Internet threat monitoring and defending method based on dynamic joint defense
A technology of dynamic joint defense and dynamic defense, applied in the field of network security, can solve the problems of heavy workload, high labor cost, misoperation, etc., and achieve the effect of preventing threat attacks and avoiding omissions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
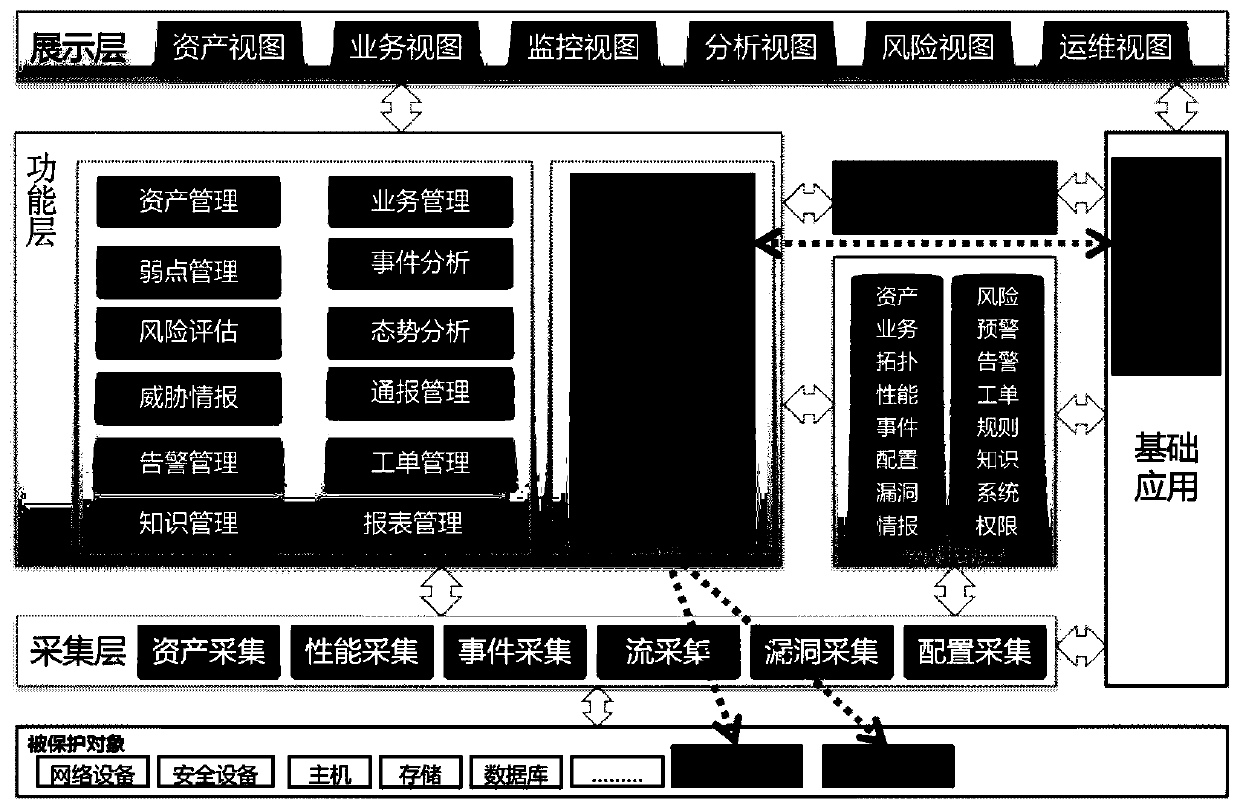
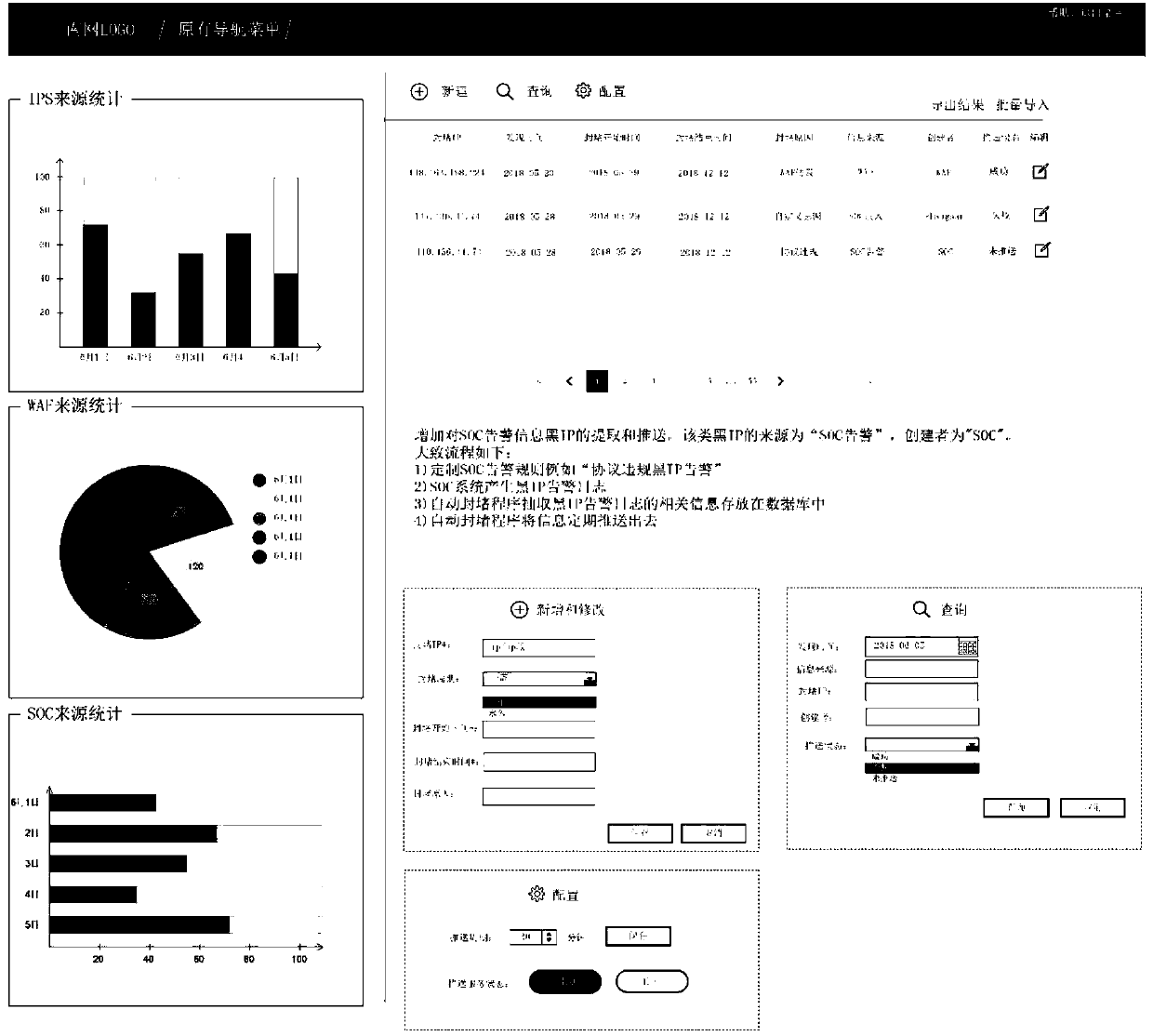
[0031] The method of the present invention is applied in the existing safety monitoring platform, the existing safety monitoring platform such as figure 1 Schematic diagram of functional modules, including display layer, functional layer, application extension layer, data layer, and data acquisition