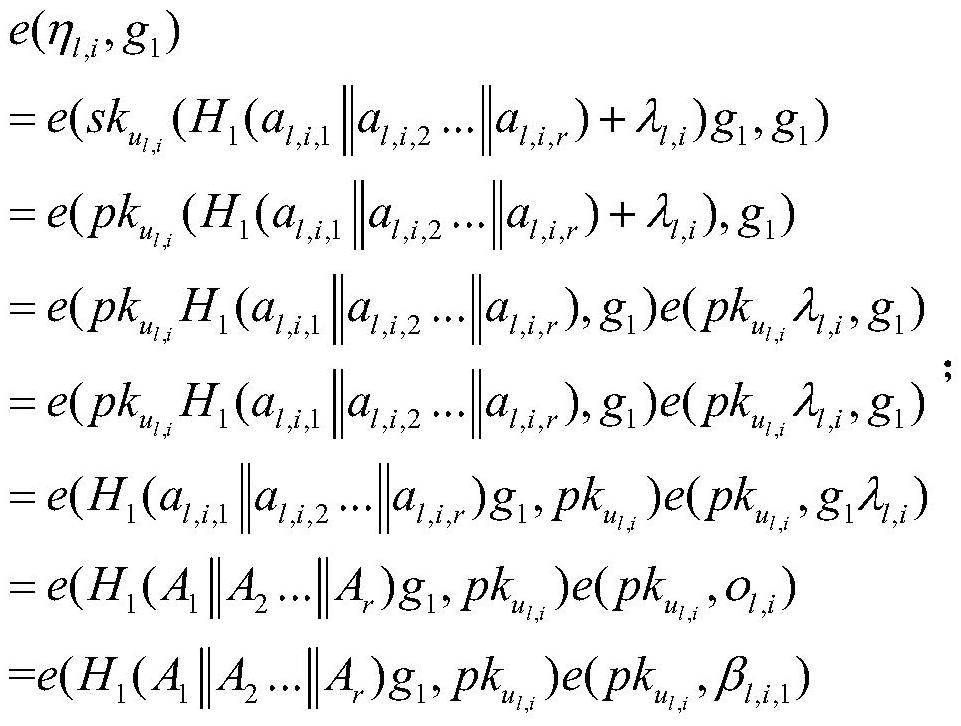Hierarchical dynamic group key negotiation method based on privacy protection
A technology for group key negotiation and privacy protection, applied in the field of hierarchical dynamic group key negotiation based on privacy protection, which can solve problems such as reducing computing and communication overhead, exposing personal identity information, and inability to flexibly protect sensitive data. , to achieve the effect of improving security, protecting personal privacy, and ensuring reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
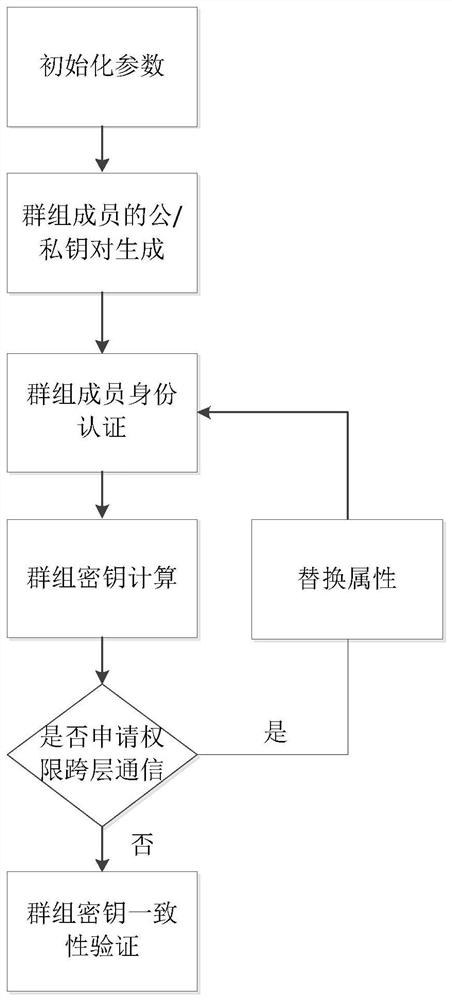
[0081] In the case of complex multi-party communication, the authentication center CA in the group needs to authenticate the terminal members of the communication, but when providing identity information, the identity information is easily leaked or stolen. For security reasons, while communicating entities with multi-party authentication, it is necessary to protect the privacy of personal identities. When sharing information, it is also necessary to ensure the confidentiality, integrity and anti-disclosure of communication information, and only members who comply with the authority policy can communicate. Aiming at this application background, the present invention provides a hierarchical dynamic group key agreement method based on privacy protection, such as figure 1 As shown, the steps are as follows: ① The terminal members participating in the group key negotiation first perform parameter initialization and generate their own public / private key pairs respectively; ② The hi...
