A method for encrypting and securely transmitting data
A technology of encryption security and transmission method, which is applied in transmission systems, relational databases, database models, etc., can solve the problems of high security requirements for engineering data transmission, poor data pertinence, data encryption protection, etc., and achieve strong pertinence in data processing , Improving the efficiency of transmission and the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The concrete implementation of the present invention is described in detail below, it is necessary to point out here that the following implementation is only used for further description of the present invention, and can not be interpreted as limiting the protection scope of the present invention. Some non-essential improvements and adjustments still belong to the protection scope of the present invention.
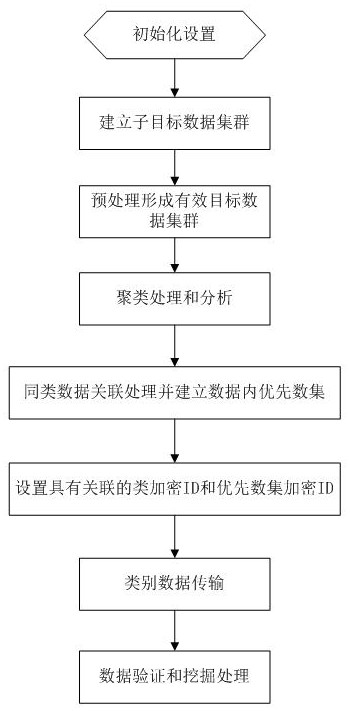
[0042] The present invention provides an encrypted secure transmission method for engineering data, and its specific flow is as attached figure 1 As shown, the processing efficiency and speed of data prediction can be improved through this method, and the data security is high, which will be introduced in detail below.
[0043] Data mining is a technology that finds its laws from a large amount of data by analyzing each data. It mainly includes three steps: data preparation, law finding and law expression. Data preparation is to select the required data from relev...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com