Credit granting authorization method for digital assets
A technology of digital assets and assets, applied in the field of information security, to achieve the effect of authentically verifying fraudulent behaviors and eliminating fraudulent behaviors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] The technical solution of the present invention will be further elaborated below in conjunction with the description of the drawings and specific embodiments.
[0031] Firstly, the relevant parties involved in the method of the present invention are defined.
[0032] The present invention defines the relevant parties of the method as follows:
[0033] 1. Related parties of digital assets
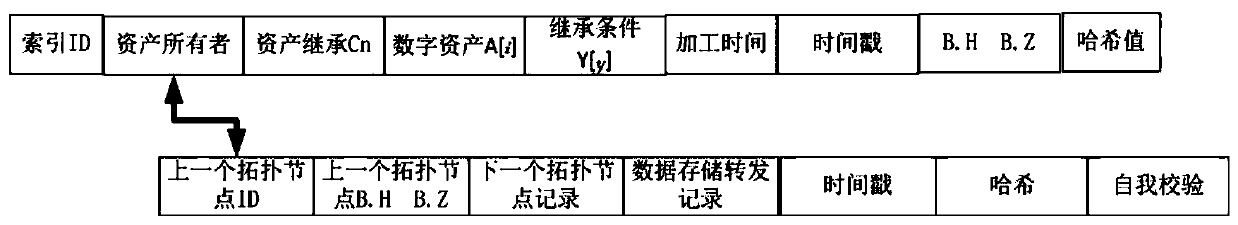
