Access control method, device and system, computer equipment and storage medium
An access control, computer program technology, applied in transmission systems, electrical components, etc., can solve problems such as being vulnerable to piggyback attacks, difficult to accurately set the service exposure time window, affecting normal access, etc., so as to reduce the time of scanning and detection. , the effect of reducing ineffective time and reducing risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
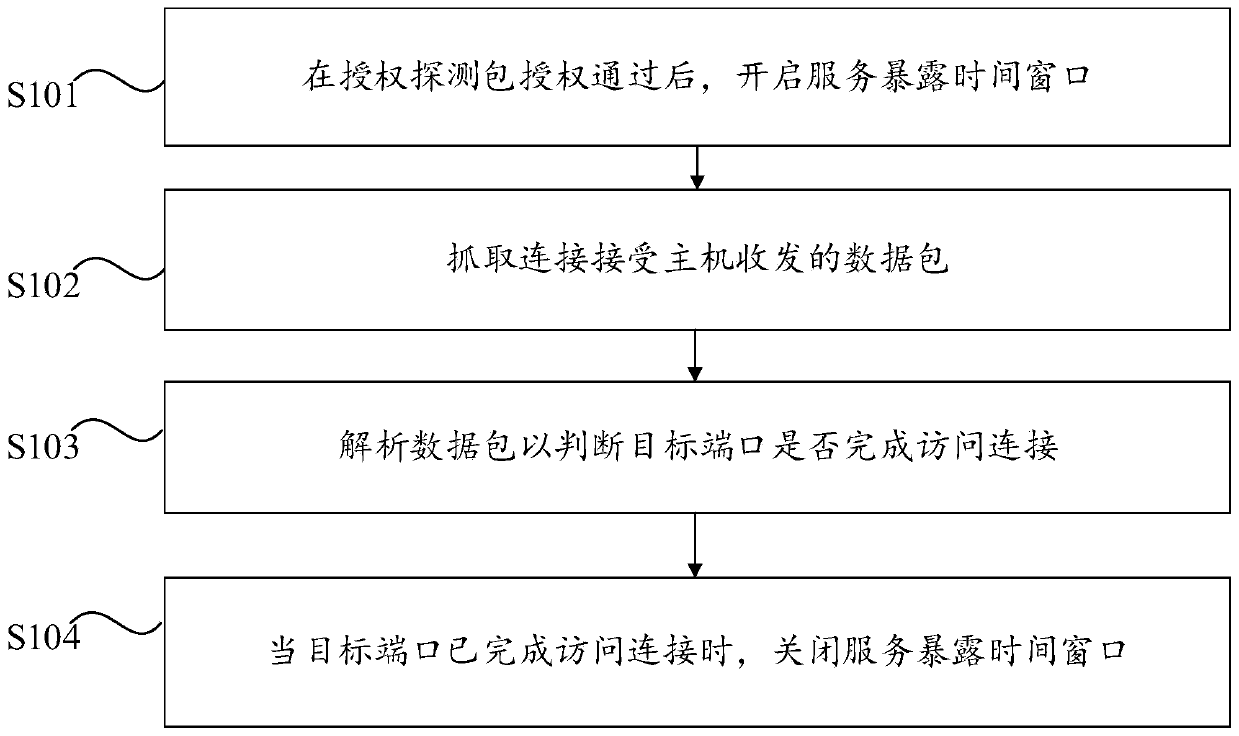
[0035] The embodiment of the present invention provides an access control method. The execution subject of the access control method is the connection accepting host. Through the interaction with the connection opening host and the controller, the normal connection from the connection opening host to the connection accepting host can be achieved without affecting the connection opening host. On the premise of access, close the service exposure time window in time to reduce the invalid time when the service exposure time window is opened, thereby reducing the time for attackers to scan and detect, and reducing the risk of piggyback attacks. specifically, figure 1 A flow chart of the access control method provided by Embodiment 1 of the present invention, such as figure 1 As shown, the access control method provided in this embodiment includes the following steps S101 to S104.
[0036] Step S101: After the authorization detection packet is authorized, open the service exposure ...
