Method, system and device for security authentication of Internet of Vehicles communication based on national secret algorithm
A national secret algorithm and security authentication technology, which is applied in the field of vehicle network communication security authentication based on the national secret algorithm, can solve problems such as network delay, resource waste, and imperfect roadside facilities, so as to prevent message replay attacks and ensure confidentiality Sexuality, the effect of reducing the number of times
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
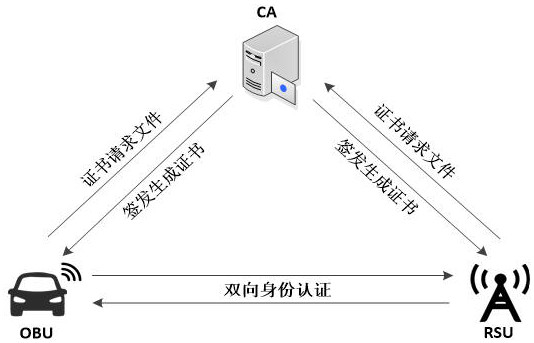
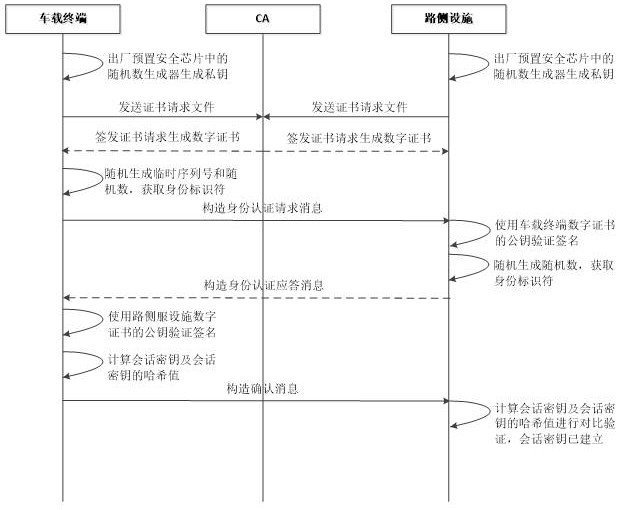
[0070] An embodiment of the present invention is a security authentication method for Internet of Vehicles communication based on a national secret algorithm. Based on the SM2 digital signature algorithm, the SM2 public key encryption algorithm and the SM3 hash algorithm, the on-board terminals and roadside facilities in the Internet of Vehicles realize the Two-way identity authentication between terminals and roadside facilities, such as figure 1 shown.
[0071] The on-board terminal and the roadside facility are factory-preset with a random number generator in the security chip to generate the private key respectively , , and stored in the storage unit of the security chip, which cannot be acquired by external devices.
[0072] Before the two-way security identity authentication between the vehicle terminal and the roadside facility, the vehicle terminal and the roadside facility respectively send the certificate request file to the CA, and the CA respectively issues th...
Embodiment 2
[0108] Another embodiment of the present invention is a vehicle networking vehicle terminal based on a national secret algorithm, including a random number generation module, a certificate issuance module, an identity authentication message construction module, and an authentication module, such as Figure 5 shown. The vehicle-mounted terminal in this embodiment implements the security authentication method for the vehicle-to-vehicle communication vehicle terminal based on the national secret algorithm described in Embodiment 1, wherein,
[0109] The random number generation module generates a private key through the random number generator in the security chip preset in the vehicle terminal, and stores the private key in the storage unit of the security chip, which cannot be acquired by external equipment;
[0110] The certificate issuing module is used for the vehicle terminal to send the certificate request file to the CA, and to receive the digital certificate generated by...
Embodiment 3
[0114] Another embodiment of the present invention is a vehicle networking roadside facility based on a national secret algorithm, including a random number generation module, a certificate issuance module, an identity authentication message construction module, and an authentication module, such as Figure 5 shown. The roadside facility of this embodiment implements the security authentication method for the roadside facility of the Internet of Vehicles communication based on the national secret algorithm described in Embodiment 1, wherein,
[0115] The random number generation module generates a private key through the random number generator in the security chip preset in the roadside facility, and stores the private key in the storage unit of the security chip, which cannot be acquired by external equipment;
[0116] The certificate issuance module is used for the roadside facility to send the certificate request file to the CA, and to receive the digital certificate gener...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com