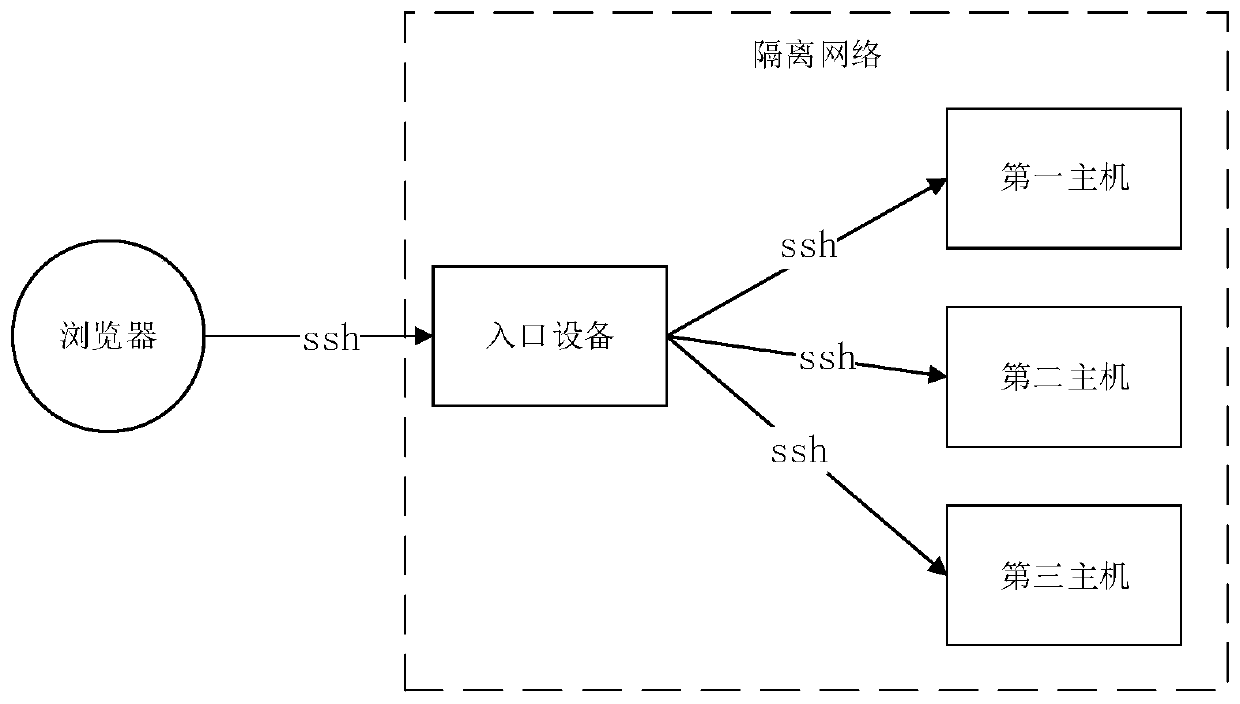
Command processing method and device for host, electronic equipment and storage medium
A command processing and host technology, which is applied in the field of network isolation and computer network, can solve the problems of easy leakage of internal data, etc., and achieve the effect of preventing data leakage, ensuring data security, and improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0059] Example 1. The preset condition includes: the received external command belongs to a predetermined type of shell command; the predetermined processing includes: determining not to process the external command.
[0060] In this example, for shell commands, whether to process them is determined according to their type. The processing of a shell command starts the shell command interpreter. For example, after the csh command is executed, csh will be started, so that subsequent external commands will be switched to csh for processing. In order to avoid this situation, the shell command type corresponding to the shell command interpreter that does not have a preset list configured can be pre-recorded as a predetermined type. The predetermined type of shell command will start the corresponding shell command interpreter, and then refuse to process the predetermined type of shell command, thereby preventing other command interpretation components from switching to process subs...
example 2
[0061] Example 2. The preset condition includes: the external command belongs to the compilation and construction command; the predetermined processing includes: determining not to process the external command.
[0062] The compilation and construction command may be, for example, a compilation and construction command in C language or C++ language such as gcc and make. Using the compile and build command, you can build a shell command interpreter. If the built shell command interpreter is not in the preset list, it can be executed. Since the shell command interpreter itself is also a shell command, executing the shell command can also switch the command interpretation component used in the host to the shell command interpreter built by compiling and building commands, causing subsequent external commands to switch to the built shell command interpreter. For example, if a shell command interpreter is built using the compile and build command and named "zsh1", since "zsh1" do...
example 3
[0064] Example 3, the preset condition includes: the script of the external command includes a release symbol, and the command interpretation component specified by the script of the external command is not the first type of command interpretation component; the predetermined processing includes: interpreting the command specified by the script of the external command The component switches to the first type of command interpretation component.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com