Web terminal protection method and system based on port proxy and storage medium
A protection system and terminal technology, applied in transmission systems, electrical components, etc., can solve the problems of code auditing and code repairing for a long time, and the firewall system cannot quickly respond to and counteract 0DAY vulnerabilities, and achieve the effect of ensuring security and legitimacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
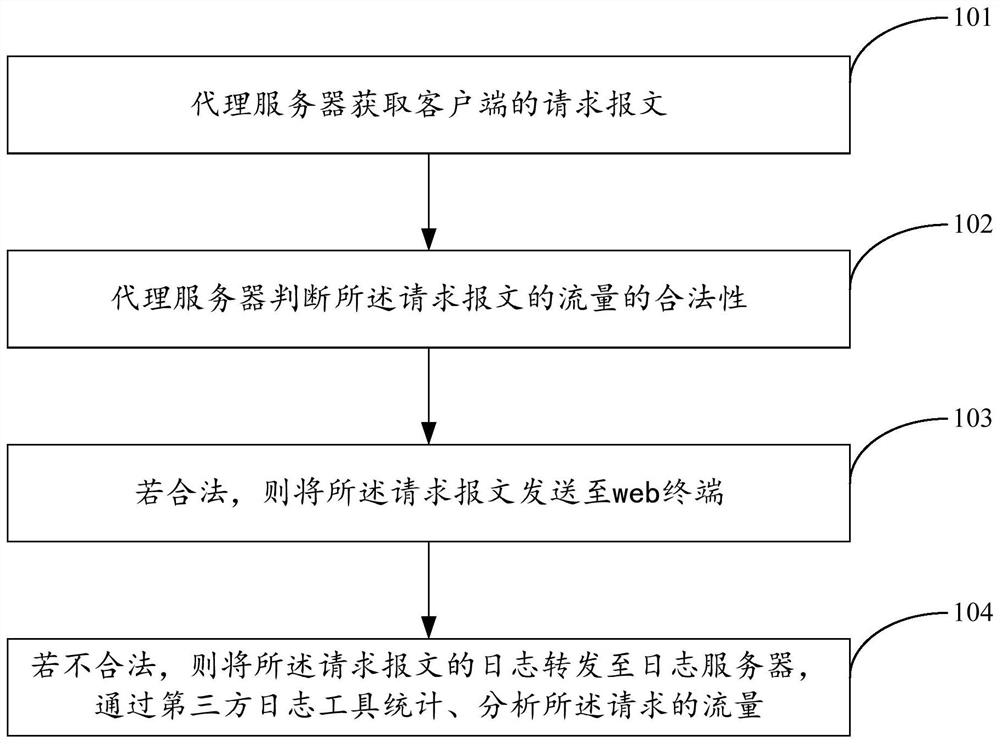
[0034] figure 1 It is a flow chart of a port proxy-based web terminal protection method provided by the embodiment of the present invention, and the method can be executed by the port proxy-based web terminal protection system provided by the embodiment of the present invention. refer to figure 1 , the method may specifically include the following steps:
[0035] S101. The proxy server obtains the request message of the client;
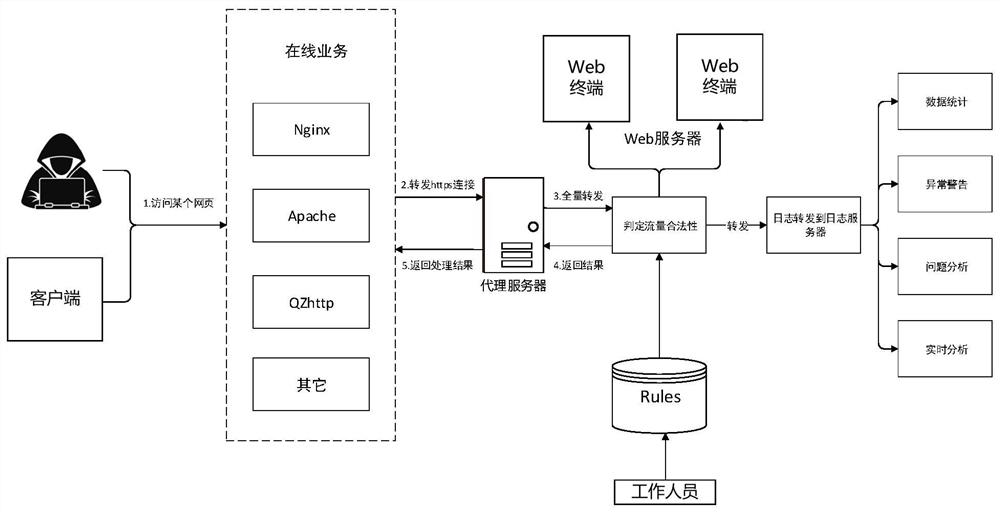
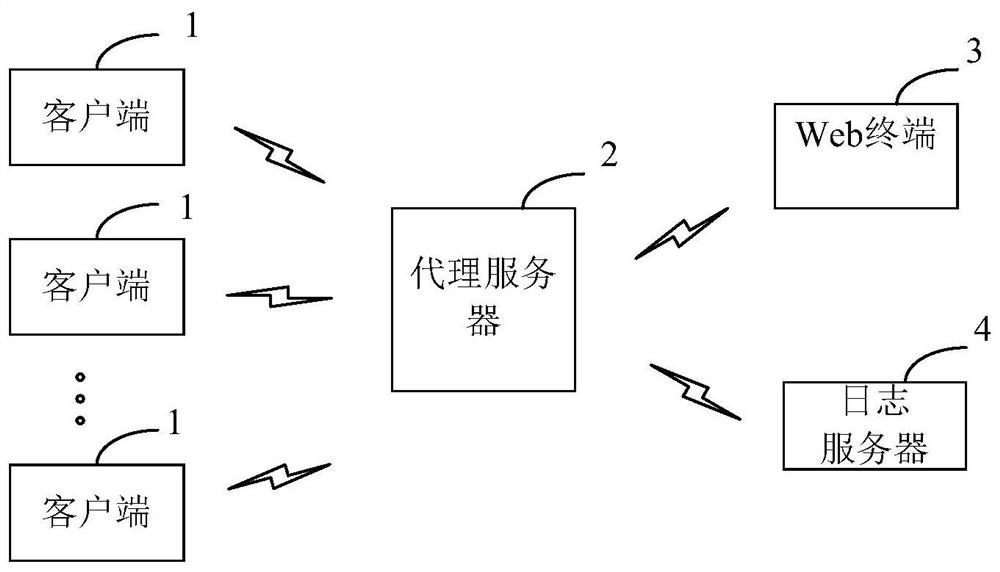
[0036] Specifically, the address of the web terminal is mapped to the proxy server, and the proxy server pretends to be a real web server, and exposes the IP address and port number for the client's request message to access the web terminal. It should be noted that the request message generally includes multiple online services.
[0037] S102. The proxy server judges the legitimacy of the flow of the request message;
[0038] Specifically, relevant personnel can judge the legality of traffic based on setting some specific rules. Certainly, the m...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com