Network security deduction method, device and equipment and storage medium
A technology for network security and network simulation, which is applied in the fields of equipment and storage media, network security deduction methods, and devices, and can solve the problems of inability to simulate the performance of new cyberspace equipment, inability to preview emergency response, and excessive influence of communication protocol rules.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0031] figure 1 It is a flow chart of a network security deduction method provided by Embodiment 1 of the present invention, and this embodiment is applicable to the situation of performing deduction on cyberspace security. The network security deduction method provided in this embodiment can be executed by the network security deduction device provided in the embodiment of the present invention, and the device can be realized by means of software and / or hardware, and integrated into the computer equipment executing the method.
[0032] see figure 1 , the method of this embodiment includes but not limited to the following steps:
[0033] S101. Determine a network to be simulated according to an information system and a data interaction service.
[0034] Wherein, the network to be simulated may be a network that matches the network environment of the real business system that needs to be simulated.
[0035] In the Internet era, especially in the smart city information system...
Embodiment 2
[0048] figure 2 It is a flowchart of a network security deduction method provided by Embodiment 2 of the present invention. The embodiments of the present invention are optimized on the basis of the foregoing embodiments. Optionally, this embodiment explains in detail the process after accessing the hardware-in-the-loop simulation system.
[0049] see figure 2 , the method of this embodiment includes but not limited to the following steps:
[0050] S201. Determine a network to be simulated according to an information system and a data interaction service.
[0051] S202, linking the network elements based on the network to be simulated, and accessing the hardware-in-the-loop simulation system.
[0052] Optionally, the accessing the hardware-in-the-loop simulation system may specifically include: simulating the physical properties of at least one network element by accessing a virtual machine; accessing at least one physical device, and the at least one physical device is ...
Embodiment 3
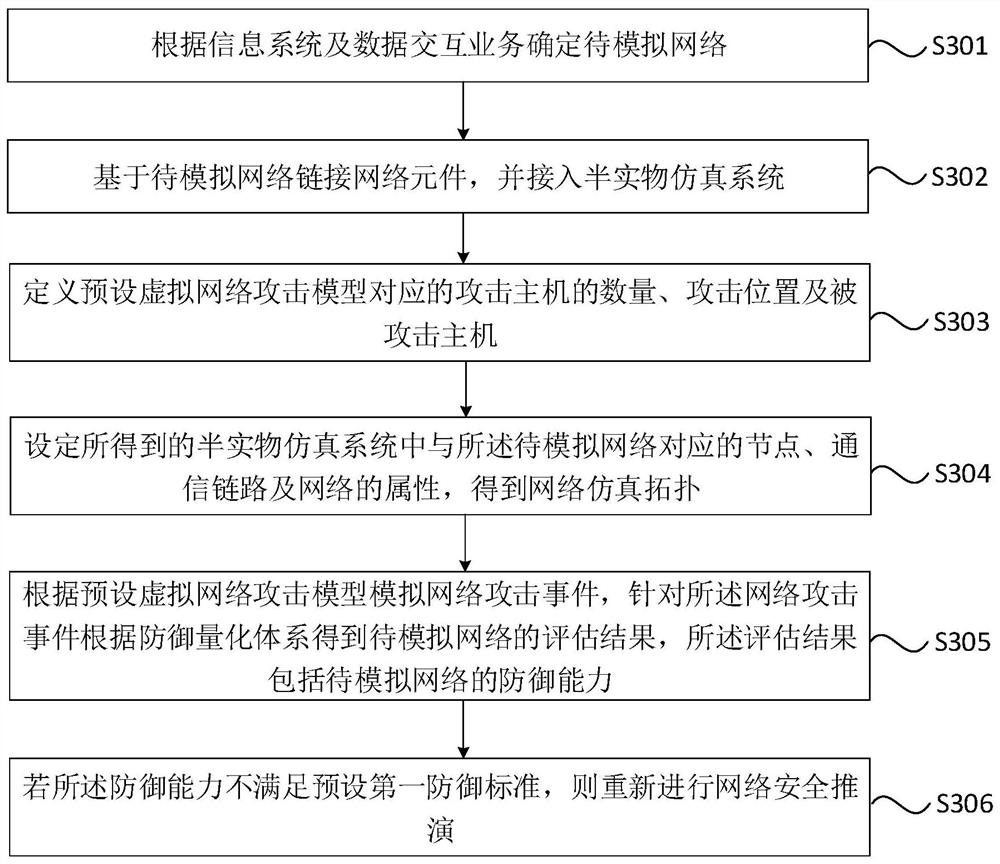
[0063] Figure 3A It is a flow chart of a network security deduction method provided by Embodiment 3 of the present invention. The embodiments of the present invention are optimized on the basis of the foregoing embodiments. Optionally, this embodiment explains in detail the process of simulating network attack events according to a preset virtual network attack model, performing network security deduction, and obtaining evaluation results.
[0064] refer to Figure 3A , the method of this embodiment includes but not limited to the following steps:
[0065] S301. Determine the network to be simulated according to the information system and the data interaction service.
[0066] S302, linking the network elements based on the network to be simulated, and accessing the hardware-in-the-loop simulation system.
[0067] S303. Define the number of attacking hosts, attacking locations, and attacked hosts corresponding to the preset virtual network attack model.
[0068] S304, se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com