Security Risk Assessment Method of Assets in Network Based on Game Theory
A technology of security risk and game theory, applied in the field of security risk assessment of assets in the network, to achieve the effect of simple method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
[0191] This embodiment illustrates the method of the present invention through an embodiment.
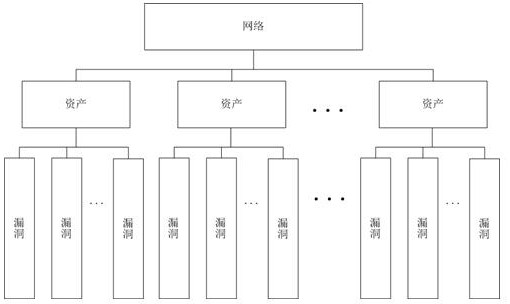
[0192] In this embodiment, there is a host computer equipped with necessary and commonly used software, including operating system, word processing software, web browser and instant messaging software, and 10 vulnerabilities are found by manual and vulnerability scanning tools, as shown in Figure 5 .
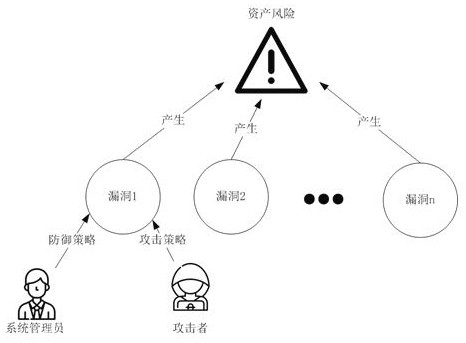
[0193] 3 vulnerabilities were found in the operating system, 3 vulnerabilities were found in the word processing software, 2 vulnerabilities were found in the web browser, and 2 vulnerabilities were found in the instant messaging software. The cost of a vulnerability is a real number in the interval (0,1), the loss of a successful attack is the product of a real number in the interval (1,2) and the cost of focusing on the vulnerability, and the profit of a successful attack is in the interval (1,2) The product of the real number between and the cost of attacking the vulnerability, t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com