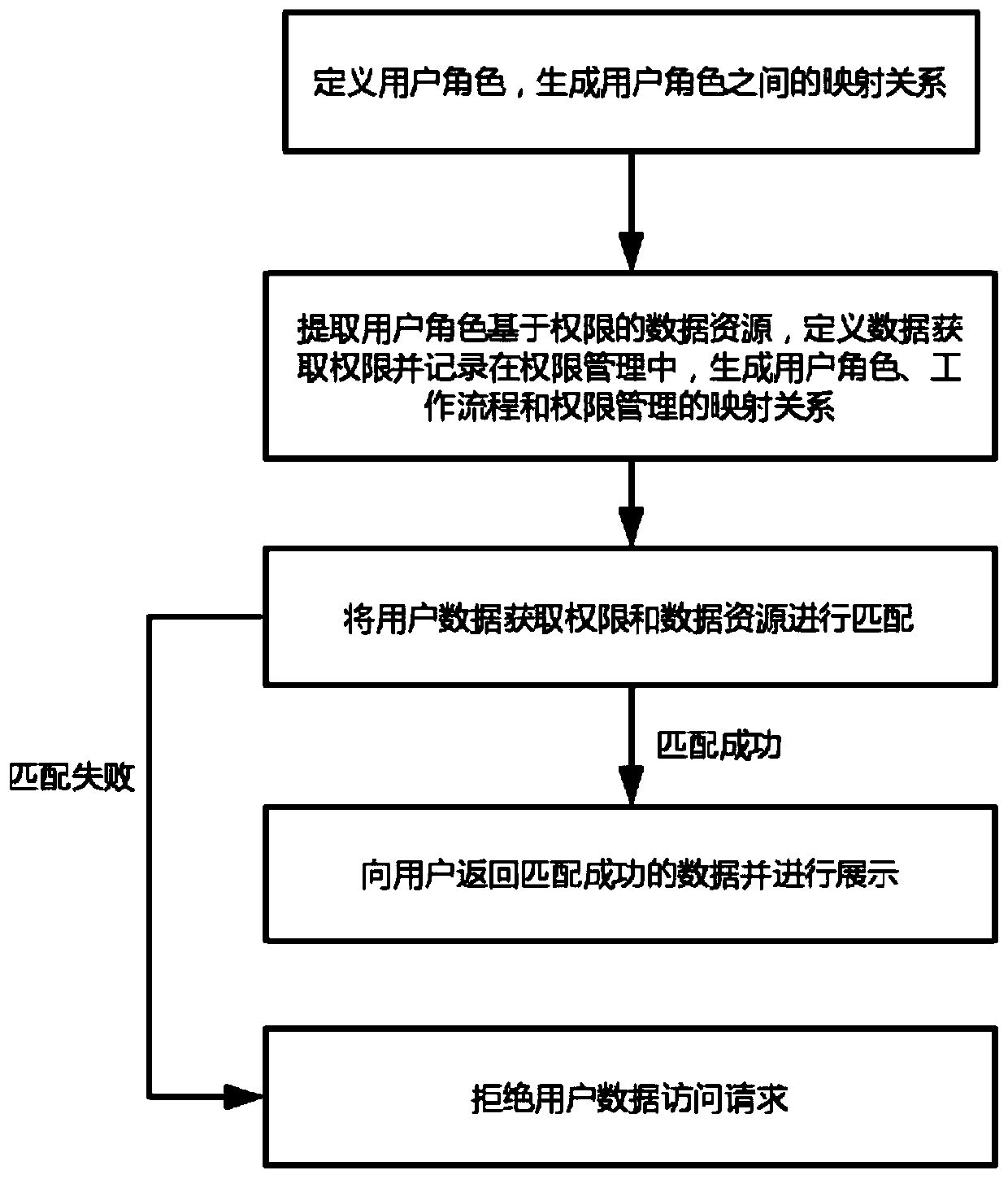
Authority verification method based on user management
A technology of user management and verification method, which is applied in the direction of digital data authentication, etc., can solve the problems that platform administrators cannot manage tenant business, and achieve the effects of improving data visualization, reducing system management complexity, and increasing uniqueness and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
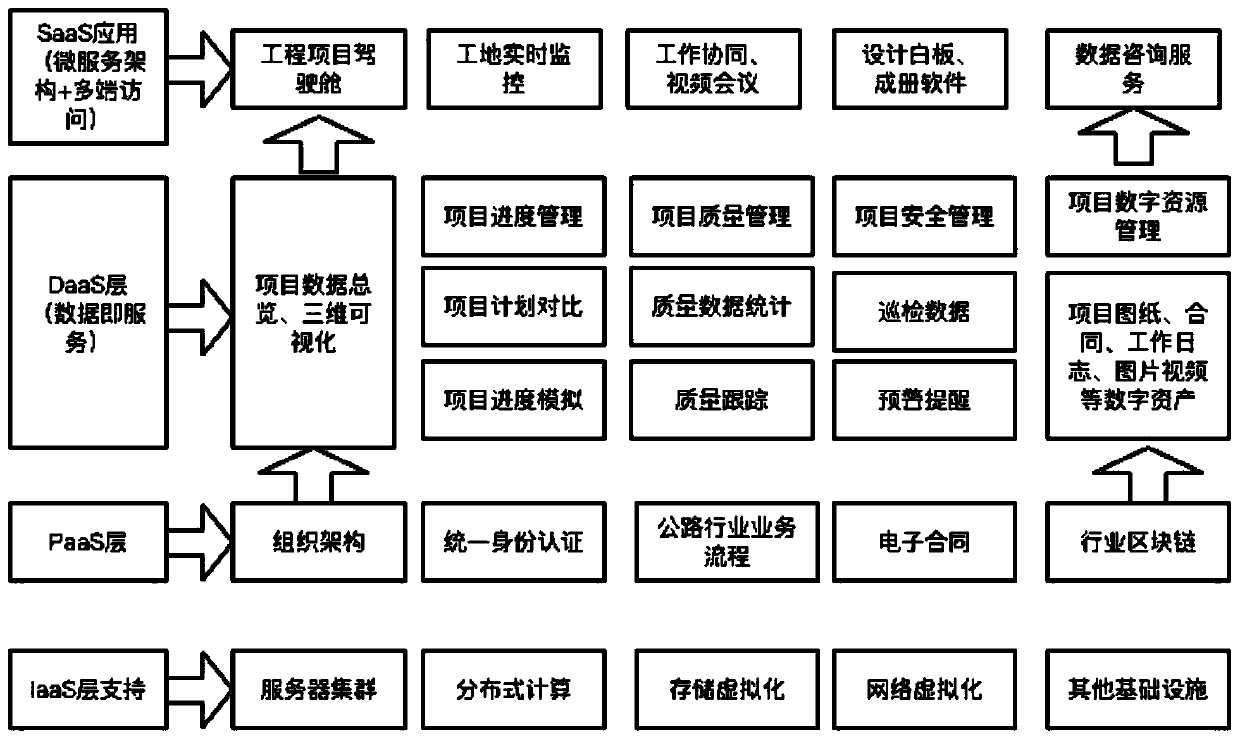
[0055] see figure 2, the present invention supports the operating environment for the operation of the entire system through the underlying support of IaaS, uses server clusters as data storage, and uses technologies such as storage virtualization and network virtualization to realize ultra-large-scale data storage; and has good access control, Features such as load balancing, storage expansion, and disaster recovery, as well as configurable and custom features; and applications that support multi-tenant and multi-user roles.
[0056] Based on the services of the PaaS layer, the processes and components required by the service model of the system are constructed, and the business process services in the field of traffic engineering are constructed through the combination of micro-services, so as to realize the rapid connection of tools and data display.
[0057] Service components in this architecture include:
[0058] Cloud storage components: use virtualization and other t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com