Identity authentication method, storage medium and device integrating user's multi-source voice characteristics
An identity authentication and user technology, applied in the field of radio frequency identification and voice authentication, can solve the problems of fingerprint authentication infection risk, voice command replay attack, affecting authentication accuracy, etc., achieve strong practicability and feasibility, resist illegal access, Highly Confidential Effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
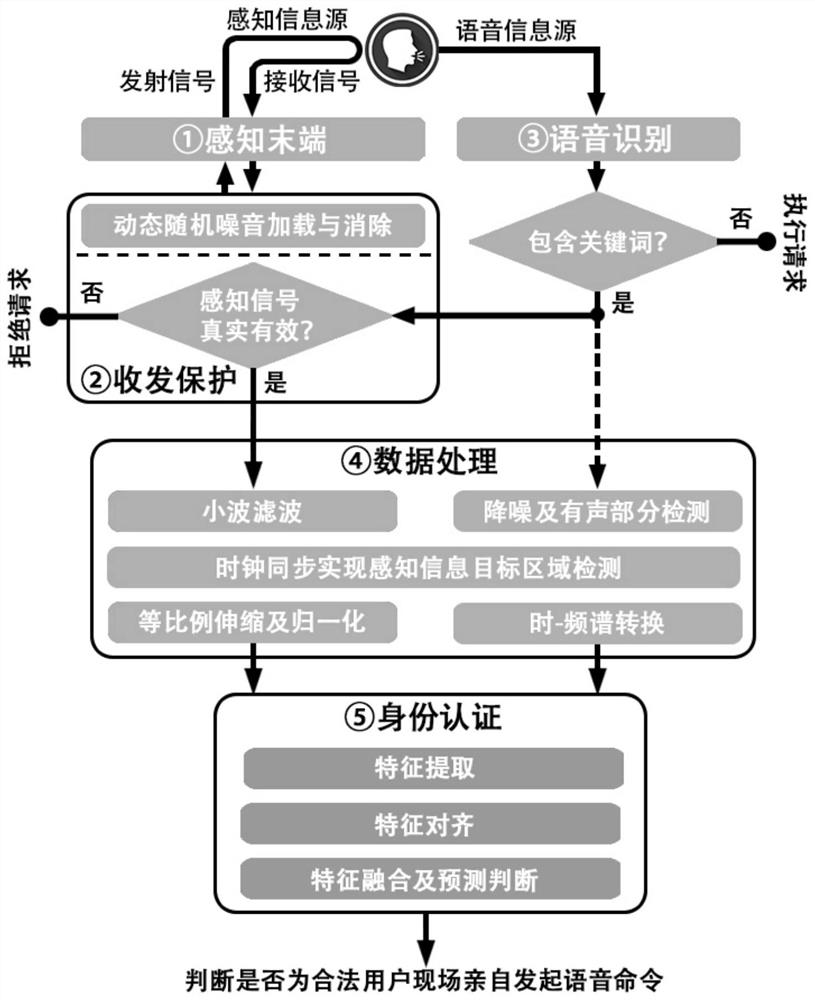
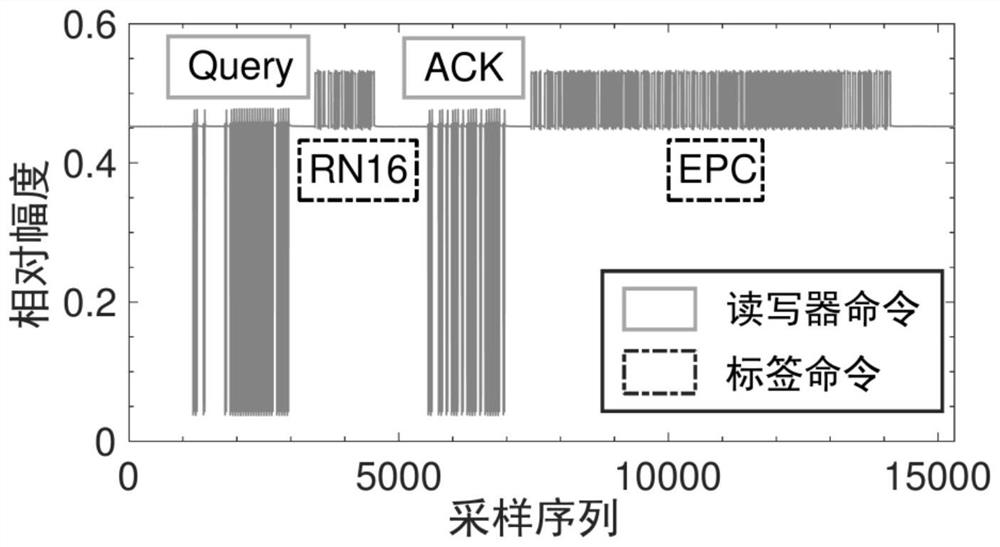
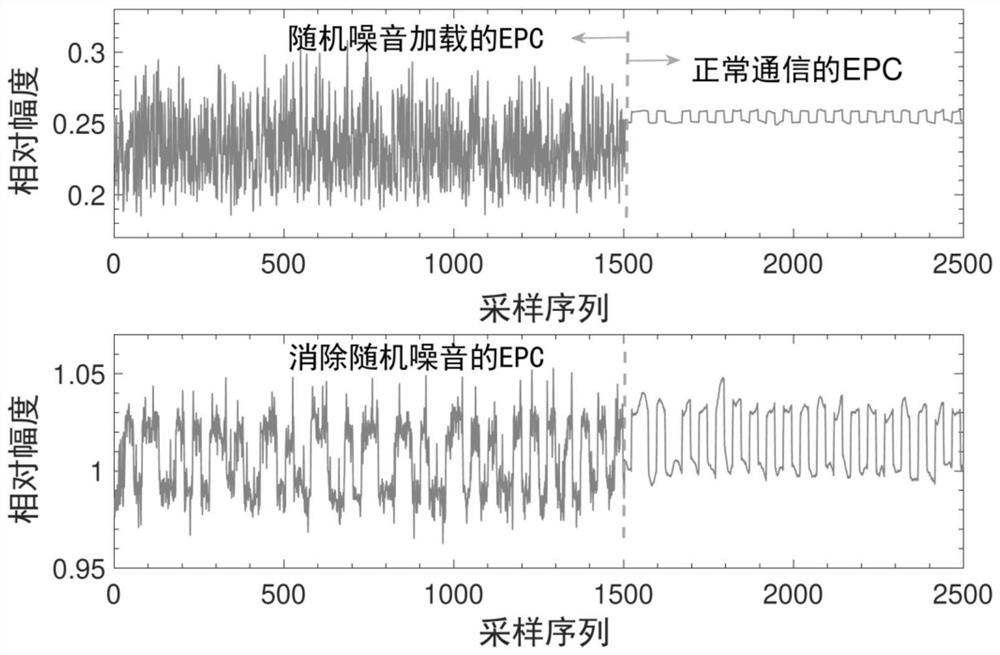
[0041] The present invention provides an identity authentication method, storage medium and equipment that integrates the user's multi-source vocalization characteristics, comprehensively considers the advantages and disadvantages and characteristics of common authentication technologies, and utilizes radio frequency identification (RFID) signal physical layer information to sense the user's mouth when vocalizing Motion features (the first source, the source of perceptual information), use the microphone to receive the voice commands issued by the user (the second source, the source of voice information), and design a double-branch neural network to extract identity features from the multi-source information of the user's voice at the same time. Realize integrated authentication; by designing a dynamic random noise loading and recovery mechanism at the RF transceiver end, it eliminates the security risk that the RF sensing signal is replayed together with the voice signal by an ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com