Identity authentication system implementation method based on a quantum key distribution technology
A quantum key distribution and quantum key technology, which is applied in the fields of quantum cryptography and Internet user identity authentication and trust, can solve problems such as abnormality and inability to modify signatures, and achieves an increase in the number of key updates, and the difficulty of key cracking. safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
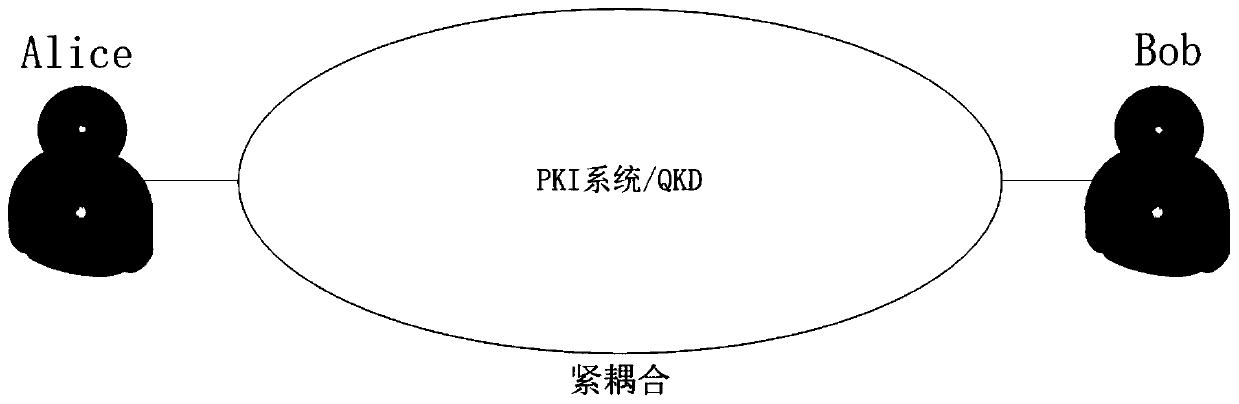
[0046] The case where the public key infrastructure system (PKI) and the quantum key distribution (QKD) are tightly coupled, this embodiment includes two end users Alice (initiator) and Bob (responder), and the quantum keys they belong to Management terminal. This embodiment will provide a method of using the quantum key as the session key in the communication between the two users. The method includes two assumptions: Assumption 1: All users can use quantum channels, regardless of the photon energy Attenuation in the transmission case. Assumption 2: Do not consider destructive attacks such as denial of service attacks. The method includes:
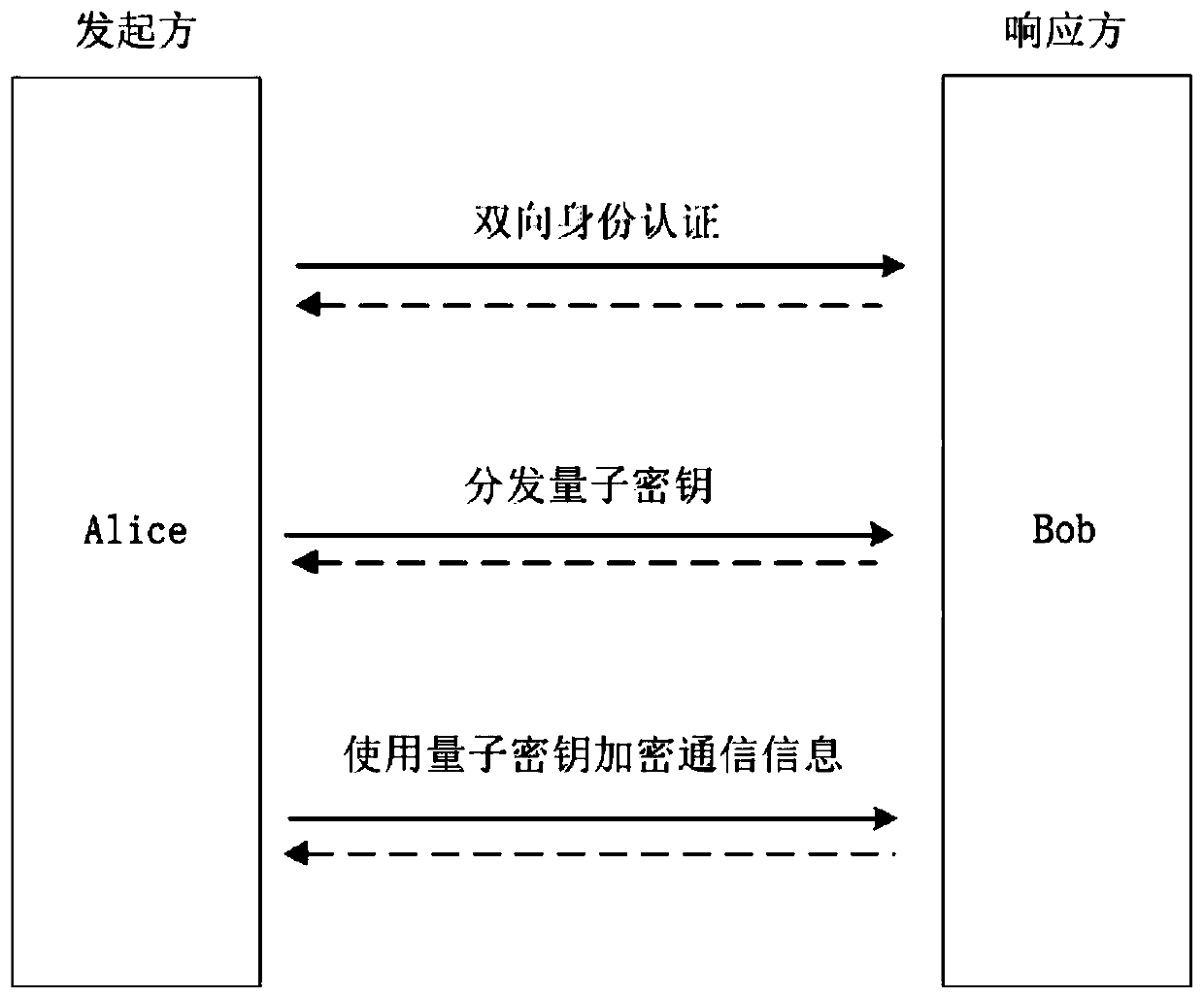
[0047] Step 1. Alice and Bob perform two-way authentication.
[0048] Step 2. If the two-way authentication of Alice and Bob passes, the two parties exchange the parameters required to distribute the quantum key, and then start the distribution of the quantum key.
[0049] Step 3. After Alice and Bob obtain the quantum key, they adjus...
Embodiment 2
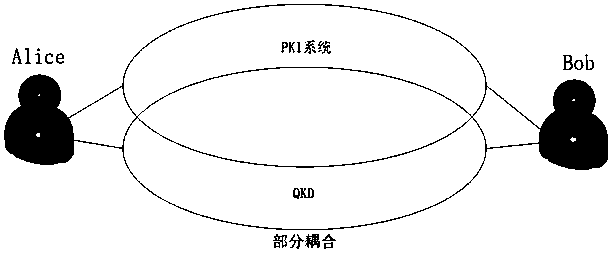
