Service deployment method and device based on K8S, electronic equipment and storage medium
A device and server-side technology, applied in the computer field, can solve data security risks, inability to solve user camouflage, lack of scalability and flexibility, etc., to achieve the effect of improving security, solving security problems, and solving camouflage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach
[0067] Specifically, this implementation mode provides a specific implementation mode for implementing the solution of adding an anti-counterfeiting watermark to the deployment request, and the code is as follows:
[0068]
[0069]
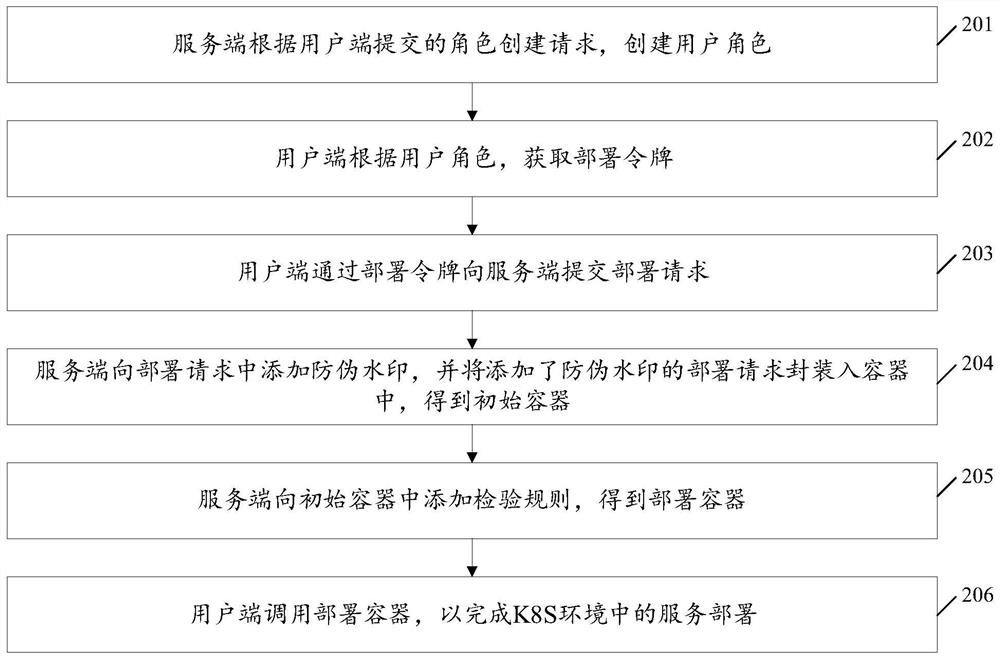
[0070] 205: The server adds inspection rules to the initial container to obtain the deployment container.
[0071] Enterprise big data hadoop applications have security controls on data access. In this embodiment, HMS system (hadoop user system) is used to establish corresponding virtual users for real users who need to access data, and then access hadoop through virtual users Data in a big data cluster. Therefore, user information for deploying applications is particularly important.
[0072] In this embodiment, to prevent user information from being tampered with, that is, it is mandatory to use the virtual user corresponding to the real user to start the container application. For other users, the user who has completely started the con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com