Security verification code generation method and system based on track drawing interaction and medium
A security verification code and verification code technology, which is applied in the field of security verification code generation based on trajectory drawing interaction, can solve the problems of increasing the difficulty of human identification, increase the difficulty of cracking, etc., so as to prevent the behavior of machine simulation generation of trajectory and improve security. and correctness, the effect of preventing cracking
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
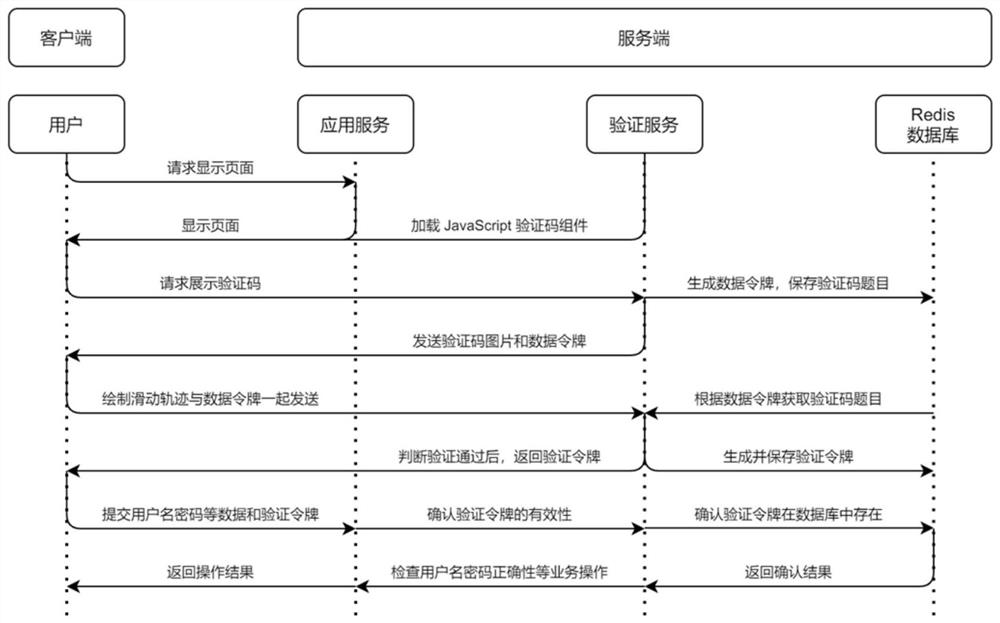
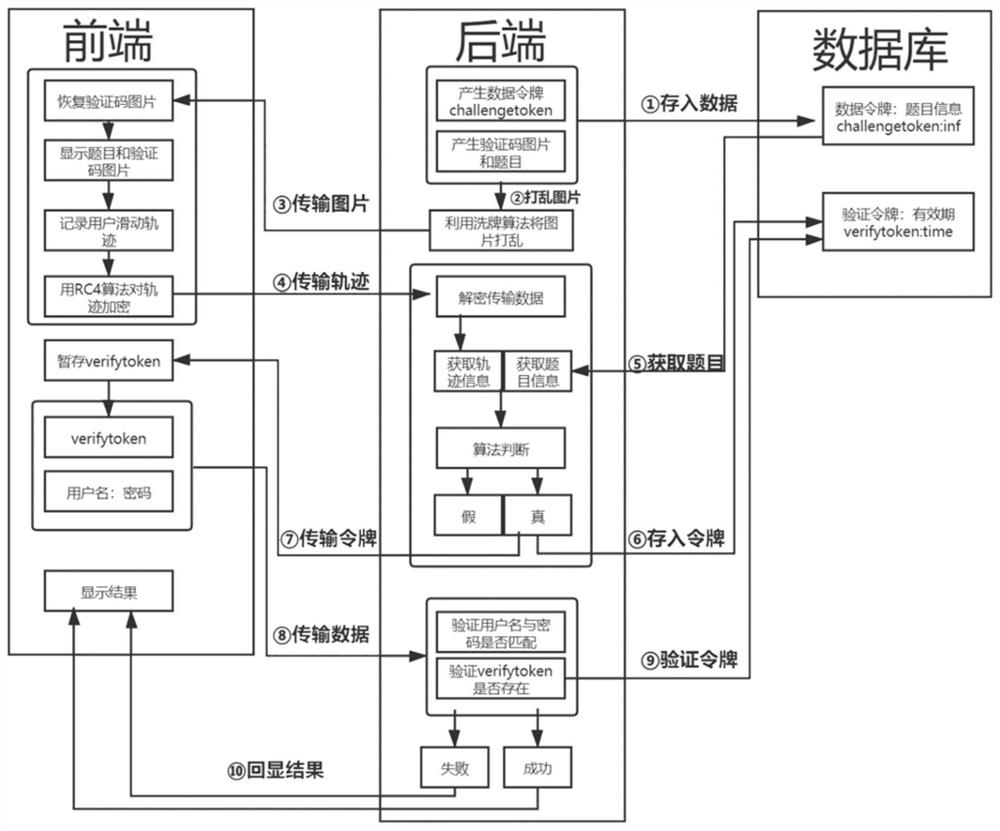
[0055] The solution described in this embodiment proposes a security verification code generation method based on trajectory drawing interaction. Among them, the "title" of the verification code is a word between two and four characters, and the user needs to pass a Sequentially drag the mouse or touch the screen to draw sliding tracks, and connect the given words in order, such as figure 1 shown.
[0056] The solution described in this embodiment mainly includes four roles: user, client, server, and database. The client, server and database communicate through the HTTP protocol, wherein the user is the subject of verification in the present invention; the client is mainly responsible for monitoring and recording user behavior and resisting various attacks against verification codes; the server is mainly responsible for generating verification codes. Code information to verify user behavior; the database is mainly responsible for storing verification code topic data and rela...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com