Embodiment 2
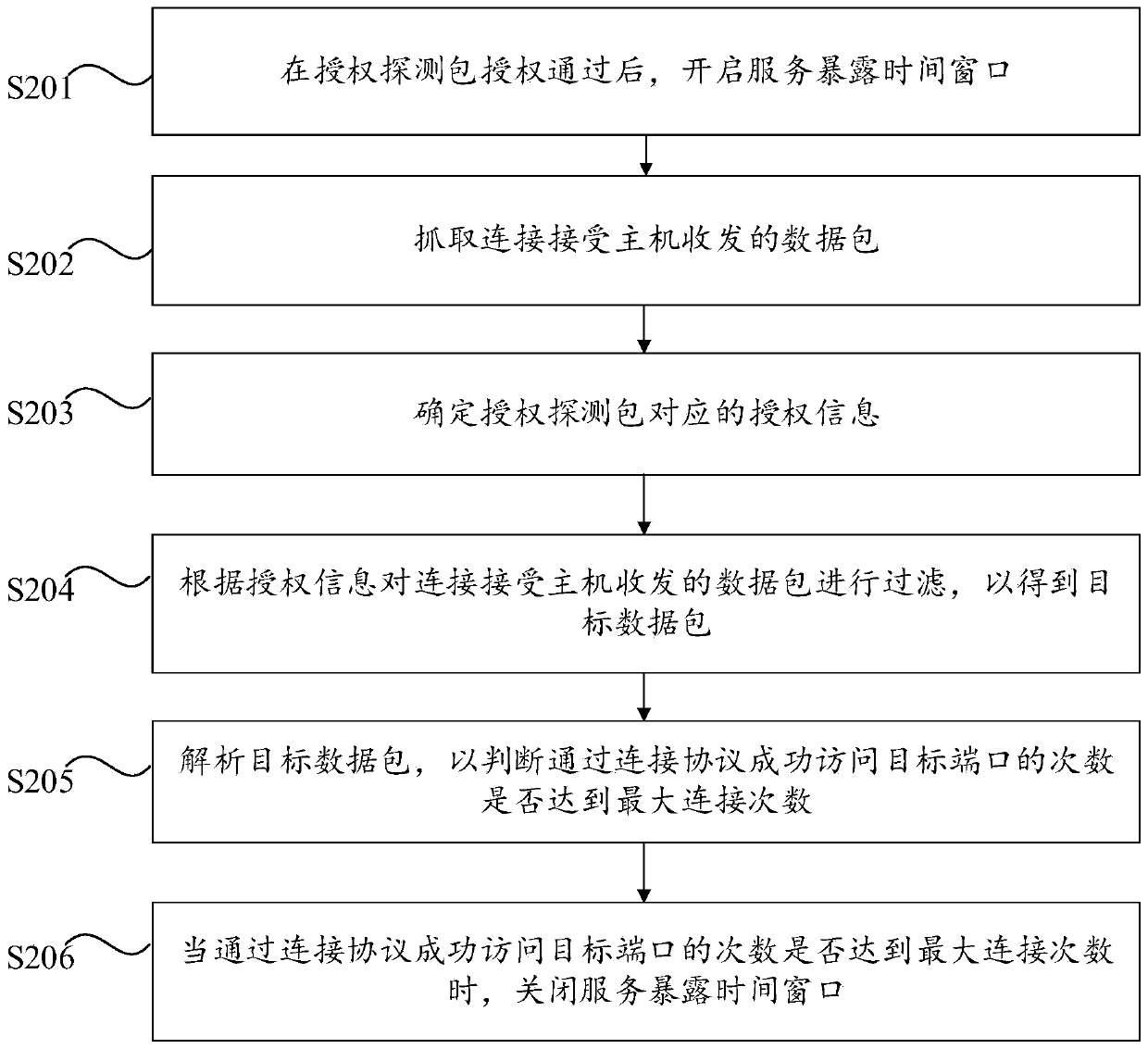
[0054] Embodiment 2 of the present invention provides a preferred access control method to control the access of the hidden service from the connection-opening host to the connection-accepting host. Some technical features are the same as those of the first embodiment above. The specific description and corresponding technologies The effect can refer to the first embodiment above. Furthermore, in the second embodiment, by tracking the number of connections between the connection opening host and the connection accepting host, it is judged whether the target port has completed the access connection based on whether the number of connections reaches the maximum number of connections, and then the service exposure can be closed at an appropriate time. Time window to improve the accuracy of access control. specifically, figure 2 The flow chart of the access control method provided by Embodiment 2 of the present invention, such as figure 2 As shown, the access control method pr...
Embodiment 3
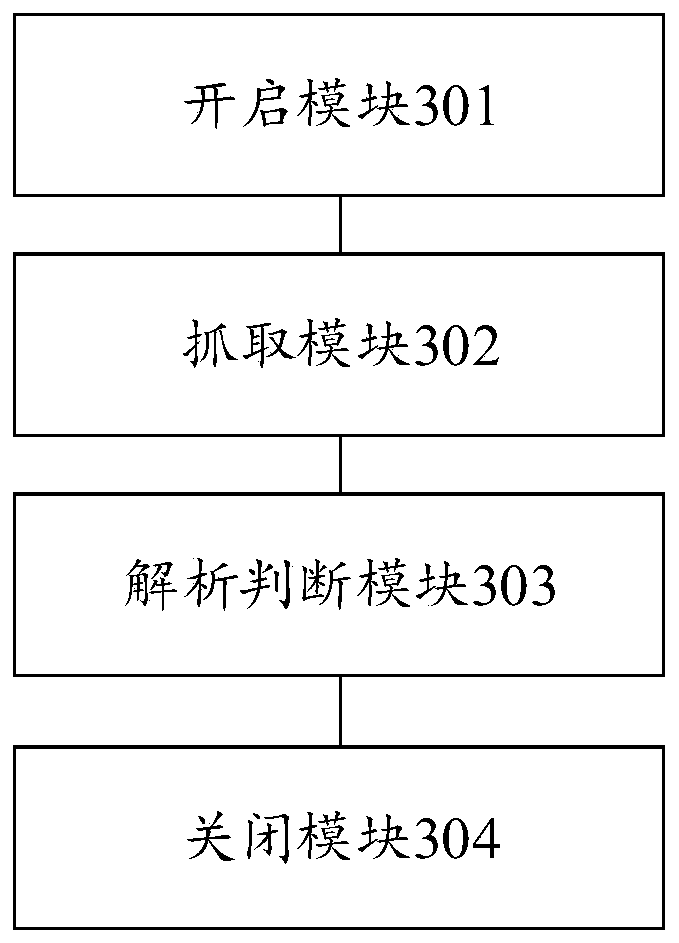
[0070] Corresponding to the first embodiment above, the third embodiment of the present invention provides an access control device, the access control device is set on the connection accepting host, the corresponding technical features and technical effects can be referred to above, and will not be repeated here. image 3 The block diagram of the access control device provided for Embodiment 3 of the present invention, such as image 3 As shown, the device includes an opening module 301 , a grabbing module 302 , an analysis and judgment module 303 and a closing module 304 .
[0071] Wherein, the opening module 301 is used to open the service exposure time window after the authorization detection packet is authorized, wherein, when the service exposure time window is opened, the connection opening host sending the authorization detection packet can access the target port of the connection accepting host; Grabbing module 302 is used for grabbing the data packet sent and receive...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com