Embodiment 2
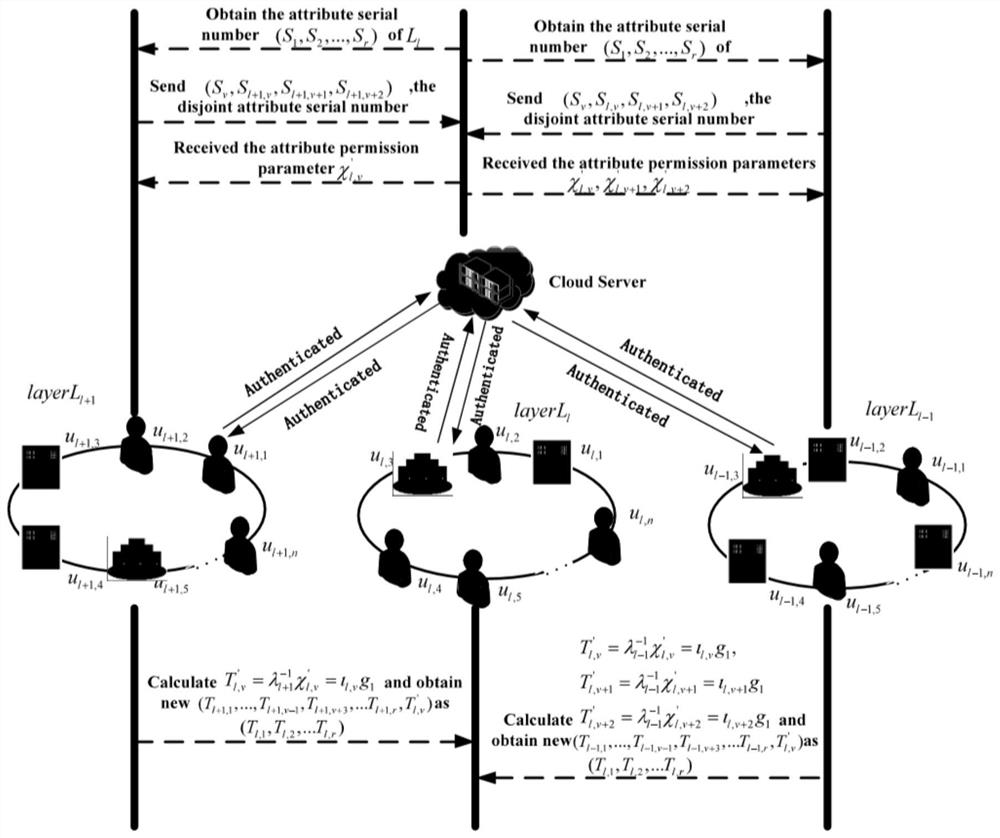
[0126] A privacy-preserving hierarchical dynamic group key agreement method, such as figure 1 As shown, in order to illustrate the content and implementation method of the present invention, a specific embodiment is provided. In this embodiment, for the convenience of example description, a 3-layer group is set up for group key negotiation, each group has 10 members, and the entity set of these 10 members is expressed as S={S 1 ,S 2 ,...,S 10},S 1 ={u 1,1 , u 1,2 ,...,u 1,10},S 2 ={u 2,1 , u 2,2 ,...,u2,10}, S 3 ={u 3,1 , u 3,2 ,...,u 3,10}, the entity set of terminal members is expressed as The identity set of corresponding group members is expressed as The authentication center CA defines the attribute set of all terminal members as ATTR={A 1 ,A 2 ,A 3}, the ordered attribute set corresponding to group members is The purpose of introducing details in this embodiment is not to limit the scope of the claims, but to help understand the specific implementati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com