module. Among them, the function layer is provided with the new automatic blocking module of the present invention, and the real-time operation of the automatic blocking module is displayed through the display layer, such as figure 2 As shown, the interface display of the automatic blocking module provides operators with man-machine interface operation input interface, and provides IPS source statistical display, WAF source statistical display and SOC source statistical display, and the statistical source is consistent with IPS, WAF and SOC systems Number of black names.
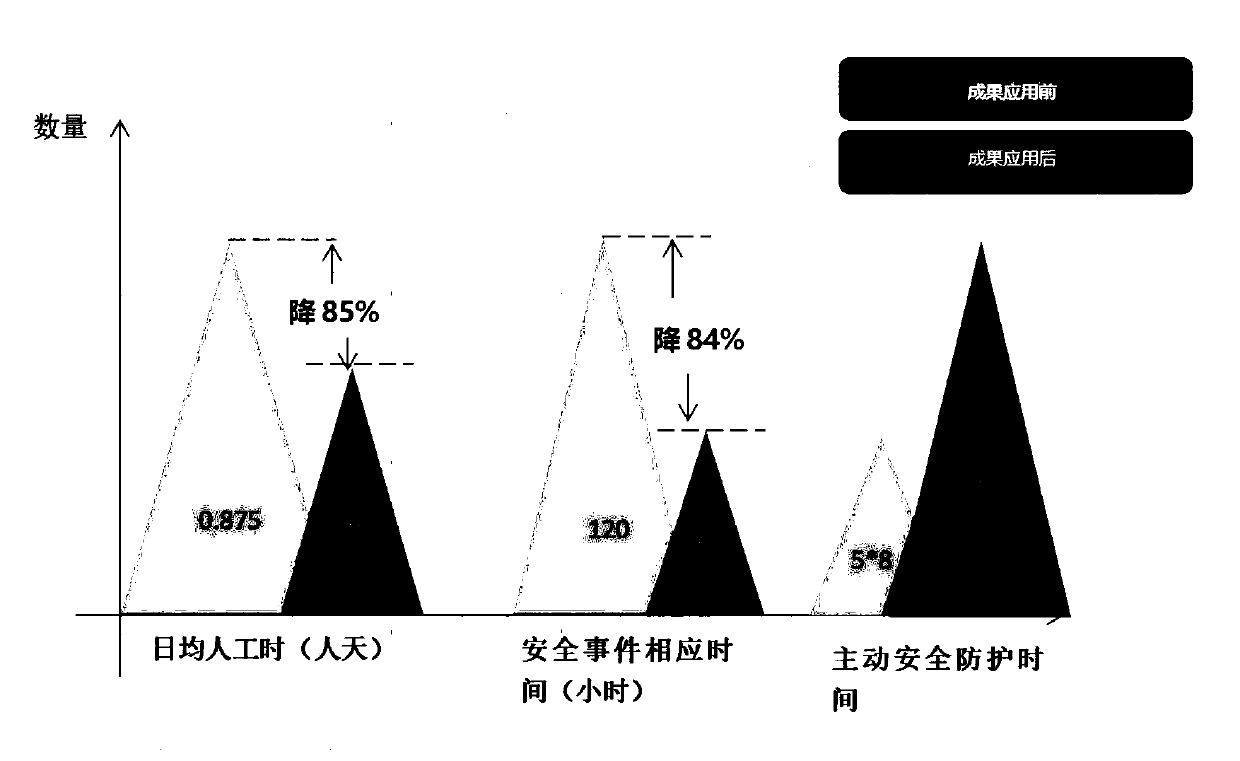
[0032] Add a dynamic defense module to the existing security monitoring platform, and the dynamic defense mo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com