[0055] Communication between users in different trust domains in the case of a partially coupled structure. This embodiment includes two end users Alice (initiator) and Bob (responder), and digital certificate certification authorities QCA1 and QCA2 using quantum keys. QCA nodes have quantum key management terminals, QCA nodes use quantum channels for communication, and general user nodes can only use classical channels for communication. This embodiment provides a method for using a quantum key as a session key in two-way communication between users. The method is based on two assumptions: Assumption 1: The attenuation of photon energy in the case of long-distance transmission is not considered; Assumption 2: Rejection is not considered Destructive attacks such as service attacks. The method includes:
[0056] Step 1. The active communication party Alice and QCA1 perform two-way verification to prove their identities to each other.
[0057] Step 2. QCA1 and QCA2 perform au...
Embodiment 3
[0073] In the case of a partially coupled structure, communication between users within the same trust domain. This embodiment includes two end users Alice (initiator) and Bob (responder), and a digital certificate certification authority QCA using quantum keys. QCA nodes have quantum key management terminals, and general user nodes use classical channels for communication. This embodiment provides a method for using a quantum key as a session key in communication between two users. This method is based on an assumption that destructive attacks such as denial of service attacks are not considered. The method includes:
[0074] Step 1. Alice, the active communication party, and QCA conduct two-way verification to prove their identities to each other.
[0075] Step 2. QCA sends Alice's communication request to Bob, and at the same time conducts two-way identity authentication with Bob.
[0076] Step 3. If the above steps are all successful, it means that the authentication i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com