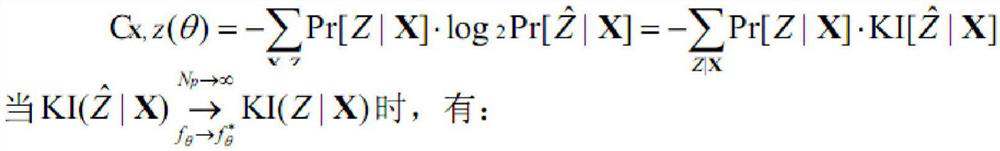Safety assessment framework building method for deep learning bypass analysis
A technology of security assessment and deep learning, which is applied in the field of security assessment framework construction of deep learning bypass analysis, which can solve problems such as cumbersome feature process, interference of feature extraction ability, inability to accurately extract data features, etc., and achieve low order of magnitude requirements and accurate measurement Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
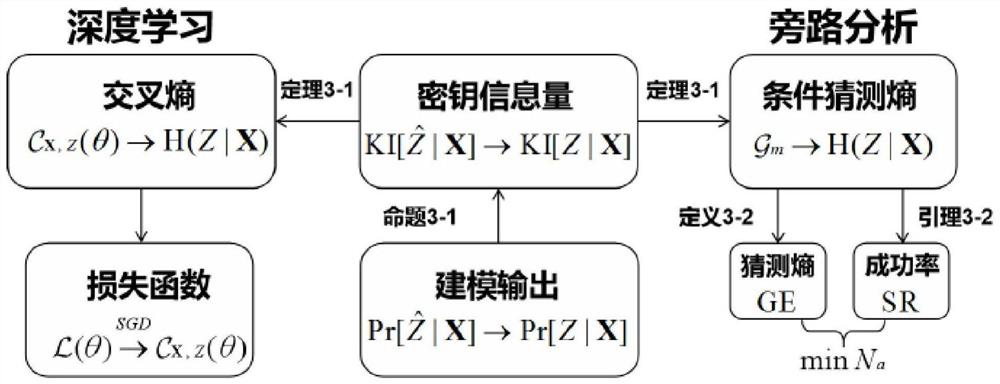
[0025] Embodiment 1, key information amount and bypass security assessment
[0026] (1) Key information volume and bypass security assessment
[0027] Although DLSCA is a combination of deep learning and bypass analysis, it is still a bypass analysis problem. To solve the DLSCA evaluation problem, it is necessary to start from the perspective of bypass security analysis. In the whole process of SCA, the probability distribution of each moment is only related to the probability distribution of the previous moment, so the process can be regarded as a Markov process:
[0028] Lemma 3-1 The SCA process can be defined as a Markov process: Among them, D is the bypass distinguisher, and K^ is the key value corresponding to the DNN model prediction category.
[0029] According to the SCA Markov process, combined with the DLSCA implementation steps, the DLSCA security assessment should address the following issues:
[0030] Question 3-1 (Evaluation Question) Given a training datase...
Embodiment 2
[0047] Embodiment 2, key information amount and DNN performance evaluation
[0048] (1) Information bottleneck theory explains DNN
[0049] DNN has always been considered as a black box model due to the complexity of the learning process. The previous section pointed out that machine learning performance metrics are not available, so it is necessary to find additional metrics to correlate key information. According to information bottleneck theory
[0050] In theory, the association between DNN layers and layers can be regarded as a Markov process, and the mutual information transferred in this process can measure the degree of learning:
[0051] Lemma 3-2 (Information Bottleneck Theory) In the hypothesis space H, the DNN model The structure can be interpreted as a Bayesian hierarchical structure. Because the input of the hidden layer i is the output T of the previous layer i-1 ,but Can be equivalent to a Markov chain: The corresponding probability distribution is: ...
Embodiment 3
[0058] Example 3, DLSCA evaluation index - PI (Z; T, θ)
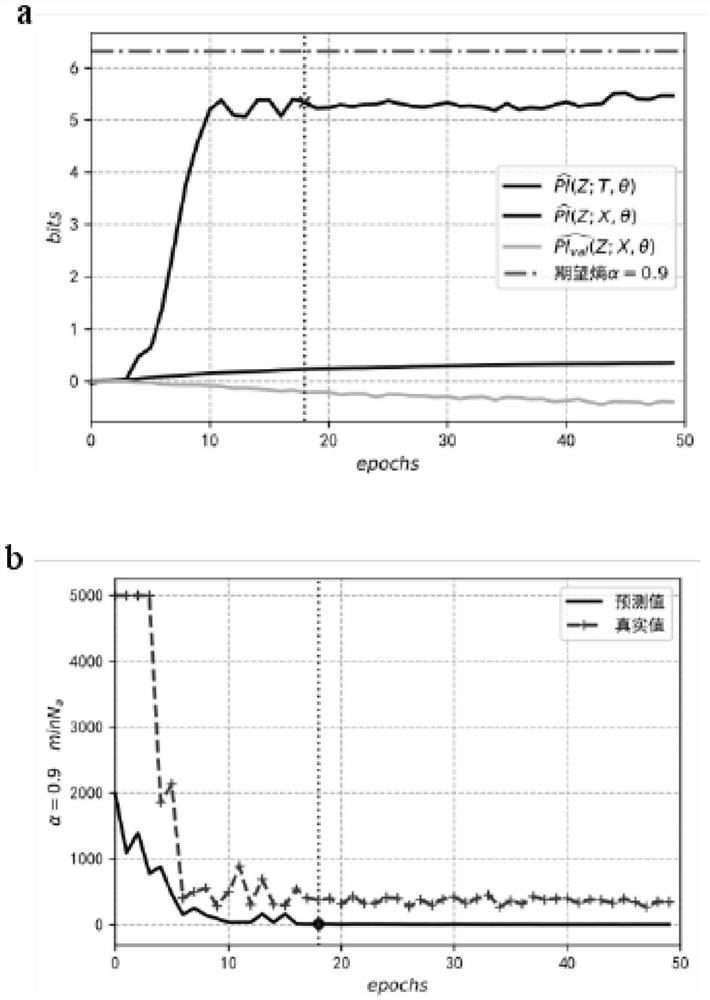
[0059] The essence of DNN training and learning is the optimization of the cross-entropy by the law of maximum likelihood. The more accurate the DNN model learning is, the cross-entropy CX, Z(θ) and the conditional guess entropy Gm tend to a fixed value H[Z|X] (Theorem 3 -1). Therefore, finding an evaluation index to establish a quantitative relationship with the cross entropy CX,Z(θ) can realize the DLSCA security evaluation framework with the key information as the core.
[0060] (1) Masure evaluation principle
[0061] Using the relationship between perceptual information and cross entropy function, DLSCA is evaluated by calculating the perceptual information of the X→Z process, but the error of this method is too large to accurately quantify and evaluate DLSCA. First introduce its evaluation principle:
[0062] ① Due to the random dimensionality reduction mechanism of the SGD algorithm, the actual sample size NSG...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com