Method, system and equipment for enhancing MQTT protocol identity authentication by using symmetric cryptographic technology
A technology of identity authentication and symmetric cryptography, which is applied in the field of using symmetric cryptography to enhance MQTT protocol identity authentication, to achieve the effects of easy implementation of development technology, improved security performance, and strong versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
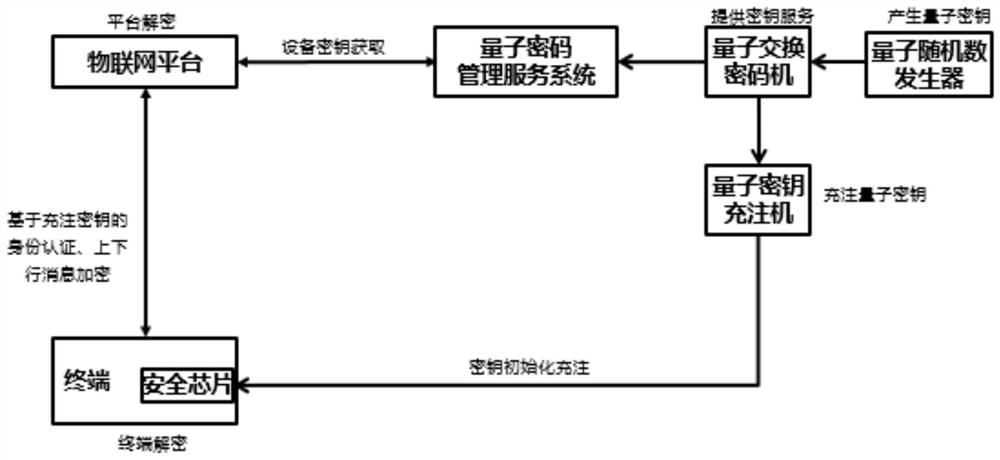
[0078] The invention provides an identity authentication method using symmetric cryptography to enhance the MQTT protocol, which is applied to an identity authentication system. The identity authentication system includes a quantum random number generator, a quantum exchange cipher machine, a quantum key filling machine, and a quantum cryptography management service. system, IoT terminal, security key chip, and IoT platform.
[0079] The Internet of Things terminal can be a publisher in the MQTT protocol, or a subscriber in the MQTT protocol. The IoT platform can be a broker in the MQTT protocol. During the process of IoT terminal accessing the IoT platform, the IoT platform needs to authenticate the IoT terminal. If the authentication is passed, the IoT terminal can transmit business data with the IoT platform. For example, the IoT terminal can pass the IoT The platform publishes news, and can also subscribe to news published by other IoT terminals through the IoT platform. ...
Embodiment 2
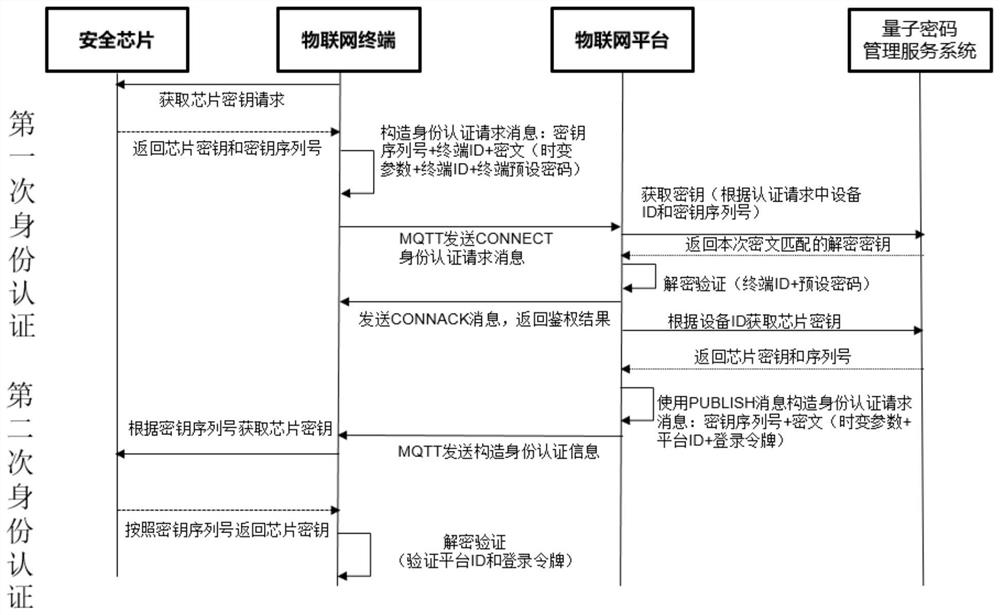
[0119] The present invention provides a method of using symmetric cryptography to enhance MQTT protocol identity authentication, which is applied to terminals of the Internet of Things, such as Image 6 with Figure 7 shown, including:
[0120] First authentication:
[0121] S31. The terminal acquires a key request in the security chip, and the security chip returns the key B of the chip key serial number Z;
[0122] S32. The terminal constructs an initial identity authentication request message according to the content format of the MQTT connection message Connect: key serial number Z+terminal ID+ciphertext (time-varying parameter+terminal ID+terminal preset password), and the encryption method of the ciphertext can use a symmetric algorithm such as SM4 Complete, the encryption key is the key B taken out from S1;
[0123] S33. The terminal sends the constructed identity authentication request message to the proxy address exposed by the Internet of Things platform;
[0124...
Embodiment 3
[0130] The present invention provides a method of using symmetric cryptography to enhance MQTT protocol identity authentication, which is applied on the Internet of Things platform, such as Figure 8 with Figure 9 shown, including:
[0131] First authentication:
[0132] S301. The IoT platform obtains the key B' symmetrical to the key B from the quantum cryptography management service system according to the terminal ID and the key serial number Z in the initial identity authentication request message sent by the IoT terminal;
[0133] S302. The Internet of Things platform receives the key B' returned by the quantum cryptography management service system, and the Internet of Things platform uses the key B' to decrypt the initial identity authentication request message, and obtains the decrypted ciphertext: time-varying parameter + terminal ID+terminal preset password, and compare the decrypted terminal ID and terminal preset password with the terminal ID stored in the backg...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com