A method for collecting sensitive data
A technology of sensitive data and data sets, applied in the field of information security, can solve the problems of leaking users' personal privacy data, noise without considering attributes, untrusted servers, etc., to meet data availability, improve security, and protect privacy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
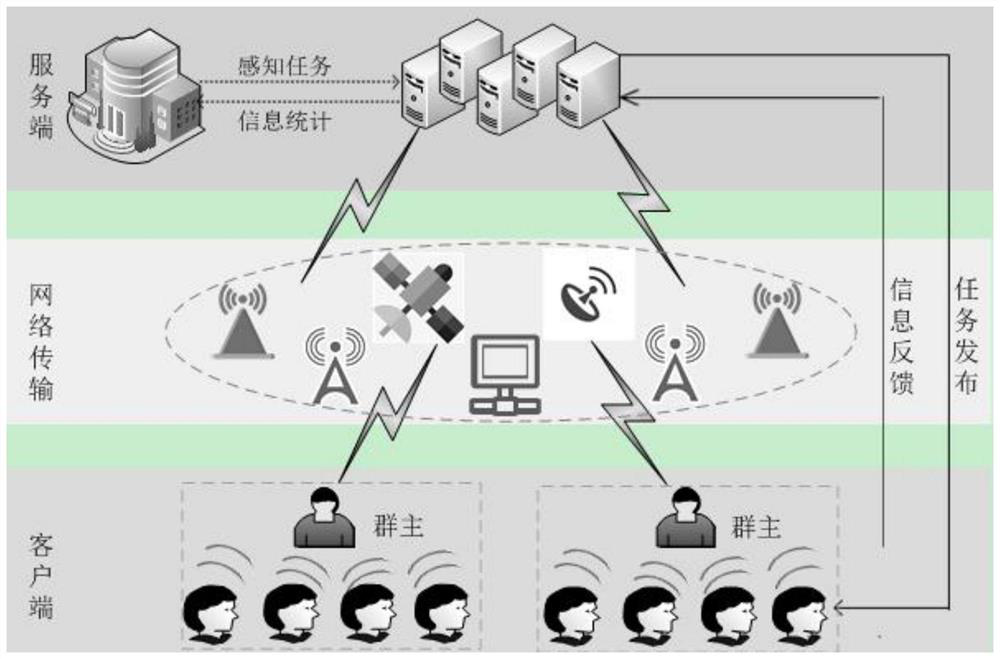
[0020] Please refer to figure 1 , a method for collecting sensitive data, comprising the steps of:
[0021] S0, the server generates a corresponding pseudonym ID for the i-th client i ', where i ranges from 1 to m, and m represents the total number of clients.
[0022] S1. The server judges whether the instruction information sent by the client is a creation instruction, and if so, creates a disturbance group G j , and select the client as the owner client of the disturbance group, otherwise, select the client as a member client, and assign the member client to the corresponding disturbance group, and the The above creation instructions include the public key PK of the group owner client j , where j represents the sequence number of the disturbance group;
[0023] The specific assignment of the member clients to the corresponding disturbance group is as follows:
[0024] The member clients are assigned to corresponding perturbation groups under pseudonyms.
[0025] The i...
Embodiment 2
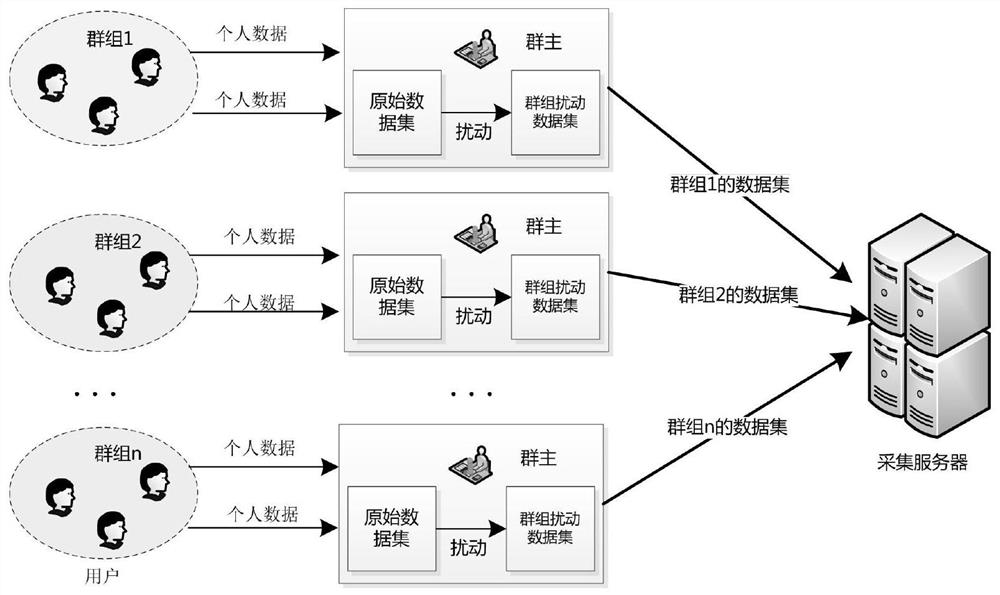
[0047] Please refer to figure 2 with 3 The difference between this embodiment and Embodiment 1 is that the present invention will further illustrate how the above-mentioned sensitive data collection method of the present invention is realized in combination with specific application scenarios:
[0048] S0, the server generates a corresponding pseudonym ID for the i-th client i ', where i ranges from 1 to m, and m represents the total number of clients.
[0049]S1. The server judges whether the instruction information sent by the client is a creation instruction, and if so, creates a disturbance group G j , and select the client as the owner client of the disturbance group, otherwise, select the client as a member client, and assign the member client to the corresponding disturbance group, and the The above creation instructions include the public key PK of the group owner client j , where j represents the sequence number of the disturbance group;
[0050] The specific as...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com