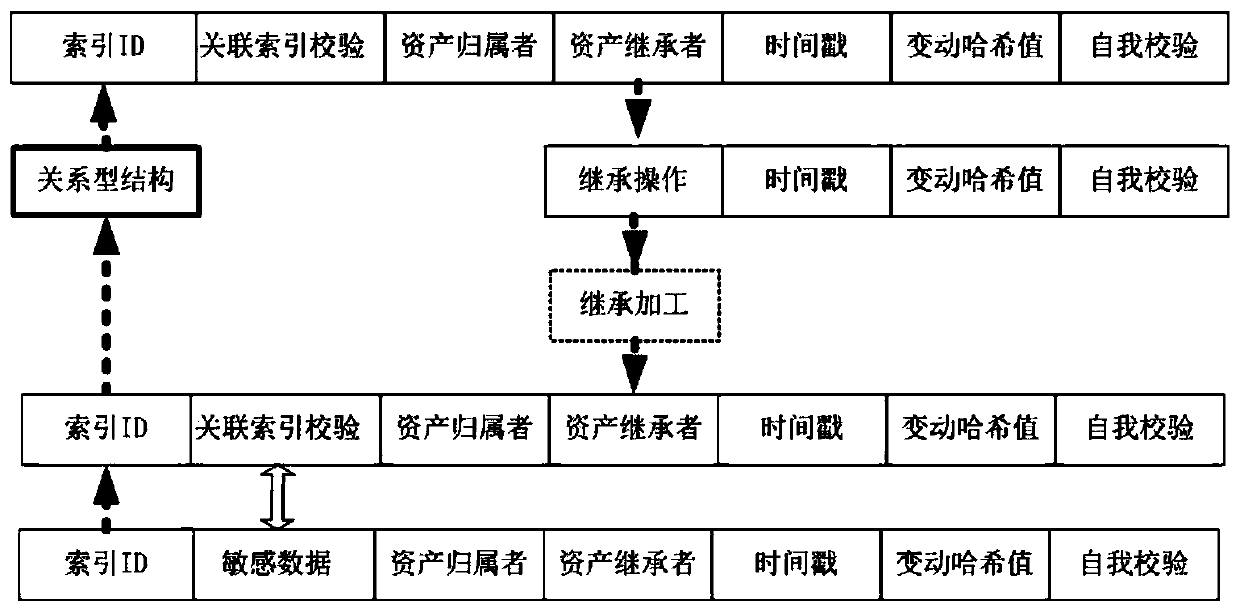
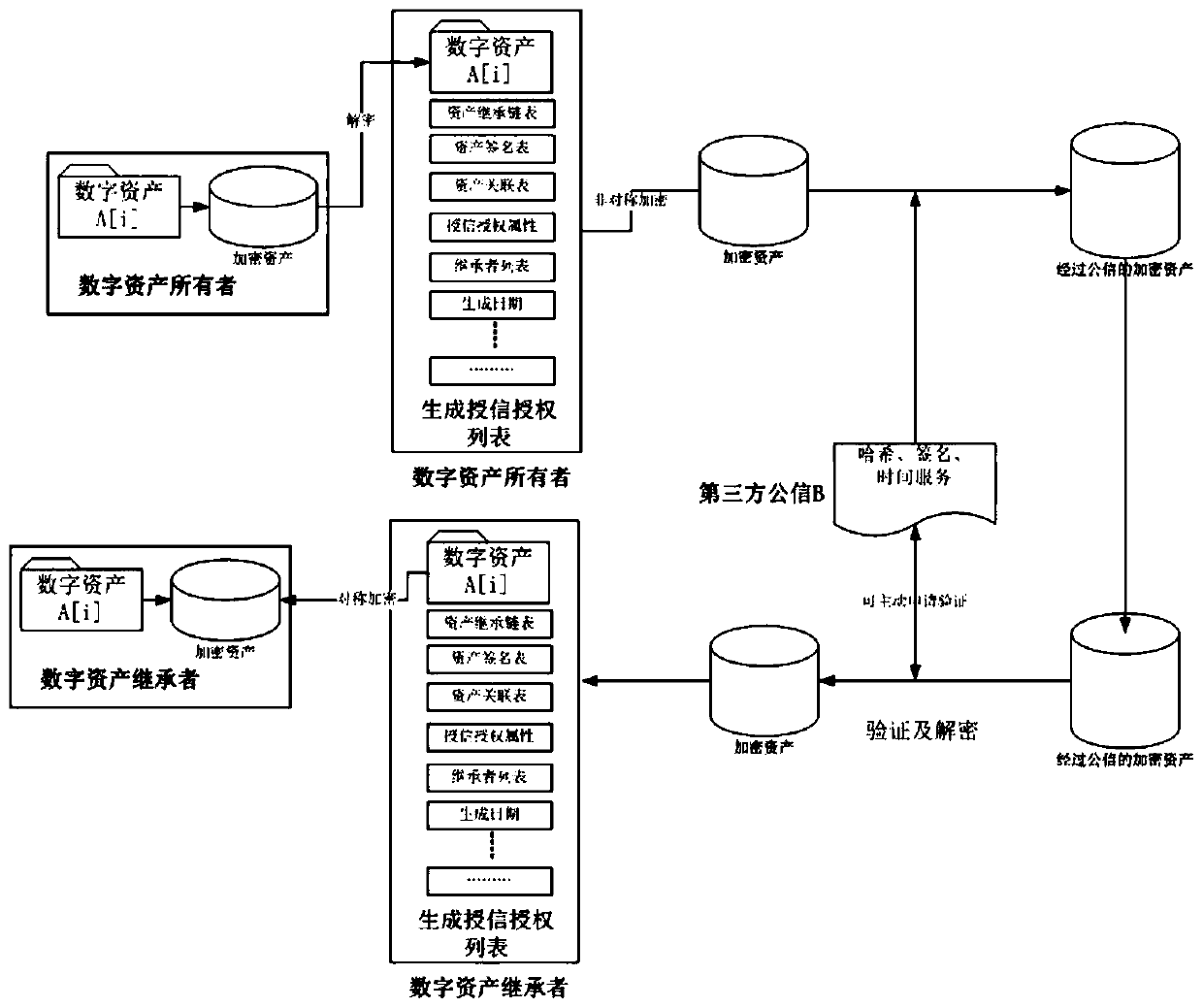
[0034] Let A represent the owner group (or collection) of digital assets with data correlation, which is identified by a sequence / matrix, and A[i] is the owner of the i-th inherited digital asset. Then in the present invention, A[i], i∈[1, 2, 3, .... P-1]) is the collection of all digital assets of the i-th owner, and i is incremental data, generating original data If i=0, then the successor of the digital asset who inherits the data and may process the data is i+1. P is the number of all owners who form the digital asset process.
[0035] The credit authorization conditions are Y...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com