Artificial intelligence processor security enhancement system and method based on key path encryption
An artificial intelligence, critical path technology, applied in key distribution, to achieve the effect of large market benefits, good application prospects, and security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be described in detail below in conjunction with the accompanying drawings and embodiments.
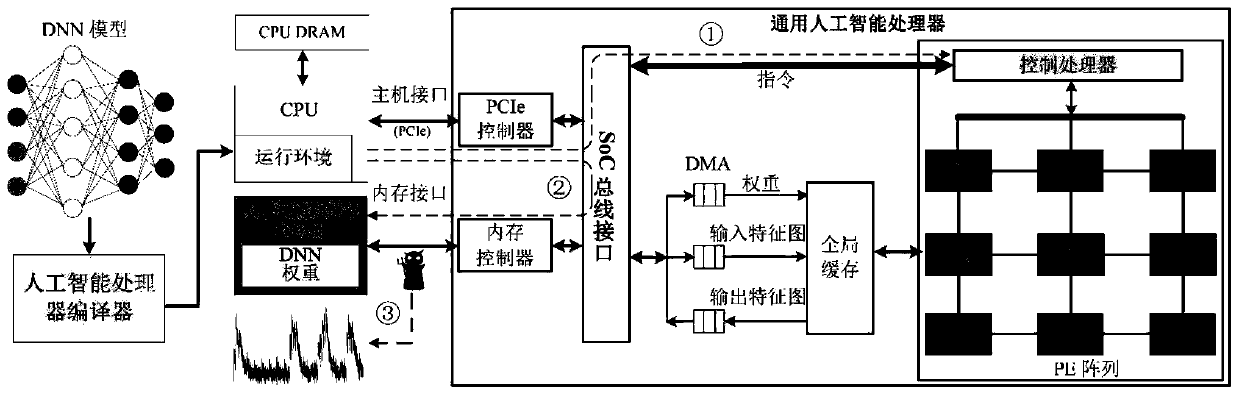
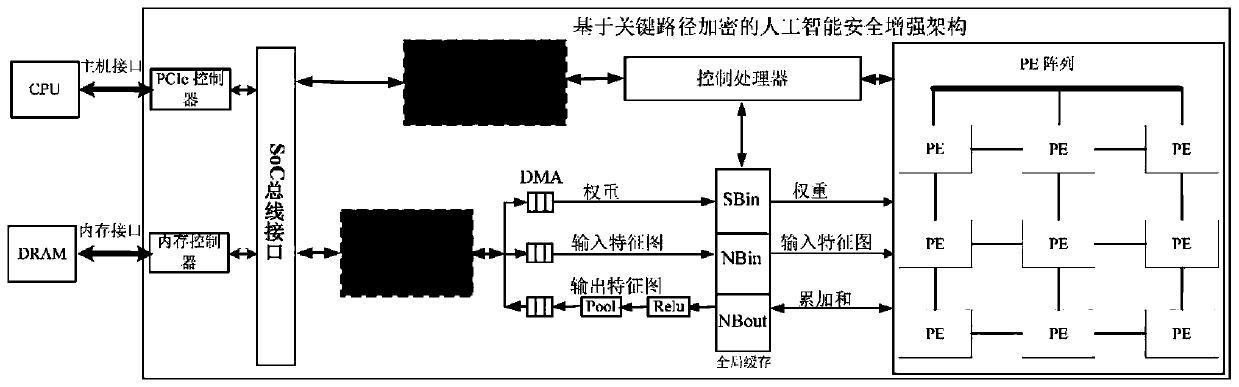
[0036] General artificial intelligence processor system application architecture such as figure 1 As shown, it is mainly composed of a neural network model, an accelerator compiler, a CPU (including the accelerator's operating environment), an off-chip DRAM of the accelerator, and an artificial intelligence processor. For neural network models trained on deep learning platforms such as TensorFlow, Keras, Caffe, and PyTorch, the compiler of the accelerator is used to generate the operating instruction file of the artificial intelligence processor corresponding to the neural network model. The CPU encrypts the instruction file and weight data generated by the compiler, and then parses out the encrypted instructions of each layer of the neural network through the operating environment and sends them to the artificial intelligence processor for execution....
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com