Memory, verification code implementation method, device and equipment
An implementation method and verification code technology, which is applied in the direction of digital data authentication, can solve the problems of user identity authentication security risks and high probability of cracking, and achieve the effect of reducing the probability of passing verification and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
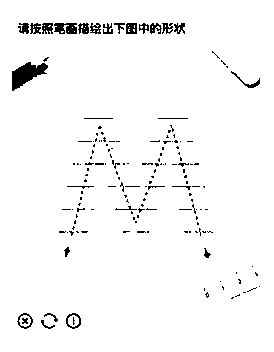
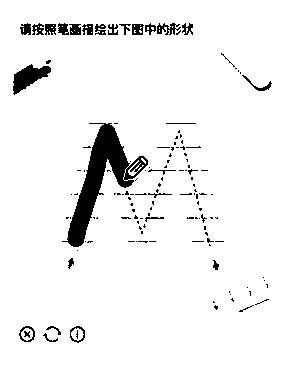
[0054] figure 1A flowchart showing a method for implementing a verification code provided by an embodiment of the present invention, the method may be executed by an electronic device, such as a network device, a terminal device, or a server device. In other words, the method can be implemented by software or hardware installed on network equipment, terminal equipment or server equipment. The server includes, but is not limited to: a single server, a server cluster, and the like. refer to Figure 1 to Figure 4 , the method includes the following steps.
[0055] S11. Obtain a verification picture including a preset graphic;
[0056] The inventor found through research that in the prior art, in the verification method of dragging the slider to the target position, the number of trajectory answers is very limited; specifically, from the starting point of the slider to the farthest position, from the shape of the motion trajectory Said to be a straight line, the pixel length o...
Embodiment 2
[0076] Figure 5 It shows a schematic structural diagram of the device for realizing the verification code provided by the embodiment of the present invention, and the device for realizing the verification code is a device corresponding to the method for realizing the verification code described in Embodiment 1, that is, the method in Embodiment 1 is realized by means of a virtual device. The verification code realization method and each virtual module constituting the verification code realization apparatus can be executed by electronic equipment, such as network equipment, terminal equipment, or server.
[0077] Specifically, the verification code implementation device in the embodiment of the present invention includes:
[0078] The verification picture acquisition unit 01 is used to obtain a verification picture including a preset graphic; the prompt unit 02 is used to prompt the user to draw in the verification picture according to the trajectory of the preset graphic; th...
Embodiment 3
[0086] An embodiment of the present invention provides a memory, and the memory may be a non-transitory (non-volatile) computer storage medium, and the computer storage medium stores computer-executable instructions, and the computer-executable instructions can execute any of the above methods to implement Each step of the verification code implementation method in the example, and achieve the same technical effect.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com