Intelligent equipment network communication security implementation method based on Internet of Things
A smart device and network communication technology, applied in the field of network communication, can solve problems such as network communication links being tapped, communication links being tapped, keys easily leaked, etc., to achieve resistance to repeated data attacks, less MCU resources, and solve security problems. problem effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
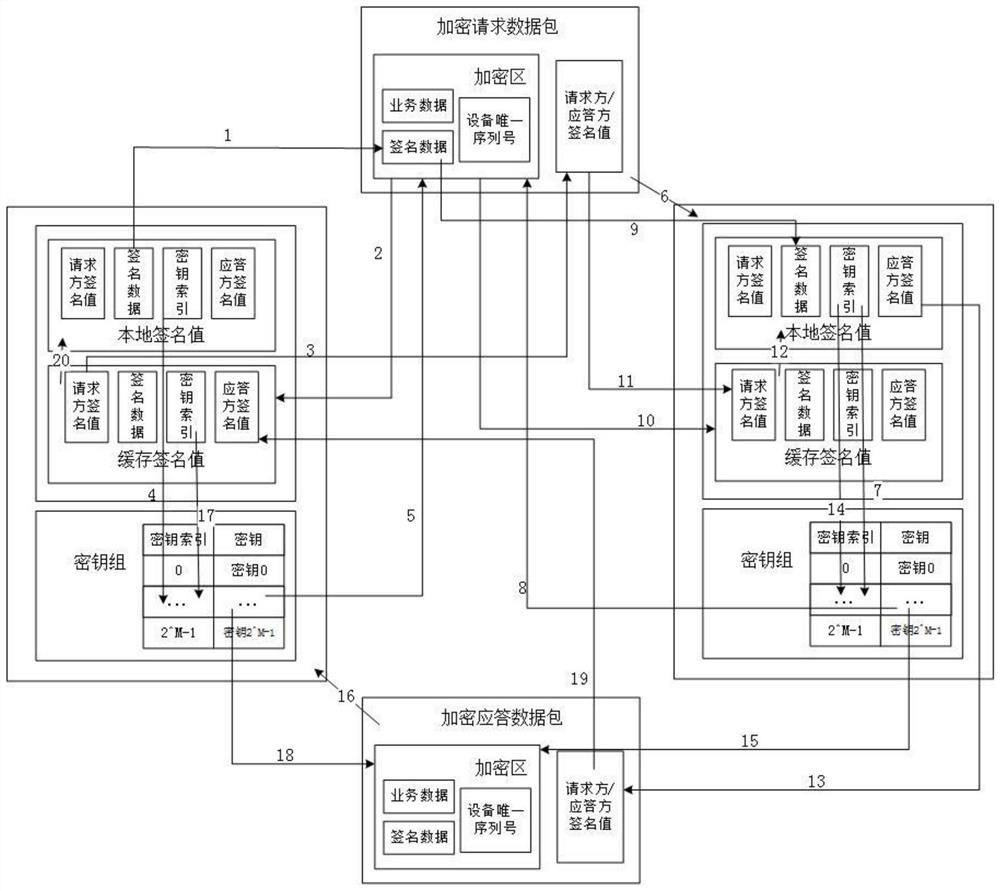
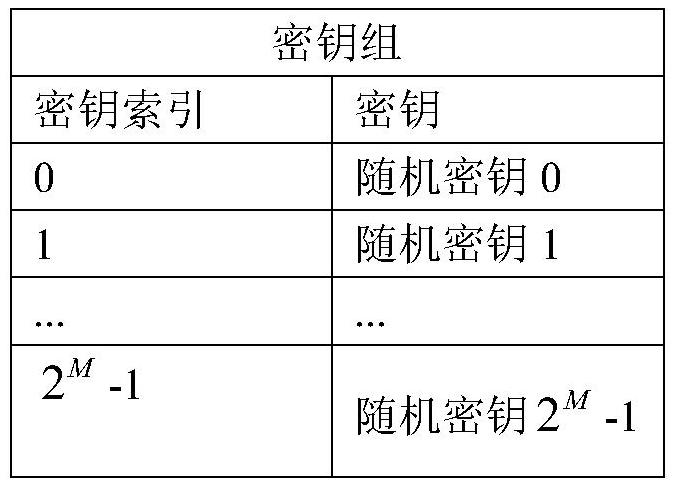
[0043] Embodiment 1: A method for realizing network communication security of smart devices based on the Internet of Things, such as figure 1 As shown, first set the key group, each key group is 2 M keys and 2 M key index, and the key group structure is shown in Table 2-1:
[0044] Table 2-1 Key group structure
[0045]
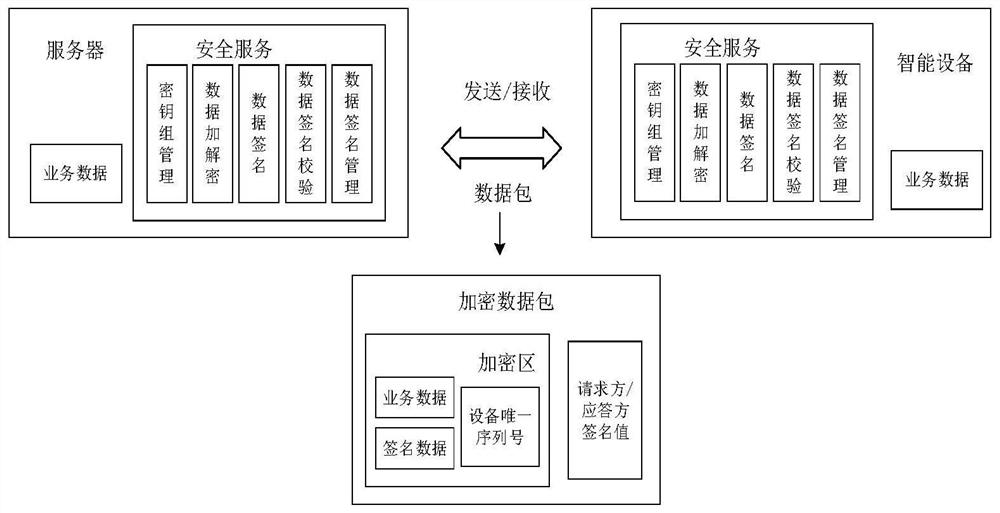
[0046] Encapsulate and encrypt the communication data. The structure of the encapsulated data packet is shown in Table 2-2:
[0047] Table 2-2 Data packet structure
[0048]
[0049] The data packet is divided into an encryption area and a verification area; all data in the encryption area is encrypted, including business data, unique serial number of the device, and signature data. The signature value of the requester or responder is stored in the verification area, which is used for identity verification and data tampering inspection.
[0050] The encryption process adopts the method of electronic signature. Through MD5 Message-Digest Algorithm, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com