Safety access method and system based on fire wall policy
A firewall policy and security access technology, applied in the security access method and system field based on firewall policy, can solve problems such as reducing the effect of firewall restrictions, confusion of firewall policies, and affecting the operation of existing network services, so as to avoid configuration problems and dangers , reduce human operations, and protect against cyber threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
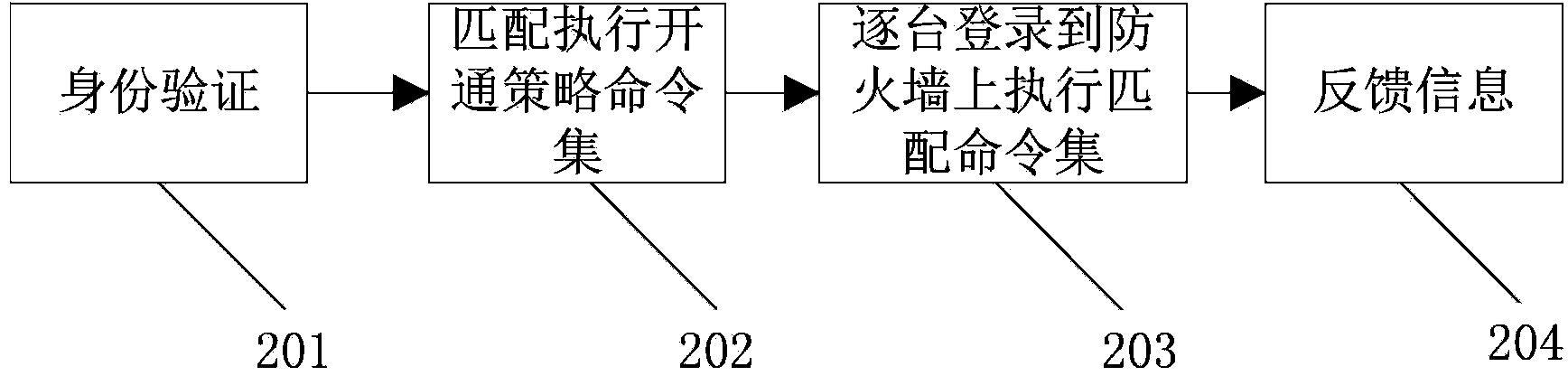
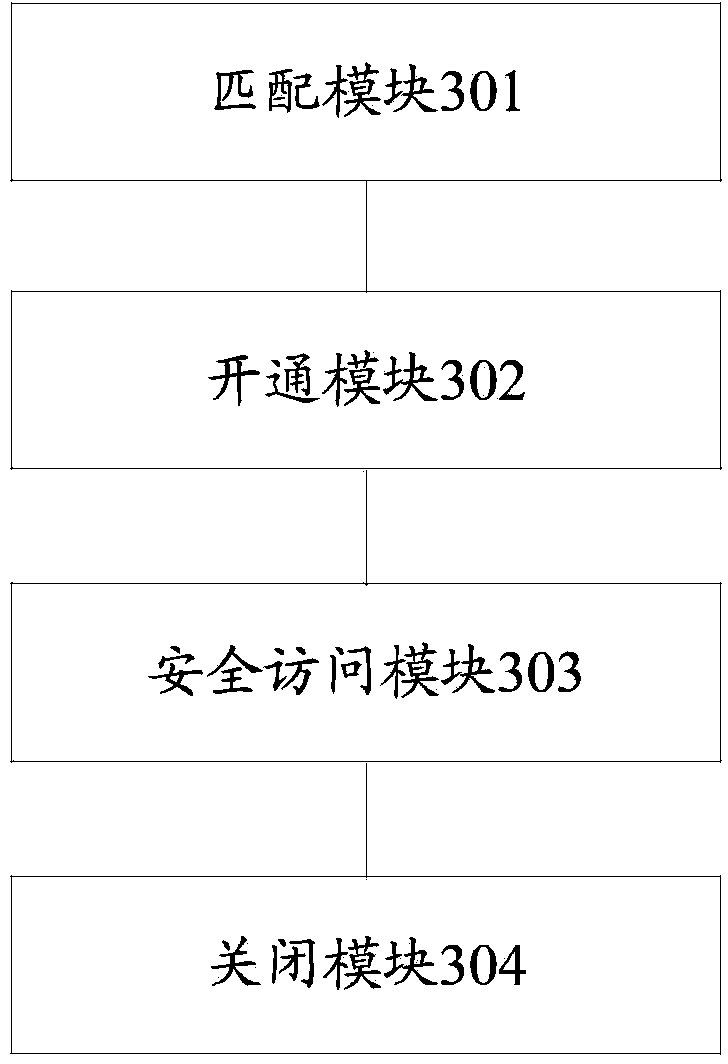
[0046] In order to make the object, technical solution and advantages of the present invention clearer, the implementation manner of the present invention will be further described in detail below in conjunction with the accompanying drawings.
[0047] The embodiments of the present invention aim at the method and the system generated when the target device cannot meet the effective access requirement. When there is a new access requirement, the configuration template of the firewall policy will be used to match the network addresses of all device firewalls. After the match is successful, the device can be accessed and operated, while the firewalls of other devices are still in the service configuration outside the security policy. state (closed state), when the target device is accessed, the firewall of other devices is in a denial of service state so that it will not be affected in any way and prevent the invasion of other threats. After the required access is completed, the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com