , high commercial value, and easy to use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] In order to better clearly express the technical solution of the present invention, the present invention will be further described below in conjunction with the accompanying drawings.
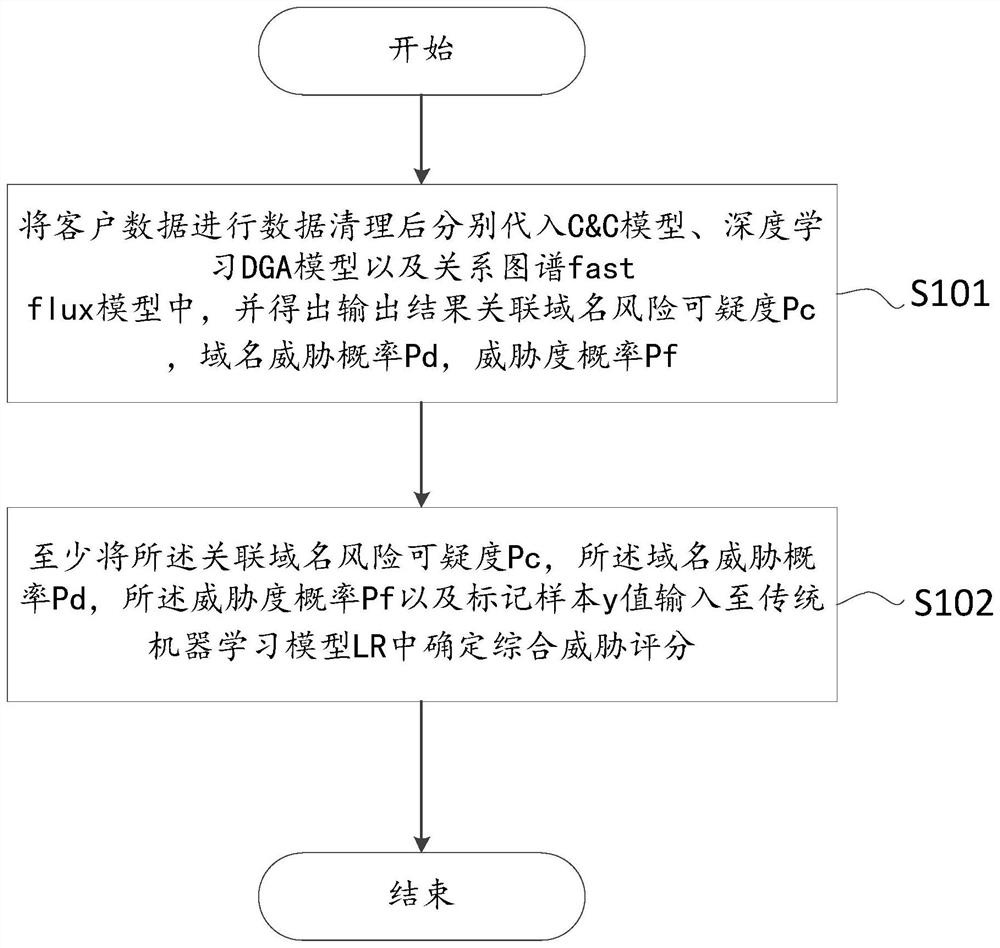
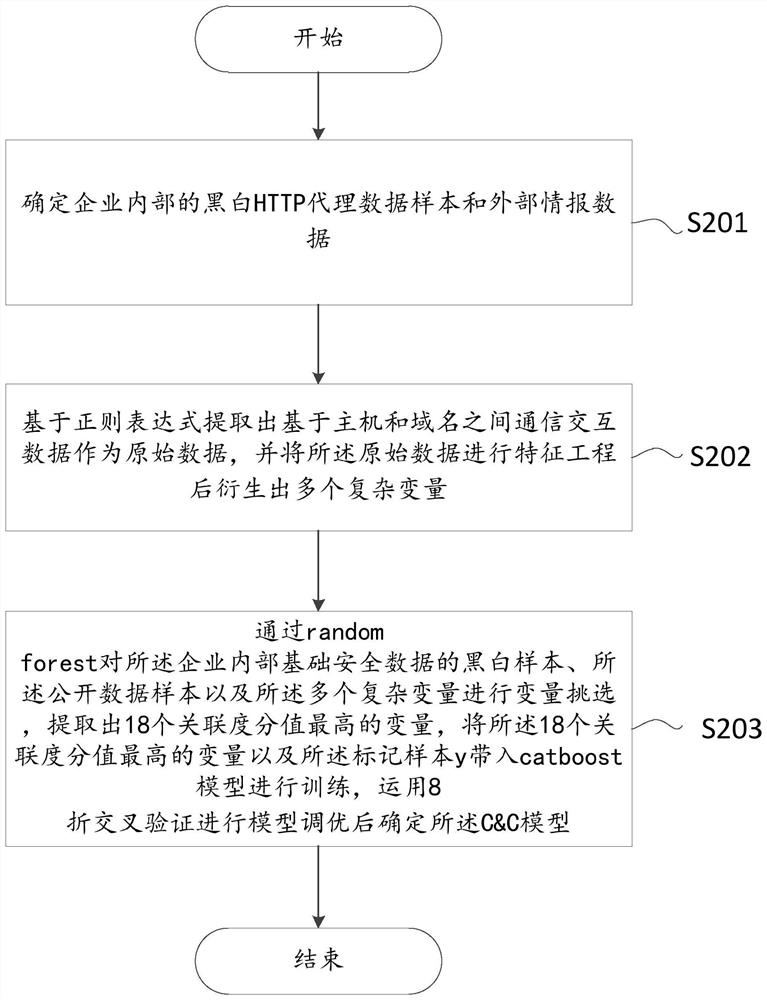
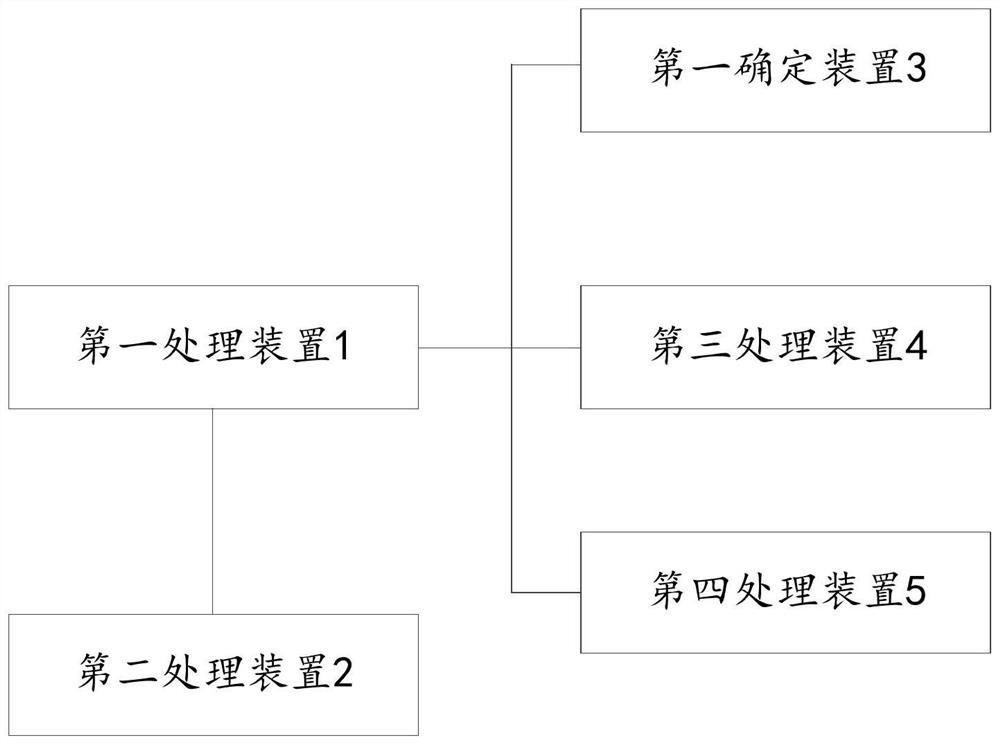
[0038] figure 1 Showing a specific implementation of the present invention, a schematic flow chart of a botnet risk assessment method. The present invention discloses a botnet risk assessment method, which establishes a multi-scenario multi-scenario fusion based on internal basic security data and public data samples of the enterprise. Dimensional model, combined with big data security platform for real-time and effective assessment of security risks, the present invention is a C&C botnet risk assessment method and system based on big data AI platform, and its characteristics are: based on internal basic security data and public data samples of the enterprise , establish a fusion of multi-scenario and multi-dimensional models, combined with a big data security platform for real-time and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com