Distributed Trusted Memory Exchange Method and System
A distributed and trusted technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve the problems of complex use, hidden dangers, easy information leakage, etc., and achieve the effect of increasing system performance and increasing security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0077] The present invention will be described in further detail below with reference to the accompanying drawings and specific embodiments.
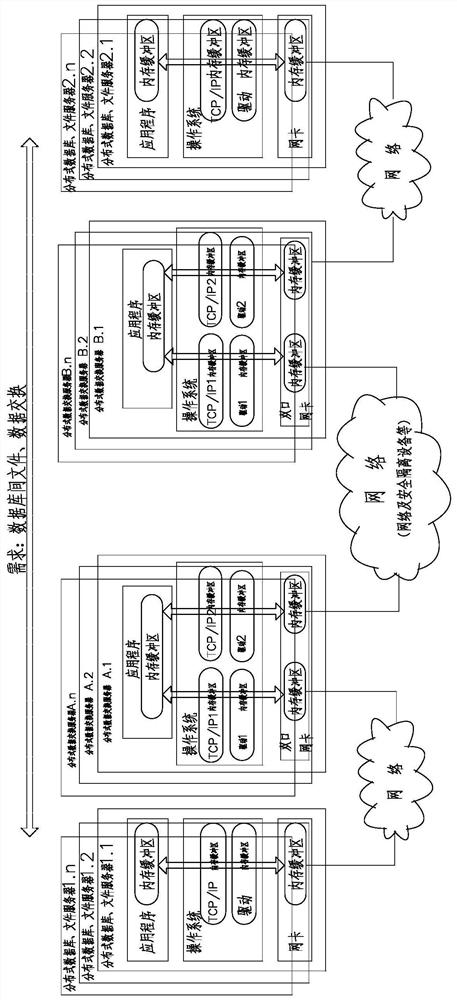
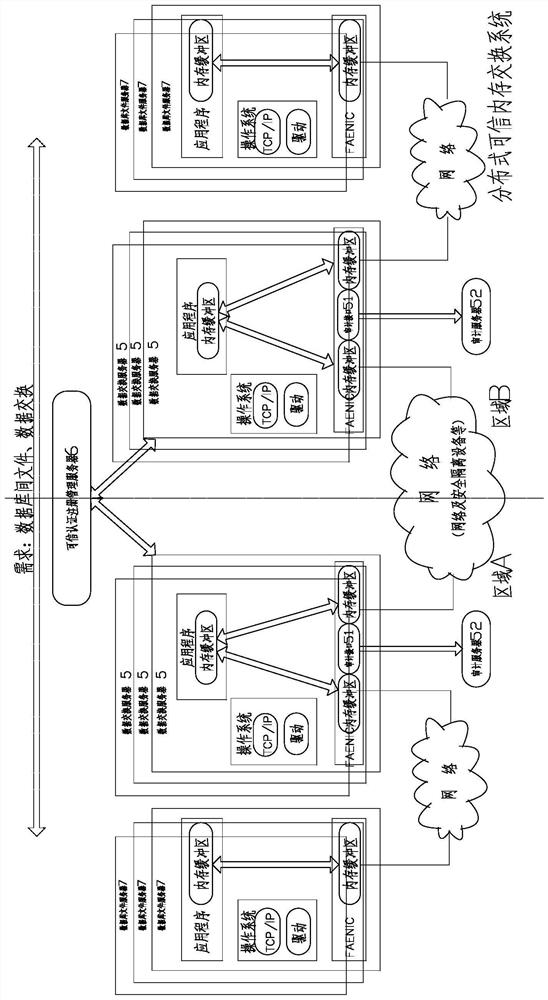
[0078] like Figure 2-3 As shown, this distributed trusted memory switching method includes the following steps:
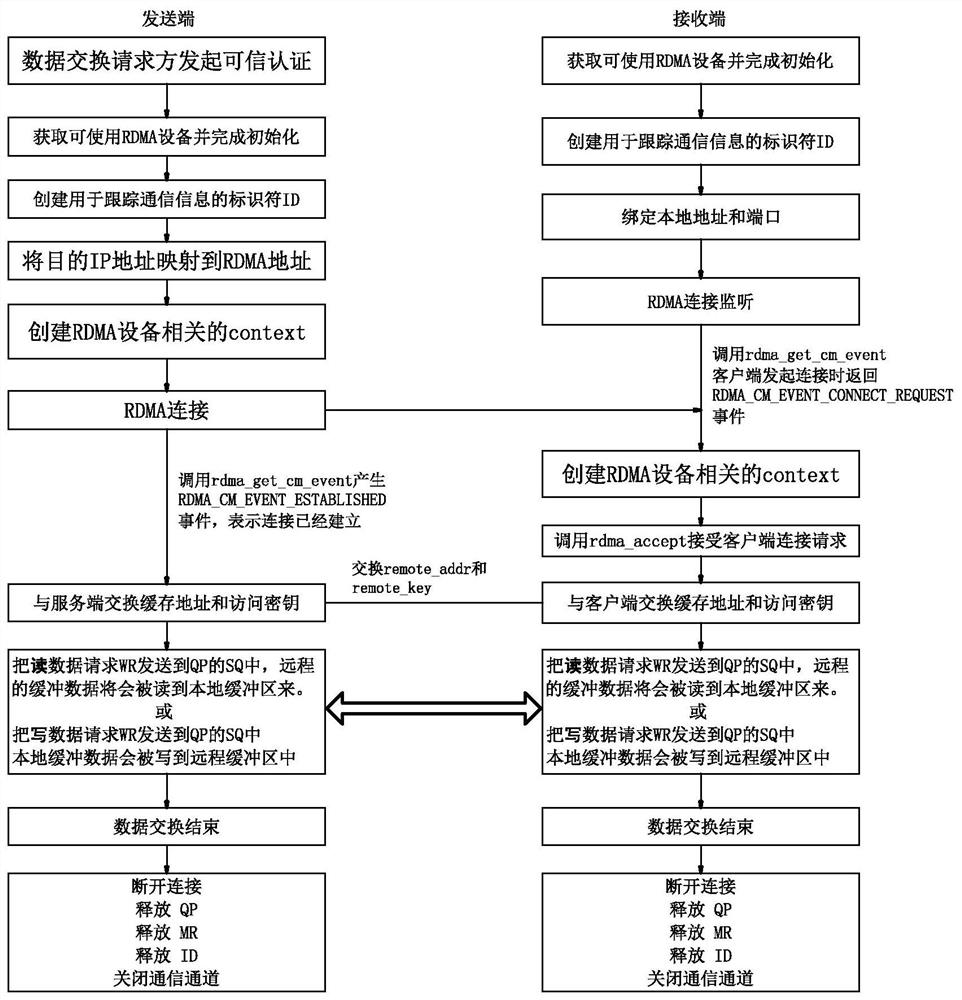
[0079] S1: The data exchange request party of the sender issues a data request, and the transmitting data exchange server 5 performs trusted authentication by the credit authentication registration management server 6.
[0080] S2: The data switching server 5 of the transmitting end and / or receiving end uses a remote direct memory access RDMA method to read data to the database file server 7, and the transmitting end data switching server 5 and the data exchange server 5 of the receiving end use remote direct memory. Access the RDMA method for data exchange.
[0081]The present invention first adopts a new technique to reduce data exchange to the server's CPU resource consumption, to maximize the data exchange performance of a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com