Power data privacy protection system, implementation method thereof and encryption attribute revocation method
A privacy protection system and power data technology, applied in the field of power data privacy protection system, to achieve the effect of protecting private data, protecting privacy, and preventing malicious access
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
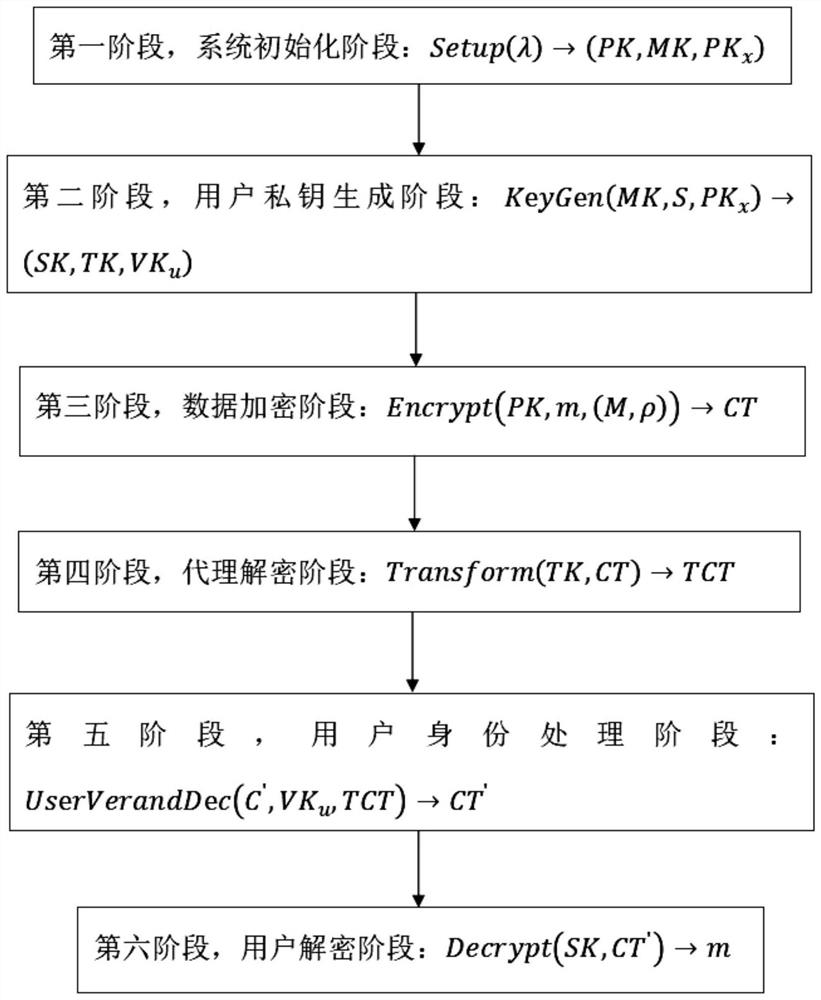
[0025] The present invention will be described in detail below in conjunction with the accompanying drawings and specific embodiments. This embodiment is carried out on the premise of the technical solution of the present invention, and detailed implementation and specific operation process are given, but the protection scope of the present invention is not limited to the following embodiments.
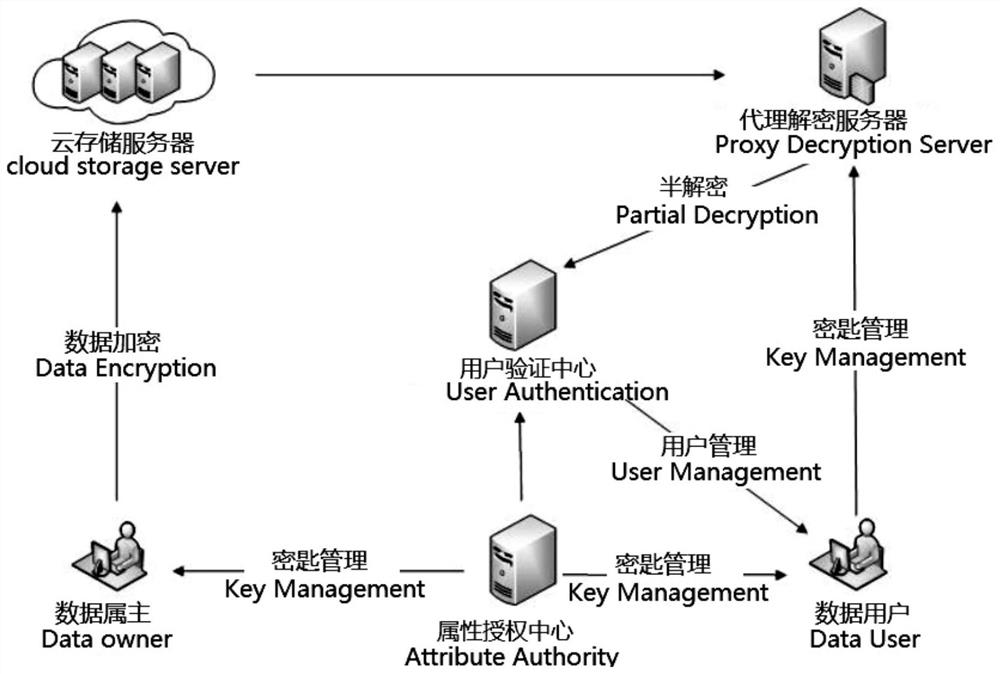
[0026] Such as figure 1 The model diagram of the power data privacy protection system shown includes six entities: attribute authorization center, power data owner, power data user, cloud storage server, proxy decryption server, user verification center, and the six entities communicate through the Internet;
[0027] Attribute authorization center AA: used to generate system master key MK, system public key PK, user identity key VK u , user private key SK and set version PK for user attributes x , and PK, PK x public in the system, the VK u , SK is distributed to corresponding use...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com