Memory overflow defense method based on pointer encryption mechanism and RISC-V coprocessor
A RISC-V and coprocessor technology, applied in the protection of internal/peripheral computer components, platform integrity maintenance, etc., can solve problems such as the inability to defend against overflow attacks, the impact of program operation efficiency, etc., to reduce impact and improve security performance Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] In order to make the purpose, technical solutions and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the examples and accompanying drawings. As a limitation of the present invention.
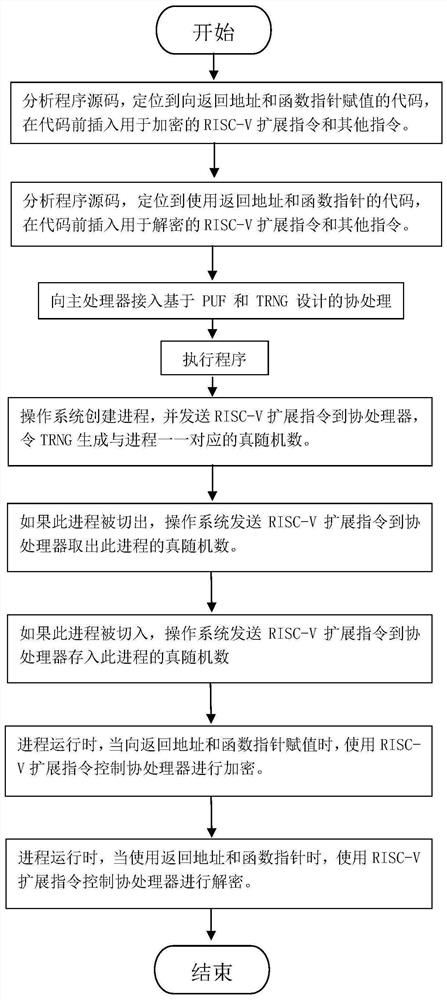
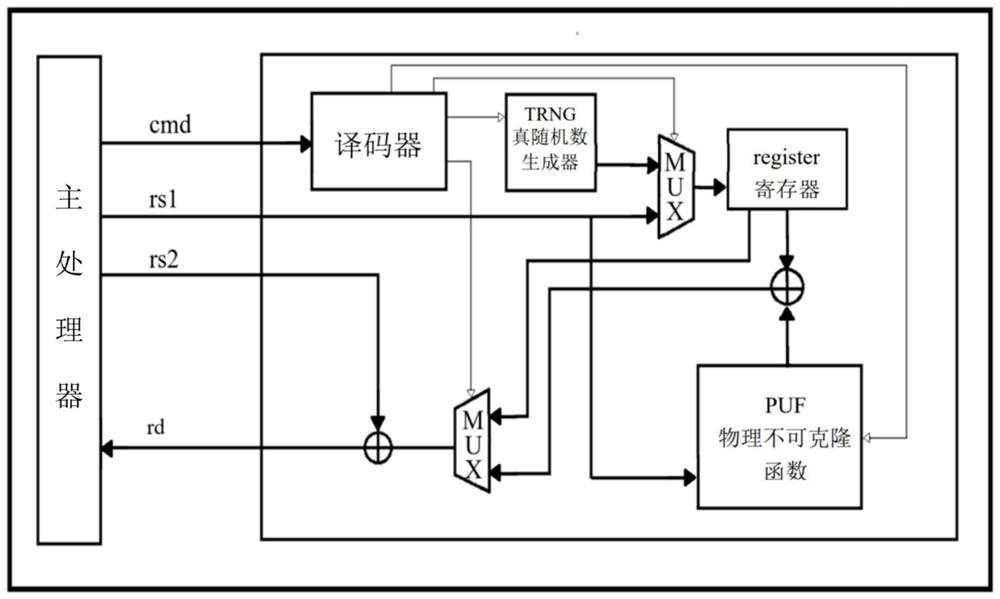
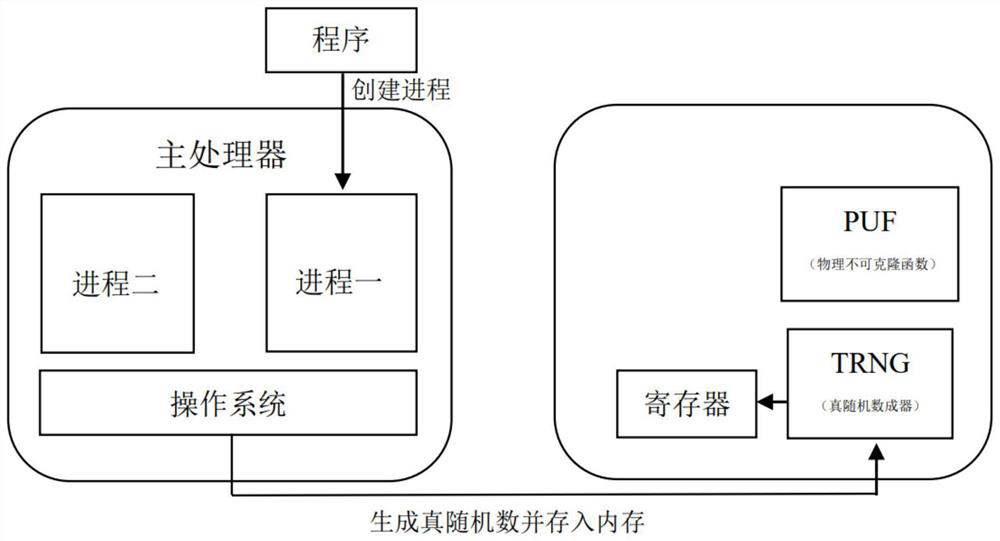
[0048] This embodiment uses the ROCC interface of RocketChip to access the coprocessor written in Chisel hardware language, realizes the memory overflow defense method based on the pointer encryption mechanism and the RISC-V coprocessor, and uses the C++cycle-accurate implemented by RocketChip The emulator conducts safety and efficiency tests. The concrete flowchart of embodiment is as figure 1 As shown, it mainly includes the following steps:
[0049] 1) Analyze the source code of the program, locate the code that assigns a value to the return address (ra), insert the RISC-V extension instruction that encrypts ra before the code—instruction 4, locate the code that uses ra, and insert the RISC-V that decry...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com