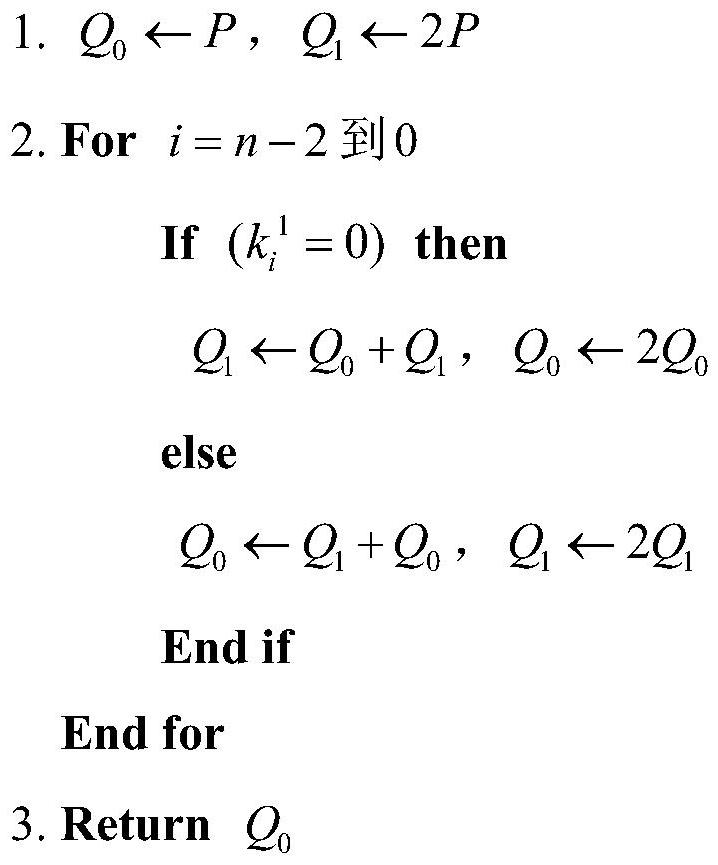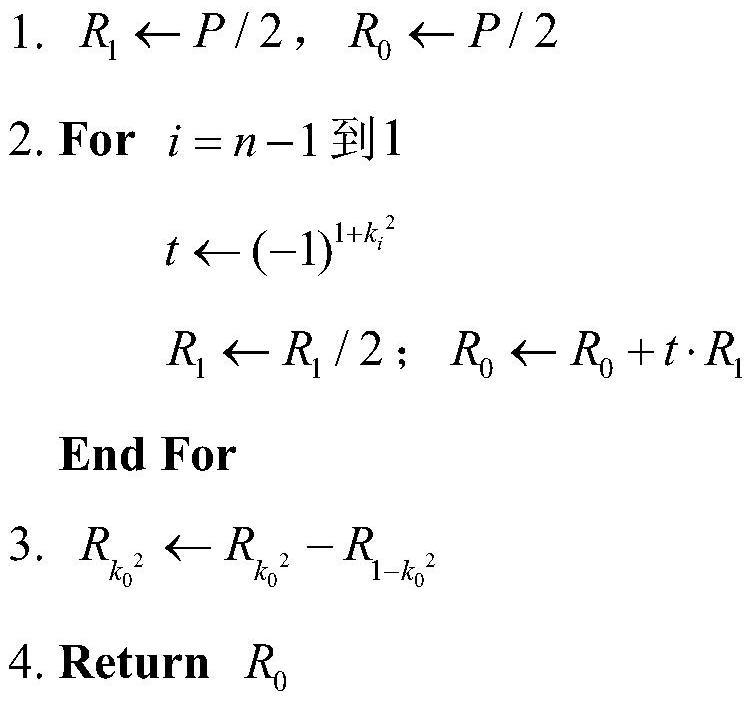Parallel processing method and device for scalar multiplication on elliptic curve with characteristic of 2
An elliptic curve, parallel processing technology, applied in the field of information security, can solve the problem that the half-point algorithm cannot use projective coordinates and so on
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
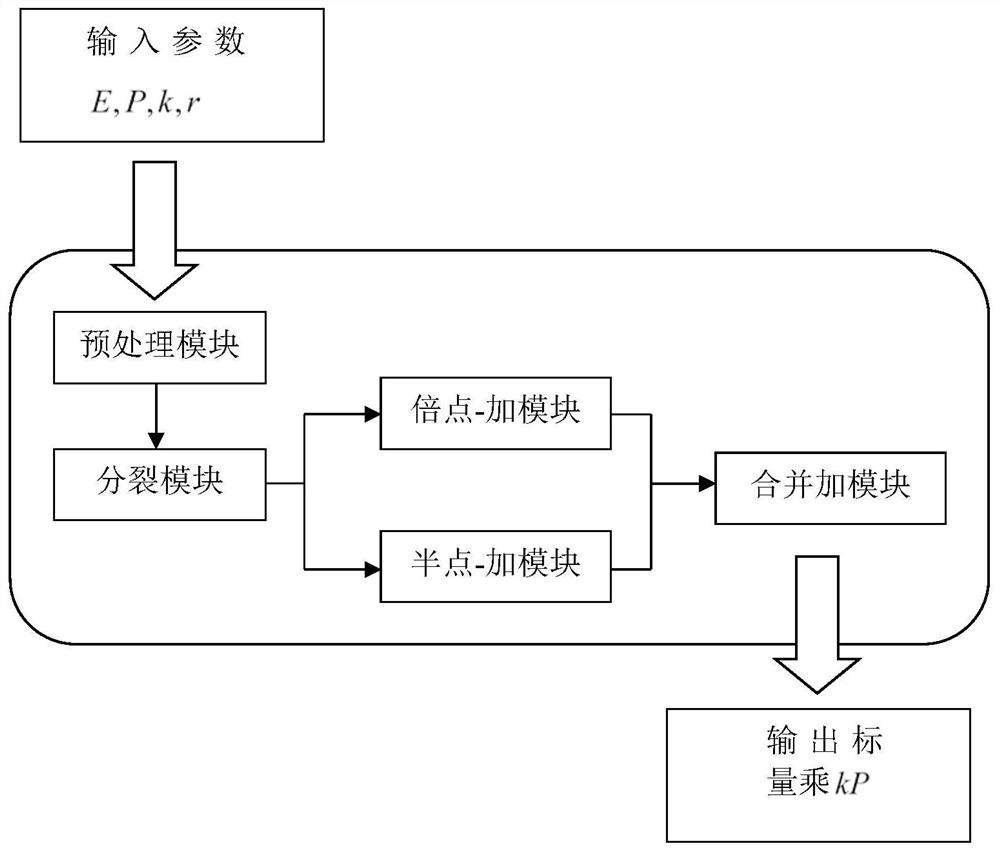
Image
Examples
Embodiment Construction
[0059] 1. The underlying computing program and system basic parameters
[0060] Before implementing the scalar multiplication operation, it is necessary to implement addition, multiplication, squaring, inversion, square root, root operation of the quadratic equation, etc. on the characteristic 2 finite field according to the parameters of the elliptic curve. When realizing the above operation, the properties of the finite field of characteristic 2 and the modulo operation are needed. The multiplication, squaring, square root, finding the root of a quadratic equation and the inverse operation described in this patent are respectively modular multiplication, modular square, modular square root, and the root of a modular quadratic equation and the modular inverse operation. This requires the choice of irreducible polynomials in finite fields to be good enough to improve computational efficiency.
[0061] In standard FIPS 186-4, NIST recommends 10 elliptic curves over finite fiel...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com