Personal information protection system and method
An information protection and information binding technology, applied in the field of information security, can solve the problem of illegally obtaining user network identity information, and achieve the effect of reducing operation steps
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
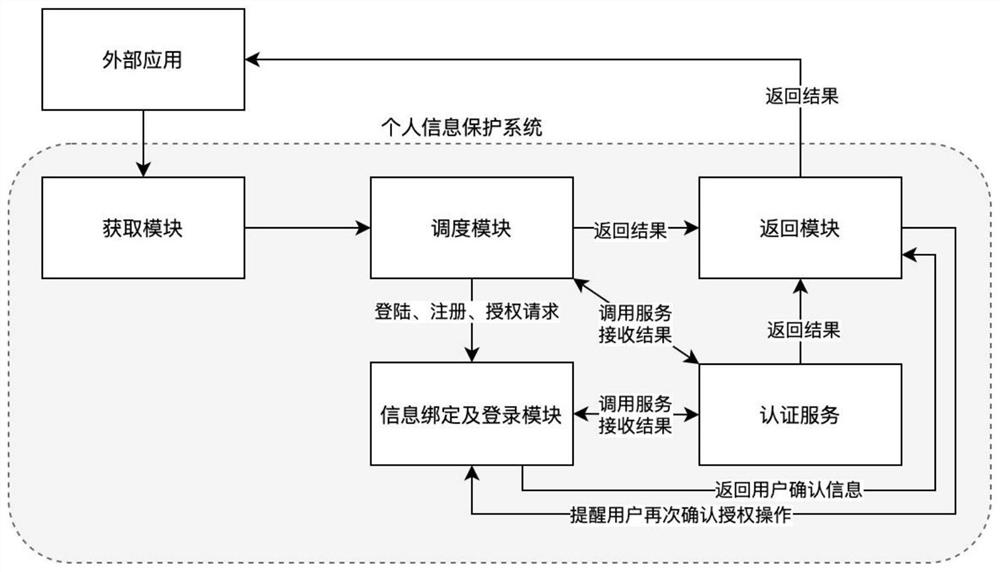
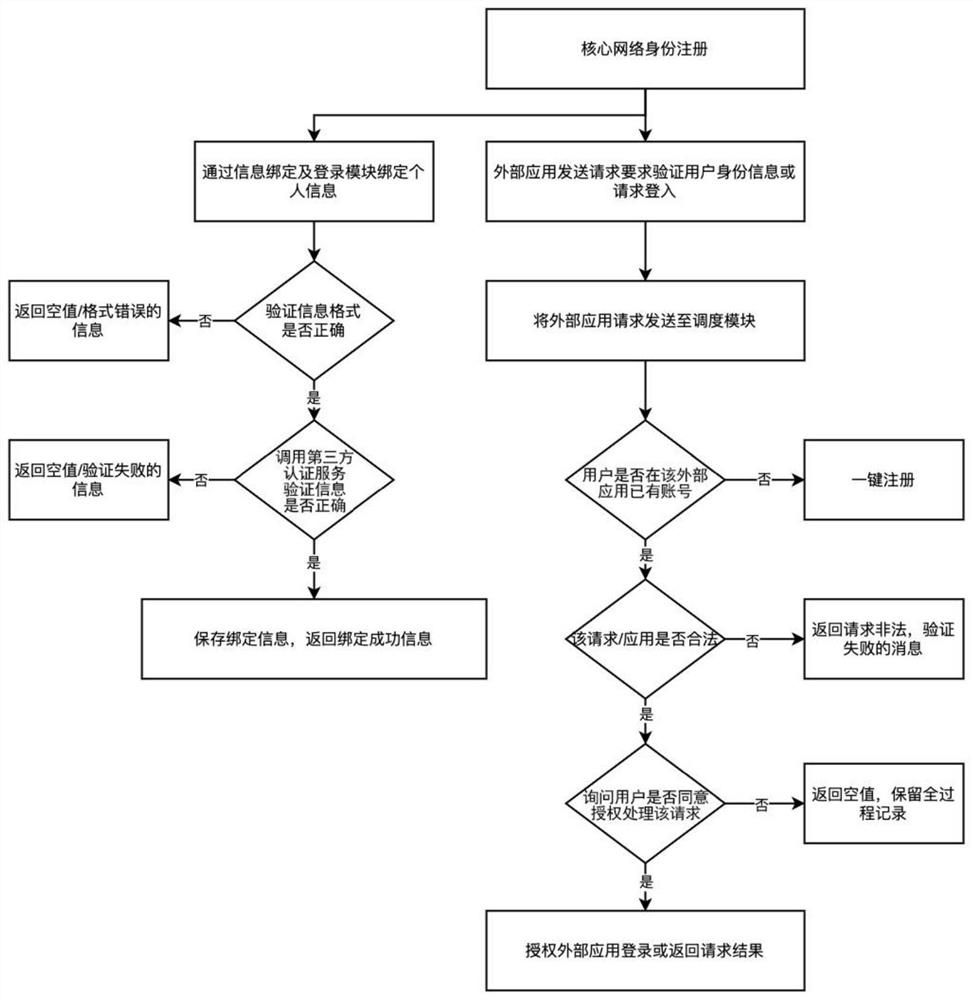
[0050] Users use the system of the present invention (extended based on the existing Easy Login system, which may also be referred to as the Easy Login System hereinafter, and the information binding and login modules are also expanded from the existing Easy Login App, which may also be referred to as Login below. Easy App) when registering an account on all websites or application servers and application devices, the user's personal information data, except for the account number and password generated by registration, will no longer be handed over to the website or application server for storage and processing, but will be kept In this system (the account password is encrypted and stored on the personal terminal of the system, that is, in the information binding and login module), the server of the website or application can request the user to authorize through the system when necessary, and then from Obtain the required information on the personal terminal of the system, or...
Embodiment 2
[0056] The following is an example of a specific application:
[0057] Step 1. The webpage of the third-party application website Wislab displays a button "Certify whether you are a student of Guanggong". After the user clicks, the server of the Wislab website constructs an authentication request and sends the authentication request to the Easy Login App.
[0058]Step 2. Log in to Easy App (information binding and login module) to display 3 options: "Authorization", "Rejection", and "Rejection and Complaint".
[0059] Step 3. If the user chooses "Authorization", send the authentication request to the student identity authentication server provided by the Academic Affairs Office of Guanggong University, obtain the authentication result, record it in the log, and stop. After receiving the authentication result from the third-party application website Wislab website, follow-up corresponding processing.
[0060] Step 4. If the user chooses "reject", the rejection result is fed bac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com