Cloud-based active immune security defense method and device
A technology of security defense and active immunity, applied in the field of information security, it can solve the problems of inability to deal with zero-day vulnerabilities, unknown internal attacks, and inability to deal with attack threats.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0030] In the cloud-based active immune security defense method and device disclosed in an embodiment of the present invention, the steps are:
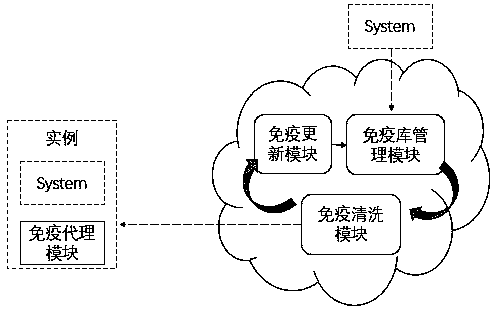
[0031] 1) The immune library management module establishes a mirror virtual machine system in the cloud that is completely consistent with the initial state of the instance system outside the cloud;
[0032] 2) The immune cleaning module replaces the mirror system in the cloud to the instance system outside the cloud, keeps the operation and maintenance instance system completely consistent with the mirror system in the cloud, and identifies inconsistent heterogeneous software;
[0033] 3) The immune update module performs a security upgrade on the mirror system in the cloud;
[0034] 4) The immune agent module runs in the hardware remote boot state in the off-cloud instance system, receives the cleaning comma...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com